Difficulty (easy)
This challenge starts off with downloading an APK file.

After downloading the file, I decided to extract it with apktool.
An APK file is a glorified ZIP file, some can just be unzipped but others APKs have been obfuscated, so there is where apktool comes to the rescue.
$ apktool d thermostat.apk
-rw-r--r-- 1 triki triki 1263 Mar 9 17:19 AndroidManifest.xml
drwxr-xr-x 136 triki triki 4096 Mar 9 17:19 res
drwxr-xr-x 6 triki triki 4096 Mar 9 17:19 smali
drwxr-xr-x 3 triki triki 4096 Mar 9 17:19 original
-rw-r--r-- 1 triki triki 9099 Mar 9 17:19 apktool.yml
triki@kalima:~/Downloads/tmp/thermostat » grep -r '\^FLAG\^' *
smali/com/hacker101/level11/PayloadRequest.smali: const-string v0, "^FLAG^4299765e023b2ce0b86427fa5c0f4d9a543e444525529b3739da63f0c19c2aca$FLAG$"
smali/com/hacker101/level11/PayloadRequest.smali: const-string v0, "^FLAG^856cd8bfe1105b9464115b1888982bfe35bd1d99aa3ff84f46b270f7a16a3810$FLAG$"
But let's go through this properly.
The Hints for these flags are:
Flag0 -- Found
Communication is key
Have you looked at what the app is sending to the server?
Flag1 -- Found
Doesn't the MAC seem interesting?
Access to the source code would help
Check out the Android Quickstart video from Hacker101
I loaded this APK into Android Studio Emulator for to see what this app is all about.
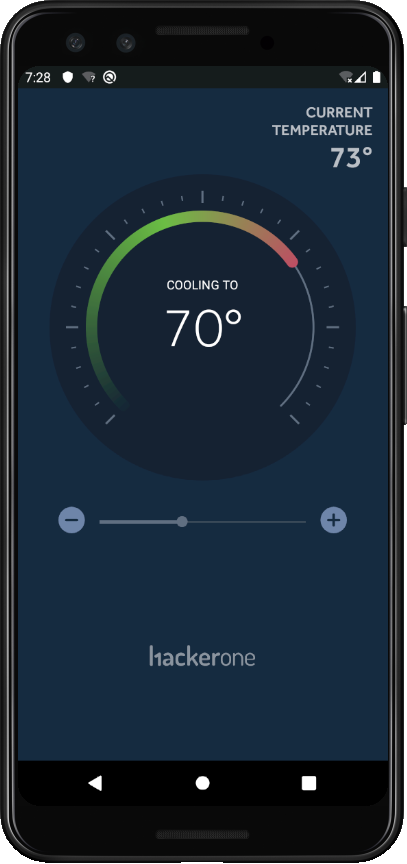
Next I set the emulator to use my local burp proxy to capture traffic.
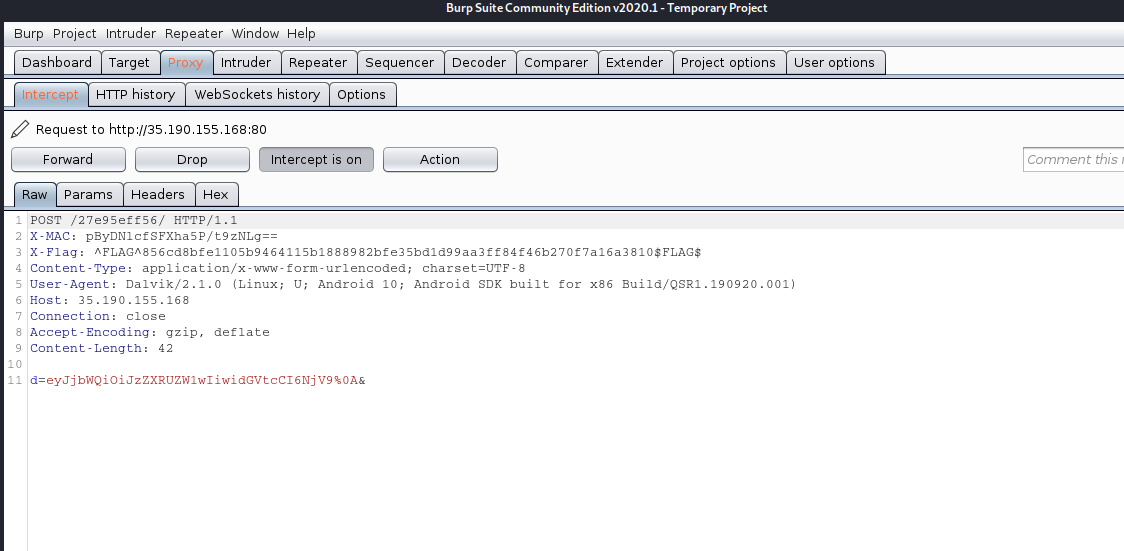
FLAG #0 done.
Looking at the http request captured I notice the X-MAC has a base64 encoded string. Decoding this gave me the following:
echo 'pByDNlcfSFXha5P/t9zNLg==' | base64 -d
6WHUk.%
When I grep for 'X-MAC' it appears in a file called 'PayloadRequest.smali'. Looking through that file for X-MAC I find the other FLAG.
FLAG #1 done.